The Pronk Pops Show 188, January 8, 2014, Story 1: Instant Tyranny of The National Security Agency — Trust Us We Will Not Target You, Unless Ordered To By Presidential Tyrants That Puts You On Our Enemies Lists — Abuse of Power — Video
Posted on January 8, 2014. Filed under: Addiction, American History, Applications, Blogroll, Books, Budgetary Policy, Business, Coal, Coal, Communications, Computers, Constitutional Law, Crime, Culture, Economics, Education, Employment, Energy, Federal Government, Fiscal Policy, Foreign Policy, Gangs, Government, Government Dependency, Government Spending, Hardware, History, Law, Media, Movies, Natural Gas, Natural Gas, Networking, Nuclear, Oil, Oil, Philosophy, Photos, Politics, Public Sector Unions, Radio, Resources, Scandals, Security, Social Science, Software, Success, Tax Policy, Taxes, Technology, Unemployment, Unions, United States Constitution, Videos, Violence, War, Wealth, Wisdom | Tags: 1984, Abolish The Fed, Abuse of Power, Barack H. Obama, Big Brother, Bill Binney, Boundless Informant, Corruption, Culture, DCSNet, Eagle Eye, ECHELON, Edward Snowden, Enemies List, Enemy of The State, FBI, Federal Bureau of Investigation, George W. Bush, Instant Tyranny, Invasion of Privacy, James Bamford, LBJ, Lives of Others, Lyndon B. Johnson, Magic Lantern, Main Core, Movies, National Security Agency, NSA, Police State, Power, Presidents, PRISM, Privacy Protection, Richard M. Nixon, Room 641A, Russ Tice, Spying, Stasi Files, Stellar Wind, Tailored Access Operations, The Surveillance State, ThinThread, Thomas Drake, THX 1138, Trailblazer, Tyrants, U.S. Constitution, Whistleblowers, XKeyscore |
The Pronk Pops Show Podcasts
Pronk Pops Show 188: January 8, 2014
Pronk Pops Show 187: January 7, 2014
Pronk Pops Show 186: January 6, 2014
Pronk Pops Show 185: January 3, 2014
Pronk Pops Show 184: December 19, 2013
Pronk Pops Show 183: December 17, 2013
Pronk Pops Show 182: December 16, 2013
Pronk Pops Show 181: December 13, 2013
Pronk Pops Show 180: December 12, 2013
Pronk Pops Show 179: December 11, 2013
Pronk Pops Show 178: December 5, 2013
Pronk Pops Show 177: December 2, 2013
Pronk Pops Show 176: November 27, 2013
Pronk Pops Show 175: November 26, 2013
Pronk Pops Show 174: November 25, 2013
Pronk Pops Show 173: November 22, 2013
Pronk Pops Show 172: November 21, 2013
Pronk Pops Show 171: November 20, 2013
Pronk Pops Show 170: November 19, 2013
Pronk Pops Show 169: November 18, 2013
Pronk Pops Show 168: November 15, 2013
Pronk Pops Show 167: November 14, 2013
Pronk Pops Show 166: November 13, 2013
Pronk Pops Show 165: November 12, 2013
Pronk Pops Show 164: November 11, 2013
Pronk Pops Show 163: November 8, 2013
Pronk Pops Show 162: November 7, 2013
Pronk Pops Show 161: November 4, 2013
Pronk Pops Show 160: November 1, 2013
Pronk Pops Show 159: October 31, 2013
Pronk Pops Show 158: October 30, 2013
Pronk Pops Show 157: October 28, 2013
Pronk Pops Show 156: October 25, 2013
Pronk Pops Show 155: October 24, 2013
Pronk Pops Show 154: October 23, 2013
Pronk Pops Show 153: October 21, 2013
Pronk Pops Show 152: October 18, 2013
Pronk Pops Show 151: October 17, 2013
Pronk Pops Show 150: October 16, 2013
Pronk Pops Show 149: October 14, 2013
Pronk Pops Show 148: October 11, 2013
Pronk Pops Show 147: October 10, 2013
Pronk Pops Show 146: October 9, 2013
Pronk Pops Show 145: October 8, 2013
Pronk Pops Show 144: October 7, 2013
Pronk Pops Show 143: October 4 2013
Pronk Pops Show 142: October 3, 2013
Pronk Pops Show 141: October 2, 2013
The Pronk Pops Show Podcasts Portfolio
Listen To Pronk Pops Podcast or Download Show 184-188
Listen To Pronk Pops Podcast or Download Show 174-183
Listen To Pronk Pops Podcast or Download Show 165-173
Listen To Pronk Pops Podcast or Download Show 158-164
Listen To Pronk Pops Podcast or Download Show 151-157
Listen To Pronk Pops Podcast or Download Show 143-150
Listen To Pronk Pops Podcast or Download Show 135-142
Listen To Pronk Pops Podcast or Download Show 131-134
Listen To Pronk Pops Podcast or Download Show 124-130
Listen To Pronk Pops Podcast or Download Shows 121-123
Listen To Pronk Pops Podcast or Download Shows 118-120
Listen To Pronk Pops Podcast or Download Shows 113 -117
Listen To Pronk Pops Podcast or Download Show 112
Listen To Pronk Pops Podcast or Download Shows 108-111
Listen To Pronk Pops Podcast or Download Shows 106-108
Listen To Pronk Pops Podcast or Download Shows 104-105
Listen To Pronk Pops Podcast or Download Shows 101-103
Listen To Pronk Pops Podcast or Download Shows 98-100
Listen To Pronk Pops Podcast or Download Shows 94-97
Listen To Pronk Pops Podcast or Download Shows 93
Listen To Pronk Pops Podcast or Download Shows 92
Listen To Pronk Pops Podcast or Download Shows 91
Listen To Pronk Pops Podcast or Download Shows 88-90
Listen To Pronk Pops Podcast or Download Shows 84-87
Listen To Pronk Pops Podcast or Download Shows 79-83
Listen To Pronk Pops Podcast or Download Shows 74-78
Listen To Pronk Pops Podcast or Download Shows 71-73
Listen To Pronk Pops Podcast or Download Shows 68-70
Listen To Pronk Pops Podcast or Download Shows 65-67
Listen To Pronk Pops Podcast or Download Shows 62-64
Listen To Pronk Pops Podcast or Download Shows 58-61
Listen To Pronk Pops Podcast or Download Shows 55-57
Listen To Pronk Pops Podcast or Download Shows 52-54
Listen To Pronk Pops Podcast or Download Shows 49-51
Listen To Pronk Pops Podcast or Download Shows 45-48
Listen To Pronk Pops Podcast or Download Shows 41-44
Listen To Pronk Pops Podcast or Download Shows 38-40
Listen To Pronk Pops Podcast or Download Shows 34-37
Listen To Pronk Pops Podcast or Download Shows 30-33
Listen To Pronk Pops Podcast or Download Shows 27-29
Listen To Pronk Pops Podcast or Download Shows 17-26
Listen To Pronk Pops Podcast or Download Shows 16-22
Listen To Pronk Pops Podcast or Download Shows 10-15
Listen To Pronk Pops Podcast or Download Shows 01-09
Story 1: Instant Tyranny of The National Security Agency — Trust Us We Will Not Target You, Unless Ordered To By Presidential Tyrants That Puts You On Our Enemies Lists — Abuse of Power — Video
Watch This 15 Year Old Movie First and Remember
This Was Before September 11, 2001
Technology and Software Have Advanced
Enemy Of The State 1998 (1080p) (Full movie)
Greenwald: Snowden Has NSA Blueprint
FOX NEWS: Edward Snowden & the Surveillance State
“They’re Collecting EVERYTHING! Content Word For Word EVERYTHING!” Russell Tice Fmr NSA Agent
NSA Whistleblower: Everyone in US under virtual surveillance, all info stored, no matter the post
He told you so: Bill Binney talks NSA leaks
NSA Blackmailing Obama? | Interview with Whistleblower Russ Tice
NSA Whistleblower Russ Tice Alleges NSA Wiretapped Barack Obama as Senate Candidate
Glenn Becks “SURVEILLANCE STATE”
Anonymous – More Info On The NSA
NSA Questioned about Congressional Spying
NSA Spying Program FAR More Massive Than Snowden Originally Told Us
Reclaiming Our Rights in the 21st Century (Sen. Rand Paul)
Rand Paul brings class action lawsuit against NSA
The NSA’s Data Grab: Keeping Us Safe – Or Invading Our Privacy?
‘This Week’ Roundtable: Snowden Vindicated?
Give Edward Snowden Clemency!
Enemy of the State (1998) Predicts Edward Snowden’s Revelations
More Movies and Documentaries To Watch
Closed Circuit – Official Trailer
Eagle Eye
Leverage–Shut Up–Or Else
Enemies of the State
Stalisland – Germany
Stasi Files: The Lives of Others | Journal Reporter
The Lives of Others trailer
The Lives Of Others
The Making of THX 1138
THX 1138 Mindlock
Orwell’s 1984 (1956)
Through a PRISM, Darkly – Everything we know about NSA spying [30c3]
Published on Dec 30, 2013
Through a PRISM, Darkly
Everything we know about NSA spying
From Stellar Wind to PRISM, Boundless Informant to EvilOlive, the NSA spying programs are shrouded in secrecy and rubber-stamped by secret opinions from a court that meets in a faraday cage. The Electronic Frontier Foundation’s Kurt Opsahl explains the known facts about how the programs operate and the laws and regulations the U.S. government asserts allows the NSA to spy on you.
The Electronic Frontier Foundation, a non-profit civil society organization, has been litigating against the NSA spying program for the better part of a decade. EFF has collected and reviewed dozens of documents, from the original NY Times stories in 2005 and the first AT&T whistleblower in 2006, through the latest documents released in the Guardian or obtained through EFF’s Freedom of Information (government transparency) litigation. EFF attorney Kurt Opsahl’s lecture will describe how the NSA spying program works, the underlying technologies, the targeting procedures (how they decide who to focus on), the minimization procedures (how they decide which information to discard), and help you makes sense of the many code names and acronyms in the news. He will also discuss the legal and policy ramifications that have become part of the public debate following the recent disclosures, and what you can do about it. After summarizing the programs, technologies, and legal/policy framework in the lecture, the audience can ask questions.
Speaker: Kurt Opsahl
EventID: 5255
Event: 30th Chaos Communication Congress [30c3] by the Chaos Computer Club [CCC]
Location: Congress Centrum Hamburg (CCH); Am Dammtor; Marseiller Straße; 20355 Hamburg; Germany
Language: english
Glenn Becks “SURVEILLANCE STATE”
Inside the NSA
Ed Snowden, NSA, and Fairy Tales
AT&T Spying On Internet Traffic
For years the National Securities Agency, has been spying on each & every keystroke. The national headquarters of AT&T is in Missouri, where ex-employees describe a secret room. The program is called “Splitter Cut-In & Test Procedure.”
NSA Whistle-Blower Tells All – Op-Docs: The Program
The filmmaker Laura Poitras profiles William Binney, a 32-year veteran of the National Security Agency who helped design a top-secret program he says is broadly collecting Americans’ personal data.
NSA Whistleblower: Everyone in US under virtual surveillance, all info stored, no matter the post
He told you so: Bill Binney talks NSA leaks
William Benny – The Government is Profiling You (The NSA is Spying on You)
‘After 9/11 NSA had secret deal with White House’
The story of Whistleblower Thomas Drake
Whistleblowers, Part Two: Thomas Drake
NSA Whistleblower Thomas Drake speaks at National Press Club – March 15, 2013
Meet Edward Snowden: NSA PRISM Whistleblower
The Truth About Edward Snowden
N.S.A. Spying: Why Does It Matter?
Inside The NSA~Americas Cyber Secrets
NSA Whistleblower Exposes Obama’s Dragnet
AT&T whistleblower against immunity for Bush spy program-1/2
AT&T Whistleblower Urges Against Immunity for Telecoms in Bush Spy Program
The Senate is expected to vote on a controversial measure to amend the Foreign Intelligence Surveillance Act tomorrow. The legislation would rewrite the nation’s surveillance laws and authorize the National Security Agency’s secret program of warrantless wiretapping. We speak with Mark Klein, a technician with AT&T for over twenty-two years. In 2006 Klein leaked internal AT&T documents that revealed the company had set up a secret room in its San Francisco office to give the National Security Agency access to its fiber optic internet cables.
AT&T whistleblower against immunity for Bush spy program-2/2
Enemy Of The State 1998 (1080p) (Full movie)
Background Articles and Videos
Stellar Wind
Stellar Wind was the open secret code name for four surveillance programs by the United States National Security Agency (NSA) during the presidency of George W. Bush and revealed by Thomas Tamm to The New York Times reporters James Risen and Eric Lichtblau.[1] The operation was approved by President George W. Bush shortly after the September 11 attacks in 2001.[2] Stellar Wind was succeeded during the presidency of Barack Obama by four major lines of intelligence collection in the territorial United States, together capable of spanning the full range of modern telecommunications.[3]
The program’s activities involved data mining of a large database of the communications of American citizens, including e-mail communications, phone conversations, financial transactions, and Internet activity.[1] William Binney, a retired Technical Leader with the NSA, discussed some of the architectural and operational elements of the program at the 2012 Chaos Communication Congress.[4]
There were internal disputes within the Justice Department about the legality of the program, because data are collected for large numbers of people, not just the subjects of Foreign Intelligence Surveillance Act (FISA) warrants.[4]
During the Bush Administration, the Stellar Wind cases were referred to by FBI agents as “pizza cases” because many seemingly suspicious cases turned out to be food takeout orders. According to Mueller, approximately 99 percent of the cases led nowhere, but “it’s that other 1% that we’ve got to be concerned about”.[2] One of the known uses of these data were the creation of suspicious activity reports, or “SARS”, about people suspected of terrorist activities. It was one of these reports that revealed former New York governor Eliot Spitzer’s use of prostitutes, even though he was not suspected of terrorist activities.[1]
In March 2012 Wired magazine published “The NSA Is Building the Country’s Biggest Spy Center (Watch What You Say)” talking about a vast new NSA facility in Utah and says “For the first time, a former NSA official has gone on the record to describe the program, codenamed Stellar Wind, in detail,” naming the official William Binney, a former NSA code breaker. Binney went on to say that the NSA had highly secured rooms that tap into major switches, and satellite communications at both AT&T and Verizon.[5] The article suggested that the otherwise dispatched Stellar Wind is actually an active program.
http://en.wikipedia.org/wiki/Stellar_Wind_%28code_name%29
PRISM
PRISM is a clandestine national security electronic surveillance program operated by the United States National Security Agency (NSA) since 2007.[1][2][3][Notes 1] PRISM is a government codename for a data collection effort known officially as US-984XN.[8][9] It is operated under the supervision of the United States Foreign Intelligence Surveillance Court pursuant to the Foreign Intelligence Surveillance Act (FISA).[10] The existence of the program was leaked by NSA contractor Edward Snowden and published by The Guardian and The Washington Post on June 6, 2013.
A document included in the leak indicated that the PRISM SIGAD was “the number one source of raw intelligence used for NSA analytic reports.”[11] The President’s Daily Brief, an all-source intelligence product, cited PRISM data as a source in 1,477 items in 2012.[12] The leaked information came to light one day after the revelation that the United States Foreign Intelligence Surveillance Court had been requiring the telecommunications company Verizon to turn over to the NSA logs tracking all of its customers’ telephone calls on an ongoing daily basis.[13][14]
According to the Director of National Intelligence James Clapper, PRISM cannot be used to intentionally target any Americans or anyone in the United States. Clapper said a special court, Congress, and the executive branch oversee the program and extensive procedures ensure the acquisition, retention, and dissemination of data accidentally collected about Americans is kept to a minimum.[15] Clapper issued a statement and “fact sheet”[16] to correct what he characterized as “significant misimpressions” in articles by The Washington Post and The Guardian newspapers.[17]
History
PRISM is a “Special Source Operation” in the tradition of NSA’s intelligence alliances with as many as 100 trusted U.S. companies since the 1970s.[1] A prior program, the Terrorist Surveillance Program, was implemented in the wake of the September 11 attacks under the George W. Bush Administration but was widely criticized and had its legality questioned, because it was conducted without approval of the Foreign Intelligence Surveillance Court (FISC).[18][19][20][21] PRISM was authorized by an order of the FISC.[11] Its creation was enabled by the Protect America Act of 2007 under President Bush and the FISA Amendments Act of 2008, which legally immunized private companies that cooperated voluntarily with US intelligence collection and was renewed by Congress under President Obama in 2012 for five years until December 2017.[2][22] According to The Register, the FISA Amendments Act of 2008 “specifically authorizes intelligence agencies to monitor the phone, email, and other communications of U.S. citizens for up to a week without obtaining a warrant” when one of the parties is outside the U.S.[22]
PRISM was first publicly revealed on June 6, 2013, after classified documents about the program were leaked to The Washington Post and The Guardian by American Edward Snowden.[2][1] The leaked documents included 41 PowerPoint slides, four of which were published in news articles.[1][2] The documents identified several technology companies as participants in the PRISM program, including (date of joining PRISM in parentheses) Microsoft (2007), Yahoo! (2008), Google (2009), Facebook (2009), Paltalk (2009), YouTube (2010), AOL (2011), Skype (2011), and Apple (2012).[23] The speaker’s notes in the briefing document reviewed by The Washington Post indicated that “98 percent of PRISM production is based on Yahoo, Google and Microsoft.”[1]
The slide presentation stated that much of the world’s electronic communications pass through the United States, because electronic communications data tend to follow the least expensive route rather than the most physically direct route, and the bulk of the world’s internet infrastructure is based in the United States.[11] The presentation noted that these facts provide United States intelligence analysts with opportunities for intercepting the communications of foreign targets as their electronic data pass into or through the United States.[2][11]
According to The Washington Post, the intelligence analysts search PRISM data using terms intended to identify suspicious communications of targets whom the analysts suspect with at least 51 percent confidence to not be United States citizens, but in the process, communication data of some United States citizens are also collected unintentionally.[1] Training materials for analysts tell them that while they should periodically report such accidental collection of non-foreign United States data, “it’s nothing to worry about.”[1]
Response from companies
The original Washington Post and Guardian articles reporting on PRISM noted that one of the leaked briefing documents said PRISM involves collection of data “directly from the servers” of several major internet services providers.[2][1]
Initial Public Statements
Corporate executives of several companies identified in the leaked documents told The Guardian that they had no knowledge of the PRISM program in particular and also denied making information available to the government on the scale alleged by news reports.[2][24] Statements of several of the companies named in the leaked documents were reported by TechCrunch and The Washington Post as follows:[25][26]
- Microsoft: “We provide customer data only when we receive a legally binding order or subpoena to do so, and never on a voluntary basis. In addition we only ever comply with orders for requests about specific accounts or identifiers. If the government has a broader voluntary national security program to gather customer data we don’t participate in it.”[25]
- Yahoo!: “Yahoo! takes users’ privacy very seriously. We do not provide the government with direct access to our servers, systems, or network.”[25] “Of the hundreds of millions of users we serve, an infinitesimal percentage will ever be the subject of a government data collection directive.”[26]
- Facebook: “We do not provide any government organization with direct access to Facebook servers. When Facebook is asked for data or information about specific individuals, we carefully scrutinize any such request for compliance with all applicable laws, and provide information only to the extent required by law.”[25]
- Google: “Google cares deeply about the security of our users’ data. We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government ‘back door’ into our systems, but Google does not have a backdoor for the government to access private user data.”[25] “[A]ny suggestion that Google is disclosing information about our users’ Internet activity on such a scale is completely false.”[26]
- Apple: “We have never heard of PRISM. We do not provide any government agency with direct access to our servers, and any government agency requesting customer data must get a court order.”[27]
- Dropbox: “We’ve seen reports that Dropbox might be asked to participate in a government program called PRISM. We are not part of any such program and remain committed to protecting our users’ privacy.”[25]
In response to the technology companies’ denials of the NSA being able to directly access the companies’ servers, The New York Times reported that sources had stated the NSA was gathering the surveillance data from the companies using other technical means in response to court orders for specific sets of data.[13] The Washington Post suggested, “It is possible that the conflict between the PRISM slides and the company spokesmen is the result of imprecision on the part of the NSA author. In another classified report obtained by The Post, the arrangement is described as allowing ‘collection managers [to send] content tasking instructions directly to equipment installed at company-controlled locations,’ rather than directly to company servers.”[1] “[I]n context, ‘direct’ is more likely to mean that the NSA is receiving data sent to them deliberately by the tech companies, as opposed to intercepting communications as they’re transmitted to some other destination.[26]
“If these companies received an order under the FISA amendments act, they are forbidden by law from disclosing having received the order and disclosing any information about the order at all,” Mark Rumold, staff attorney at the Electronic Frontier Foundation, told ABC News.[28]
On May 28, 2013, Google was ordered by United States District Court Judge Susan Illston to comply with a National Security Letter issued by the FBI to provide user data without a warrant.[30] Kurt Opsahl, a senior staff attorney at the Electronic Frontier Foundation, in an interview with VentureBeat said, “I certainly appreciate that Google put out a transparency report, but it appears that the transparency didn’t include this. I wouldn’t be surprised if they were subject to a gag order.”[31]
The New York Times reported on June 7, 2013, that “Twitter declined to make it easier for the government. But other companies were more compliant, according to people briefed on the negotiations.”[32] The other companies held discussions with national security personnel on how to make data available more efficiently and securely.[32] In some cases, these companies made modifications to their systems in support of the intelligence collection effort.[32] The dialogues have continued in recent months, as General Martin Dempsey, the chairman of the Joint Chiefs of Staff, has met with executives including those at Facebook, Microsoft, Google and Intel.[32] These details on the discussions provide insight into the disparity between initial descriptions of the government program including a training slide which states “Collection directly from the servers”[29] and the companies’ denials.[32]
While providing data in response to a legitimate FISA request approved by FISC is a legal requirement, modifying systems to make it easier for the government to collect the data is not. This is why Twitter could legally decline to provide an enhanced mechanism for data transmission.[32] Other than Twitter, the companies were effectively asked to construct a locked mailbox and provide the key to the government, people briefed on the negotiations said.[32] Facebook, for instance, built such a system for requesting and sharing the information.[32] Google does not provide a lockbox system, but instead transmits required data by hand delivery or secure FTP.[33]
Post-PRISM Transparency Reports
In response to the publicity surrounding media reports of data-sharing, several companies requested permission to reveal more public information about the nature and scope of information provided in response to National Security requests.
On June 14, 2013, Facebook reported that the U.S. Government had authorized the communication of “about these numbers in aggregate, and as a range.” In a press release posted to their web site, Facebook reported, “For the six months ending December 31, 2012, the total number of user-data requests Facebook received from any and all government entities in the U.S. (including local, state, and federal, and including criminal and national security-related requests) – was between 9,000 and 10,000.” Facebook further reported that the requests impacted “between 18,000 and 19,000” user accounts, a “tiny fraction of one percent” of more than 1.1 billion active user accounts.[34]
Microsoft reported that for the same period, it received “between 6,000 and 7,000 criminal and national security warrants, subpoenas and orders affecting between 31,000 and 32,000 consumer accounts from U.S. governmental entities (including local, state and federal)” which impacted “a tiny fraction of Microsoft’s global customer base”.[35]
Google issued a statement criticizing the requirement that data be reported in aggregated form, stating that lumping national security requests with criminal request data would be “a step backwards” from its previous, more detailed practices on its site transparency report. The company said that it would continue to seek government permission to publish the number and extent of FISA requests.[36]
Response from United States government
Executive branch
Shortly after publication of the reports by The Guardian and The Washington Post, the United States Director of National Intelligence, James Clapper, on June 7 released a statement confirming that for nearly six years the government of the United States had been using large internet services companies such as Google and Facebook to collect information on foreigners outside the United States as a defense against national security threats.[13] The statement read in part, “The Guardian and The Washington Post articles refer to collection of communications pursuant to Section 702 of the Foreign Intelligence Surveillance Act. They contain numerous inaccuracies.”[37] He went on to say, “Section 702 is a provision of FISA that is designed to facilitate the acquisition of foreign intelligence information concerning non-U.S. persons located outside the United States. It cannot be used to intentionally target any U.S. citizen, any other U.S. person, or anyone located within the United States.”[37] Clapper concluded his statement by stating “The unauthorized disclosure of information about this important and entirely legal program is reprehensible and risks important protections for the security of Americans.”[37] On March 12, 2013, Clapper had told the United States Senate Select Committee on Intelligence that the NSA does “not wittingly” collect any type of data on millions or hundreds of millions of Americans.[38] In an NBC News interview, Clapper said he answered Senator Wyden’s question in the “least untruthful manner by saying no”.[39]
Clapper also stated that “the NSA collects the phone data in broad swaths, because collecting it (in) a narrow fashion would make it harder to identify terrorism-related communications. The information collected lets the government, over time, make connections about terrorist activities. The program doesn’t let the U.S. listen to people’s calls, but only includes information like call length and telephone numbers dialed.”[15]
On June 8, 2013, Clapper said “the surveillance activities published in The Guardian and The Washington Post are lawful and conducted under authorities widely known and discussed, and fully debated and authorized by Congress.”[40][10] The fact sheet described PRISM as “an internal government computer system used to facilitate the government’s statutorily authorized collection of foreign intelligence information from electronic communication service providers under court supervision, as authorized by Section 702 of the Foreign Intelligence Surveillance Act (FISA) (50 U.S.C. § 1881a).”[10]
The National Intelligence fact sheet further stated that “the United States Government does not unilaterally obtain information from the servers of U.S. electronic communication service providers. All such information is obtained with FISA Court approval and with the knowledge of the provider based upon a written directive from the Attorney General and the Director of National Intelligence.” It said that the Attorney General provides FISA Court rulings and semi-annual reports about PRISM activities to Congress, “provid[ing] an unprecedented degree of accountability and transparency.”[10]
The President of the United States, Barack Obama, said on June 7 “What you’ve got is two programs that were originally authorized by Congress, have been repeatedly authorized by Congress. Bipartisan majorities have approved them. Congress is continually briefed on how these are conducted. There are a whole range of safeguards involved. And federal judges are overseeing the entire program throughout.”[41] He also said, “You can’t have 100 percent security and then also have 100 percent privacy and zero inconvenience. You know, we’re going to have to make some choices as a society.”[41]
In separate statements, senior (not mentioned by name in source) Obama administration officials said that Congress had been briefed 13 times on the programs since 2009.[42]
Legislative branch
In contrast to their swift and forceful reactions the previous day to allegations that the government had been conducting surveillance of United States citizens’ telephone records, Congressional leaders initially had little to say about the PRISM program the day after leaked information about the program was published. Several lawmakers declined to discuss PRISM, citing its top-secret classification,[43] and others said that they had not been aware of the program.[44] After statements had been released by the President and the Director of National Intelligence, some lawmakers began to comment:
Senator John McCain (R-AZ)
- June 9 “We passed the Patriot Act. We passed specific provisions of the act that allowed for this program to take place, to be enacted in operation,”[45]
Senator Dianne Feinstein (D-CA), chair of the Senate Intelligence Committee
- June 9 “These programs are within the law”, “part of our obligation is keeping Americans safe”, “Human intelligence isn’t going to do it”.[46]
- June 9 “Here’s the rub: the instances where this has produced good — has disrupted plots, prevented terrorist attacks, is all classified, that’s what’s so hard about this.”[47]
- June 11 “It went fine…we asked him[ Keith Alexander ] to declassify things because it would be helpful (for people and lawmakers to better understand the intelligence programs).” “I’ve just got to see if the information gets declassified. I’m sure people will find it very interesting.”[48]
Senator Susan Collins (R-ME), member of Senate Intelligence Committee and past member of Homeland Security Committee
- June 11 “I had, along with Joe Lieberman, a monthly threat briefing, but I did not have access to this highly compartmentalized information” and “How can you ask when you don’t know the program exists?”[49]
Representative John Boehner (R-OH), Speaker of the House of Representatives
- June 11 “He’s a traitor”[50] (referring to Edward Snowden)
Representative Jim Sensenbrenner (R-WI), principal sponsor of the Patriot Act
- June 9, “This is well beyond what the Patriot Act allows.”[51] “President Obama’s claim that ‘this is the most transparent administration in history’ has once again proven false. In fact, it appears that no administration has ever peered more closely or intimately into the lives of innocent Americans.”[51]
Representative Mike Rogers (R-MI), a Chairman of the Permanent Select Committee on Intelligence.
- June 9 “One of the things that we’re charged with is keeping America safe and keeping our civil liberties and privacy intact. I think we have done both in this particular case,”[46]
- June 9 “Within the last few years this program was used to stop a program, excuse me, to stop a terrorist attack in the United States we know that. It’s, it’s, it’s important, it fills in a little seam that we have and it’s used to make sure that there is not an international nexus to any terrorism event that they may believe is ongoing in the United States. So in that regard it is a very valuable thing,”[52]
Senator Mark Udall (D-CO)
- June 9 “I don’t think the American public knows the extent or knew the extent to which they were being surveilled and their data was being collected.” “I think we ought to reopen the Patriot Act and put some limits on the amount of data that the National Security (Agency) is collecting,” “It ought to remain sacred, and there’s got to be a balance here. That is what I’m aiming for. Let’s have the debate, let’s be transparent, let’s open this up”.[46]
Representative Todd Rokita (R-IN)
- June 10 “We have no idea when they [ FISA ] meet, we have no idea what their judgments are”,[53]
Senator Rand Paul (R-KY)
- June 6 “When the Senate rushed through a last-minute extension of the FISA Amendments Act late last year, I insisted on a vote on my amendment (SA 3436) to require stronger protections on business records and prohibiting the kind of data-mining this case has revealed. Just last month, I introduced S.1037, the Fourth Amendment Preservation and Protection Act,”[54]
- June 9 “I’m going to be seeing if I can challenge this at the Supreme Court level. I’m going to be asking the Internet providers and all of the phone companies: ask your customers to join me in a class-action lawsuit.”[45]
Representative Luis Gutierrez (D-IL)
- June 9 “We will be receiving secret briefings and we will be asking, I know I’m going to be asking to get more information. I want to make sure that what they’re doing is harvesting information that is necessary to keep us safe and not simply going into everybody’s private telephone conversations and Facebook and communications. I mean one of the, you know the terrorists win when you debilitate freedom of expression and privacy.”[52]
Judicial branch
The Foreign Intelligence Surveillance Court (FISC) has not acknowledged, denied or confirmed any involvement in the PRISM program at this time. It has not issued any press statement or release relating to the current situation and uncertainty.
Applicable law and practice
On June 8, 2013, the Director of National Intelligence issued a fact sheet stating that PRISM “is not an undisclosed collection or data mining program”, but rather computer software used to facilitate the collection of foreign intelligence information “under court supervision, as authorized by Section 702 of the Foreign Intelligence Surveillance Act (FISA) (50 U.S.C. § 1881a).”[10] Section 702 provides that “the Attorney General [A.G.] and the Director of National Intelligence [DNI] may authorize jointly, for a period of up to 1 year from the effective date of the authorization, the targeting of persons reasonably believed to be located outside the United States to acquire foreign intelligence information.”[55] In order to authorize the targeting, the A.G. and DNI need to get an order from the Foreign Intelligence Surveillance Court (FISC) pursuant to Section 702 or certify that “intelligence important to the national security of the United States may be lost or not timely acquired and time does not permit the issuance of an order.”[55] When asking for an order, the A.G. and DNI must certify to FISC that “a significant purpose of the acquisition is to obtain foreign intelligence information.”[55] They do not need to specify which facilities or property that the targeting will be directed at.[55]
After getting a FISC order or determining that there are emergency circumstances, the A.G. and DNI can direct an electronic communication service provider to give them access to information or facilities to carry out the targeting and keep the targeting secret.[55] The provider then has the option to: (1) comply with the directive; (2) reject it; or (3) challenge it to FISC.
If the provider complies with the directive, it is released from liability to its users for providing the information and reimbursed for the cost of providing it.[55]
If the provider rejects the directive, the A.G. may request an order from FISC to enforce it.[55] A provider that fails to comply with FISC’s order can be punished with contempt of court.[55]
Finally, a provider can petition FISC to reject the directive.[55] In case FISC denies the petition and orders the provider to comply with the directive, the provider risks contempt of court if it refuses to comply with FISC’s order.[55] The provider can appeal FISC’s denial to the Foreign Intelligence Surveillance Court of Review and then appeal the Court of Review’s decision to the Supreme Court by a writ of certiorari for review under seal.[55]
The Senate Select Committee on Intelligence and the FISA Courts had been put in place to oversee intelligence operations in the period after the death of J. Edgar Hoover. Beverly Gage of Slate said, “When they were created, these new mechanisms were supposed to stop the kinds of abuses that men like Hoover had engineered. Instead, it now looks as if they have come to function as rubber stamps for the expansive ambitions of the intelligence community. J. Edgar Hoover no longer rules Washington, but it turns out we didn’t need him anyway.”[56]
Involvement of other countries
Australia
The Australian government has said it will investigate the impact of the PRISM program and the use of the Pine Gap surveillance facility on the privacy of Australian citizens.[57]
Canada
Canada’s national cryptologic agency, the Communications Security Establishment, said that commenting on PRISM “would undermine CSE’s ability to carry out its mandate”. Privacy Commissioner Jennifer Stoddart lamented Canada’s standards when it comes to protecting personal online privacy stating “We have fallen too far behind,” Stoddart wrote in her report. “While other nations’ data protection authorities have the legal power to make binding orders, levy hefty fines and take meaningful action in the event of serious data breaches, we are restricted to a ‘soft’ approach: persuasion, encouragement and, at the most, the potential to publish the names of transgressors in the public interest.” And, “when push comes to shove,” Stoddart wrote, “short of a costly and time-consuming court battle, we have no power to enforce our recommendations.”[58]
Germany
Germany did not receive any raw PRISM data, according to a Reuters report.[59]
Israel
Israeli newspaper Calcalist discussed[60] the Business Insider article[61] about the possible involvement of technologies from two secretive Israeli companies in the PRISM program – Verint Systems and Narus.
New Zealand
In New Zealand, University of Otago information science Associate Professor Hank Wolfe said that “under what was unofficially known as the Five Eyes Alliance, New Zealand and other governments, including the United States, Australia, Canada, and Britain, dealt with internal spying by saying they didn’t do it. But they have all the partners doing it for them and then they share all the information.”[62]
United Kingdom
In the United Kingdom, Government Communications Headquarters (GCHQ) has had access to the PRISM program on or before June 2010 and wrote 197 reports with it in 2012 alone. PRISM may have allowed GCHQ to circumvent the formal legal process required to seek personal material.[63][64]
Domestic response
|
|
The neutrality of this section is disputed. Please do not remove this message until the dispute is resolved. (June 2013) |
The New York Times editorial board charged that the Obama administration “has now lost all credibility on this issue,”[65] and lamented that “for years, members of Congress ignored evidence that domestic intelligence-gathering had grown beyond their control, and, even now, few seem disturbed to learn that every detail about the public’s calling and texting habits now reside in a N.S.A. database.”[66]
Republican and former member of Congress Ron Paul said, “We should be thankful for individuals like Edward Snowden and Glenn Greenwald who see injustice being carried out by their own government and speak out, despite the risk…. They have done a great service to the American people by exposing the truth about what our government is doing in secret.”[67] Paul denounced the government’s secret surveillance program: “The government does not need to know more about what we are doing…. We need to know more about what the government is doing.”[67] He called Congress “derelict in giving that much power to the government,” and said that had he been elected president, he would have ordered searches only when there was probable cause of a crime having been committed, which he said was not how the PRISM program was being operated.[68]
In response to Obama administration arguments that it could stop terrorism in the cases of Najibullah Zazi and David Headley, Ed Pilkington and Nicholas Watt of The Guardian said in regards to the role of PRISM and Boundless Informant interviews with parties involved in the Zazi scheme and court documents lodged in the United States and the United Kingdom indicated that “conventional” surveillance methods such as “old-fashioned tip-offs” of the British intelligence services initiated the investigation into the Zazi case.[69] An anonymous former CIA agent said that in regards to the Headley case, “That’s nonsense. It played no role at all in the Headley case. That’s not the way it happened at all.”[69] Pilkington and Watt concluded that the data-mining programs “played a relatively minor role in the interception of the two plots.”[69] Michael Daly of The Daily Beast stated that even though Tamerlan Tsarnaev had visited Inspire and even though Russian intelligence officials alerted U.S. intelligence officials about Tsarnaev, PRISM did not prevent him from carrying out the Boston bombings, and that the initial evidence implicating him came from his brother Dzhokhar Tsarnaev and not from federal intelligence. In addition Daly pointed to the fact that Faisal Shahzad visited Inspire but that federal authorities did not stop his attempted terrorist plot. Daly concluded “The problem is not just what the National Security Agency is gathering at the risk of our privacy but what it is apparently unable to monitor at the risk of our safety.”[70] In addition, political commentator Bill O’Reilly criticized the government, saying that PRISM did not stop the Boston bombings.[71]
In a blog post, David Simon, the creator of The Wire, compared the NSA’s programs, including PRISM, to a 1980s effort by the City of Baltimore to add dialed number recorders to all pay phones to know which individuals were being called by the callers;[72] the city believed that drug traffickers were using pay phones and pagers, and a municipal judge allowed the city to place the recorders. The placement of the dialers formed the basis of the show’s first season. Simon argued that the media attention regarding the NSA programs is a “faux scandal.”[72][73] George Takei, an actor who had experienced Japanese American internment, said that due to his memories of the internment, he felt concern towards the NSA surveillance programs that had been revealed.[74]
The Electronic Frontier Foundation (EFF), an international non-profit digital-rights group based in the U.S., is hosting a tool, by which an American resident can write to their government representatives regarding their opposition to mass spying.[75]
On June 11, 2013, the American Civil Liberties Union filed a lawsuit against the NSA citing that PRISM “violates Americans’ constitutional rights of free speech, association, and privacy”.[76]
International response
Reactions of Internet users in China were mixed between viewing a loss of freedom worldwide and seeing state surveillance coming out of secrecy. The story broke just before US President Barack Obama and Chinese President Xi Jinping met in California.[77][78] When asked about NSA hacking China, the spokeswoman of Ministry of Foreign Affairs of the People’s Republic of China said “China strongly advocates cybersecurity”.[79] The party-owned newspaper Liberation Daily described this surveillance like Nineteen Eighty-Four-style.[80] Hong Kong legislators Gary Fan and Claudia Mo wrote a letter to Obama, stating “the revelations of blanket surveillance of global communications by the world’s leading democracy have damaged the image of the U.S. among freedom-loving peoples around the world.”[81]
Sophie in ‘t Veld, a Dutch Member of the European Parliament, called PRISM “a violation of EU laws”.[82]

Protests at Checkpoint Charlie in Berlin
The German Federal Commissioner for Data Protection and Freedom of Information, Peter Schaar, condemned the program as “monstrous”.[83] He further added that White House claims do “not reassure me at all” and that “given the large number of German users of Google, Facebook, Apple or Microsoft services, I expect the German government […] is committed to clarification and limitation of surveillance.” Steffen Seibert, press secretary of the Chancellor’s office, announced that Angela Merkel will put these issues on the agenda of the talks with Barack Obama during his pending visit in Berlin.[84]
The Italian president of the Guarantor for the protection of personal data, Antonello Soro, said that the surveillance dragnet “would not be legal in Italy” and would be “contrary to the principles of our legislation and would represent a very serious violation”.[85]
William Hague, the foreign secretary of the United Kingdom, dismissed accusations that British security agencies had been circumventing British law by using information gathered on British citizens by Prism[86] saying, “Any data obtained by us from the United States involving UK nationals is subject to proper UK statutory controls and safeguards.”[86] David Cameron said Britain’s spy agencies that received data collected from PRISM acted within the law: “I’m satisfied that we have intelligence agencies that do a fantastically important job for this country to keep us safe, and they operate within the law.”[86][87] Malcolm Rifkind, the chairman of parliament’s Intelligence and Security Committee, said that if the British intelligence agencies were seeking to know the content of emails about people living in the UK, then they actually have to get lawful authority.[87] The UK’s Information Commissioner’s Office was more cautious, saying it would investigate PRISM alongside other European data agencies: “There are real issues about the extent to which U.S. law agencies can access personal data of UK and other European citizens. Aspects of U.S. law under which companies can be compelled to provide information to U.S. agencies potentially conflict with European data protection law, including the UK’s own Data Protection Act. The ICO has raised this with its European counterparts, and the issue is being considered by the European Commission, who are in discussions with the U.S. Government.”[82]
Ai Weiwei, a Chinese dissident, said “Even though we know governments do all kinds of things I was shocked by the information about the US surveillance operation, Prism. To me, it’s abusively using government powers to interfere in individuals’ privacy. This is an important moment for international society to reconsider and protect individual rights.”[88]
Kim Dotcom, a German-Finnish Internet entrepreneur who owned Megaupload, which was closed by the U.S. federal government, said “We should heed warnings from Snowden because the prospect of an Orwellian society outweighs whatever security benefits we derive from Prism or Five Eyes.”[89] The Hong Kong law firm representing Dotcom expressed a fear that the communication between Dotcom and the firm had been compromised by U.S. intelligence programs.[90]
Russia has offered to consider an asylum request from Edward Snowden.[91]
Taliban spokesperson Zabiullah Mujahid said “We knew about their past efforts to trace our system. We have used our technical resources to foil their efforts and have been able to stop them from succeeding so far.”[92][93]
Related government Internet surveillance programs
A parallel program, code-named BLARNEY, gathers up metadata as it streams past choke points along the backbone of the Internet. BLARNEY’s summary, set down in the slides alongside a cartoon insignia of a shamrock and a leprechaun hat, describes it as “an ongoing collection program that leverages IC [intelligence community] and commercial partnerships to gain access and exploit foreign intelligence obtained from global networks.”[94]
A related program, a big data visualization system based on cloud computing and free and open-source software (FOSS) technology known as “Boundless Informant”, was disclosed in documents leaked to The Guardian and reported on June 8, 2013. A leaked, top secret map allegedly produced by Boundless Informant revealed the extent of NSA surveillance in the U.S.[95]
http://en.wikipedia.org/wiki/PRISM_%28surveillance_program%29
ThinThread
ThinThread is the name of a project that the United States National Security Agency (NSA) pursued during the 1990s, according to a May 17, 2006 article in The Baltimore Sun.[1] The program involved wiretapping and sophisticated analysis of the resulting data, but according to the article, the program was discontinued three weeks before the September 11, 2001 attacks due to the changes in priorities and the consolidation of U.S. intelligence authority.[2] The “change in priority” consisted of the decision made by the director of NSA General Michael V. Hayden to go with a concept called Trailblazer, despite the fact that ThinThread was a working prototype that protected the privacy of U.S. citizens.
ThinThread was dismissed and replaced by the Trailblazer Project, which lacked the privacy protections.[3] A consortium led by Science Applications International Corporation was awarded a $280 million contract to develop Trailblazer in 2002.[4]
http://en.wikipedia.org/wiki/ThinThread
Trailblazer
Trailblazer was a United States National Security Agency (NSA) program intended to develop a capability to analyze data carried on communications networks like the Internet. It was intended to track entities using communication methods such as cell phones and e-mail.[1][2] It ran over budget, failed to accomplish critical goals, and was cancelled.
NSA whistleblowers J. Kirk Wiebe, William Binney, Ed Loomis, and House Permanent Select Committee on Intelligence staffer Diane Roark complained to the Department of Defense’s Inspector General (IG) about waste, fraud, and abuse in the program, and the fact that a successful operating prototype existed, but was ignored when the Trailblazer program was launched. The complaint was accepted by the IG and an investigation began that lasted until mid-2005 when the final results were issued. The results were largely hidden, as the report given to the public was heavily (90%) redacted, while the original report was heavily classified, thus restricting the ability of most people to see it.
The people who filed the IG complaint were later raided by armed Federal Bureau of Investigation (FBI) agents. While the Government threatened to prosecute all who signed the IG report, it ultimately chose to pursue an NSA Senior Executive — Thomas Andrews Drake — who helped with the report internally to NSA and who had spoken with a reporter about the project. Drake was later charged under the Espionage Act of 1917. His defenders claimed this was retaliation.[3][4] The charges against him were later dropped, and he agreed to plead guilty to having committed a misdemeanor under the Computer Fraud and Abuse Act, something that Jesselyn Radack of the Government Accountability Project (which helped represent him) called an “act of civil disobedience”.[5]
Background
Trailblazer was chosen over a similar program named ThinThread, a less costly project which had been designed with built-in privacy protections for United States citizens.[4][3] Trailblazer was later linked to the NSA electronic surveillance program and the NSA warrantless surveillance controversy.[3]
In 2002 a consortium led by Science Applications International Corporation was chosen by the NSA to produce a technology demonstration platform in a contract worth $280 million. Project participants included Boeing, Computer Sciences Corporation, and Booz Allen Hamilton. The project was overseen by NSA Deputy Director William B. Black, Jr., an NSA worker who had gone to SAIC, and then been re-hired back to NSA by NSA director Michael Hayden in 2000.[6][7][8] SAIC had also hired a former NSA director to its management; Bobby Inman.[9] SAIC also participated in the concept definition phase of Trailblazer.[10][11]
The NSA Inspector General issued a report on Trailblazer that “discussed improperly based contract cost increases, non-conformance in the management of the Statement of Work, and excessive labor rates for contractor personnel.” [13]
In 2004 the DoD IG report criticized the program (see the Whistleblowing section below). It said that the “NSA ‘disregarded solutions to urgent national security needs'” and “that TRAILBLAZER was poorly executed and overly expensive …” Several contractors for the project were worried about cooperating with DoD’s audit for fear of “management reprisal.”[5] The Director of NSA “nonconcurred” with several statements in the IG audit, and the report contains a discussion of those disagreements.[14]
In 2005, NSA director Michael Hayden told a Senate hearing that the Trailblazer program was several hundred million dollars over budget and years behind schedule.[15] In 2006 the program was shut down,[3] after having cost billions of US Dollars.[16] Several anonymous NSA sources told Hosenball of Newsweek later on that the project was a “wasteful failure”.[17]
The new project replacing Trailblazer is called Turbulence.[3]
Whistleblowing
According to a 2011 New Yorker article, in the early days of the project several NSA employees met with Diane S Roark, an NSA budget expert on the House Intelligence Committee. They aired their grievances about Trailblazer. In response, NSA director Michael Hayden sent out a memo saying that “individuals, in a session with our congressional overseers, took a position in direct opposition to one that we had corporately decided to follow … Actions contrary to our decisions will have a serious adverse effect on our efforts to transform N.S.A., and I cannot tolerate them.”[3]
In September 2002, several people filed a complaint with the Department of Defense IG’s office regarding problems with Trailblazer: they included Roark (aforementioned), ex-NSA senior analysts Bill Binney, Kirk Wiebe, and Senior Computer Systems Analyst Ed Loomis, who had quit the agency over concerns about its mismanagement of acquisition and allegedly illegal domestic spying.[3][18][19] A major source for the report was NSA senior officer Thomas Andrews Drake. Drake had been complaining to his superiors for some time about problems at the agency, and about the superiority of ThinThread over Trailblazer, for example, at protecting privacy.[19] Drake gave info to DoD during its investigation of the matter.[19] Roark also went to her boss at the House committee, Porter Goss, about problems, but was rebuffed.[20] She also attempted to contact William Renquist, the Supreme Court Chief Justice at the time.[19]
Drake’s own boss, Maureen Baginski, the third-highest officer at NSA, quit partly over concerns about the legality of its behavior.[3]
In 2003, the NSA IG (not the DoD IG)[19] had declared Trailblazer an expensive failure.[21] It had cost more than $1 billion.[8][22][23]
In 2005, the DoD IG produced a report on the result of its investigation of the complaint of Roark and the others in 2002. This report was not released to the public, but it has been described as very negative.[18] Mayer writes that it hastened the closure of Trailblazer, which was at the time in trouble from congress for being over budget.[3]
In November 2005, Drake contacted Siobhan Gorman, a reporter of The Baltimore Sun.[24][17][25] Gorman wrote several articles about problems at the NSA, including articles on Trailblazer. This series got her an award from the Society of Professional Journalists.[17]
In 2005, President George W. Bush ordered the FBI to find whoever had disclosed information about the NSA electronic surveillance program and its disclosure in the New York Times. Eventually, this investigation led to the people who had filed the 2002 DoD IG request, even though they had nothing to do with the New York Times disclosure. In 2007, the houses of Roark, Binney, and Wiebe were raided by armed FBI agents. According to Mayer, Binney claims the FBI pointed guns at his head and that of his wife. Wiebe said it reminded him of the Soviet Union.[3][18] None of these people were ever charged with any crime. Four months later, Drake was raided in November 2007 and his computers and documents were confiscated.
In 2010 Drake was indicted by the U.S. Department of Justice on charges of obstructing justice, providing false information, and violating the Espionage Act of 1917,[17][26][27] part of President Barack Obama’s crackdown on whistleblowers and “leakers”.[24][17][28][18] The government tried to get Roark to testify to a conspiracy, and made similar requests to Drake, offering him a plea bargain. They both refused.[3]
In June 2011, the ten original charges against Drake were dropped, instead he pleaded guilty to a misdemeanor.[5]
http://www.youtube.com/watch?v=1AXwwSq_me4
Boundless Informant
Boundless Informant is a big data analysis and data visualization system used by the United States National Security Agency (NSA) to give NSA managers summaries of NSA’s world wide data collection activities.[1] It is described in an unclassified, For Official Use Only Frequently Asked Questions (FAQ) memo published by The Guardian.[2] According to a Top Secret heat map display also published by The Guardian and allegedly produced by the Boundless Informant program, almost 3 billion data elements from inside the United States were captured by NSA over a 30-day period ending in March 2013.
Data analyzed by Boundless Informant includes electronic surveillance program records (DNI) and telephone call metadata records (DNR) stored in an NSA data archive called GM-PLACE. It does not include FISA data, according to the FAQ memo. PRISM, a government codename for a collection effort known officially as US-984XN, which was revealed at the same time as Boundless Informant, is one source of DNR data. According to the map, Boundless Informant summarizes data records from 504 separate DNR and DNI collection sources (SIGADs). In the map, countries that are under surveillance are assigned a color from green, representing least coverage to red, most intensive.[3][4]
History
Intelligence gathered by the United States government inside the United States or specifically targeting US citizens is legally required to be gathered in compliance with the Foreign Intelligence Surveillance Act of 1978 (FISA) and under the authority of the Foreign Intelligence Surveillance Court (FISA court).[5][6][7]
NSA global data mining projects have existed for decades, but recent programs of intelligence gathering and analysis that include data gathered from inside the United States such as PRISM were enabled by changes to US surveillance law introduced under President Bush and renewed under President Obama in December 2012.[8]
Boundless Informant was first publicly revealed on June 8, 2013, after classified documents about the program were leaked to The Guardian.[1][9] The newspaper identified its informant, at his request, as Edward Snowden, who worked at the NSA for the defense contractor Booz Allen Hamilton.[10]
Technology
According to published slides, Boundless Informant leverages Free and Open Source Software—and is therefore “available to all NSA developers”—and corporate services hosted in the cloud. The tool uses HDFS, MapReduce, and Cloudbase for data processing.[11]
Legality and FISA Amendments Act of 2008
The FISA Amendments Act (FAA) Section 702 is referenced in PRISM documents detailing the electronic interception, capture and analysis of metadata. Many reports and letters of concern written by members of Congress suggest that this section of FAA in particular is legally and constitutionally problematic, such as by targeting U.S. persons, insofar as “Collections occur in U.S.” as published documents indicate.[12][13][14][15]
The ACLU has asserted the following regarding the FAA: “Regardless of abuses, the problem with the FAA is more fundamental: the statute itself is unconstitutional.”[16]
Senator Rand Paul is introducing new legislation called the Fourth Amendment Restoration Act of 2013 to stop the NSA or other agencies of the United States government from violating the Fourth Amendment to the U.S. Constitution using technology and big data information systems like PRISM and Boundless Informant.[17][18]
http://en.wikipedia.org/wiki/Boundless_Informant
ECHELON
ECHELON is a name used in global media and in popular culture to describe a signals intelligence (SIGINT) collection and analysis network operated on behalf of the five signatory states to the UKUSA Security Agreement[1] (Australia, Canada, New Zealand, the United Kingdom, and the United States, referred to by a number of abbreviations, including AUSCANNZUKUS[1] and Five Eyes).[2][3] It has also been described as the only software system which controls the download and dissemination of the intercept of commercial satellite trunk communications.[4]
ECHELON, according to information in the European Parliament document, “On the existence of a global system for the interception of private and commercial communications (ECHELON interception system)” was created to monitor the military and diplomatic communications of the Soviet Union and its Eastern Bloc allies during the Cold War in the early 1960s.[5]
The system has been reported in a number of public sources.[6] Its capabilities and political implications were investigated by a committee of the European Parliament during 2000 and 2001 with a report published in 2001,[5] and by author James Bamford in his books on the National Security Agency of the United States.[4] The European Parliament stated in its report that the term ECHELON is used in a number of contexts, but that the evidence presented indicates that it was the name for a signals intelligence collection system. The report concludes that, on the basis of information presented, ECHELON was capable of interception and content inspection of telephone calls, fax, e-mail and other data traffic globally through the interception of communication bearers including satellite transmission, public switched telephone networks (which once carried most Internet traffic) and microwave links.[5]
Bamford describes the system as the software controlling the collection and distribution of civilian telecommunications traffic conveyed using communication satellites, with the collection being undertaken by ground stations located in the footprint of the downlink leg.
Organization
| UKUSA Community |
|---|
|
The UKUSA intelligence community was assessed by the European Parliament (EP) in 2000 to include the signals intelligence agencies of each of the member states:
- the Government Communications Headquarters of the United Kingdom,
- the National Security Agency of the United States,
- the Communications Security Establishment of Canada,
- the Defence Signals Directorate of Australia, and
- the Government Communications Security Bureau of New Zealand.
- the National SIGINT Organisation (NSO) of The Netherlands
The EP report concluded that it seemed likely that ECHELON is a method of sorting captured signal traffic, rather than a comprehensive analysis tool.[5]
Capabilities
The ability to intercept communications depends on the medium used, be it radio, satellite, microwave, cellular or fiber-optic.[5] During World War II and through the 1950s, high frequency (“short wave”) radio was widely used for military and diplomatic communication,[7] and could be intercepted at great distances.[5] The rise of geostationary communications satellites in the 1960s presented new possibilities for intercepting international communications. The report to the European Parliament of 2001 states: “If UKUSA states operate listening stations in the relevant regions of the earth, in principle they can intercept all telephone, fax and data traffic transmitted via such satellites.”[5]
The role of satellites in point-to-point voice and data communications has largely been supplanted by fiber optics; in 2006, 99% of the world’s long-distance voice and data traffic was carried over optical-fiber.[8] The proportion of international communications accounted for by satellite links is said to have decreased substantially over the past few years[when?] in Central Europe to an amount between 0.4% and 5%.[5] Even in less-developed parts of the world, communications satellites are used largely for point-to-multipoint applications, such as video.[9] Thus, the majority of communications can no longer be intercepted by earth stations; they can only be collected by tapping cables and intercepting line-of-sight microwave signals, which is possible only to a limited extent.[5]
One method of interception is to place equipment at locations where fiber optic communications are switched. For the Internet, much of the switching occurs at relatively few sites. There have been reports of one such intercept site, Room 641A, in the United States. In the past[when?] much Internet traffic was routed through the U.S. and the UK, but this has changed; for example, in 2000, 95% of intra-German Internet communications was routed via the DE-CIX Internet exchange point in Frankfurt.[5] A comprehensive worldwide surveillance network is possible only if clandestine intercept sites are installed in the territory of friendly nations, and/or if local authorities cooperate. The report to the European Parliament points out that interception of private communications by foreign intelligence services is not necessarily limited to the U.S. or British foreign intelligence services.[5]
Most reports on ECHELON focus on satellite interception; testimony before the European Parliament indicated that separate but similar UK-US systems are in place to monitor communication through undersea cables, microwave transmissions and other lines.[10]
Controversy
Intelligence monitoring of citizens, and their communications, in the area covered by the AUSCANNZUKUS security agreement has caused concern. British journalist Duncan Campbell and New Zealand journalist Nicky Hager asserted in the 1990s that the United States was exploiting ECHELON traffic for industrial espionage, rather than military and diplomatic purposes.[10] Examples alleged by the journalists include the gear-less wind turbine technology designed by the German firm Enercon[5][11] and the speech technology developed by the Belgian firm Lernout & Hauspie.[12] An article in the US newspaper Baltimore Sun reported in 1995 that European aerospace company Airbus lost a $6 billion contract with Saudi Arabia in 1994 after the US National Security Agency reported that Airbus officials had been bribing Saudi officials to secure the contract.[13][14]
In 2001, the Temporary Committee on the ECHELON Interception System recommended to the European Parliament that citizens of member states routinely use cryptography in their communications to protect their privacy, because economic espionage with ECHELON has been conducted by the US intelligence agencies.[5]
Bamford provides an alternative view, highlighting that legislation prohibits the use of intercepted communications for commercial purposes, although he does not elaborate on how intercepted communications are used as part of an all-source intelligence process.
Hardware
According to its website, the U.S. National Security Agency (NSA) is “a high technology organization … on the frontiers of communications and data processing”. In 1999 the Australian Senate Joint Standing Committee on Treaties was told by Professor Desmond Ball that the Pine Gap facility was used as a ground station for a satellite-based interception network. The satellites were said to be large radio dishes between 20 and 100 meters in diameter in geostationary orbits.[citation needed] The original purpose of the network was to monitor the telemetry from 1970s Soviet weapons, air defence radar, communications satellites and ground based microwave communications.[15]
Name
The European Parliament’s Temporary Committee on the ECHELON Interception System stated: “It seems likely, in view of the evidence and the consistent pattern of statements from a very wide range of individuals and organisations, including American sources, that its name is in fact ECHELON, although this is a relatively minor detail.”[5] The U.S. intelligence community uses many code names (see, for example, CIA cryptonym).
Former NSA employee Margaret Newsham claims that she worked on the configuration and installation of software that makes up the ECHELON system while employed at Lockheed Martin, for whom she worked from 1974 to 1984 in Sunnyvale, California, US, and in Menwith Hill, England, UK.[16] At that time, according to Newsham, the code name ECHELON was NSA’s term for the computer network itself. Lockheed called it P415. The software programs were called SILKWORTH and SIRE. A satellite named VORTEX intercepted communications. An image available on the internet of a fragment apparently torn from a job description shows Echelon listed along with several other code names.[17]
Ground stations
The 2001 European Parliamentary (EP) report[5] lists several ground stations as possibly belonging to, or participating in, the ECHELON network. These include:
Likely satellite intercept stations
The following stations are listed in the EP report (p. 54 ff) as likely to have, or to have had, a role in intercepting transmissions from telecommunications satellites:
- Hong Kong (since closed)
- Australian Defence Satellite Communications Station (Geraldton, Western Australia)
- Menwith Hill (Yorkshire, U.K.) Map (reportedly the largest Echelon facility)[18]
- Misawa Air Base (Japan) Map
- GCHQ Bude, formerly known as GCHQ CSO Morwenstow, (Cornwall, U.K.) Map
- Pine Gap (Northern Territory, Australia – close to Alice Springs) Map
- Sugar Grove (West Virginia, U.S.) Map
- Yakima Training Center (Washington, U.S.) Map
- GCSB Waihopai (New Zealand)
- GCSB Tangimoana (New Zealand)
- CFS Leitrim (Ontario, Canada)
- Teufelsberg (Berlin, Germany) (closed 1992)
Other potentially related stations
The following stations are listed in the EP report (p. 57 ff) as ones whose roles “cannot be clearly established”:
- Ayios Nikolaos (Cyprus – U.K.)
- Bad Aibling Station (Bad Aibling, Germany – U.S.)
- relocated to Griesheim in 2004[19]
- deactivated in 2008[20]
- Buckley Air Force Base (Aurora, Colorado)
- Fort Gordon (Georgia, U.S.)
- Gander (Newfoundland & Labrador, Canada)
- Guam (Pacific Ocean, U.S.)
- Kunia Regional SIGINT Operations Center (Hawaii, U.S.)
- Lackland Air Force Base, Medina Annex (San Antonio, Texas)
http://en.wikipedia.org/wiki/ECHELON
Room 641A
Room 641A is a telecommunication interception facility operated by AT&T for the U.S. National Security Agency that commenced operations in 2003 and was exposed in 2006.[1][2]
Description
Room 641A is located in the SBC Communications building at 611 Folsom Street, San Francisco, three floors of which were occupied by AT&T before SBC purchased AT&T.[1] The room was referred to in internal AT&T documents as the SG3 [Study Group 3] Secure Room. It is fed by fiber optic lines from beam splitters installed in fiber optic trunks carrying Internet backbone traffic[3] and, as analyzed by J. Scott Marcus, a former CTO for GTE and a former adviser to the FCC, who has access to all Internet traffic that passes through the building, and therefore “the capability to enable surveillance and analysis of internet content on a massive scale, including both overseas and purely domestic traffic.”[4] Former director of the NSA’s World Geopolitical and Military Analysis Reporting Group, William Binney, has estimated that 10 to 20 such facilities have been installed throughout the United States.[2]
The room measures about 24 by 48 feet (7.3 by 15 m) and contains several racks of equipment, including a Narus STA 6400, a device designed to intercept and analyze Internet communications at very high speeds.[1]
The very existence of the room was revealed by a former AT&T technician, Mark Klein, and was the subject of a 2006 class action lawsuit by the Electronic Frontier Foundation against AT&T.[5] Klein claims he was told that similar black rooms are operated at other facilities around the country.
Room 641A and the controversies surrounding it were subjects of an episode of Frontline, the current affairs documentary program on PBS. It was originally broadcast on May 15, 2007. It was also featured on PBS’s NOW on March 14, 2008. The room was also covered in the PBS Nova episode “The Spy Factory”.
Lawsuit
More complicated diagram of how it allegedly worked. From EFF court filings.[3] See bottom of the file page for enlarged and rotated version.
The Electronic Frontier Foundation (EFF) filed a class-action lawsuit against AT&T on January 31, 2006, accusing the telecommunication company of violating the law and the privacy of its customers by collaborating with the National Security Agency (NSA) in a massive, illegal program to wiretap and data-mine Americans’ communications. On July 20, 2006, a federal judge denied the government’s and AT&T’s motions to dismiss the case, chiefly on the ground of the States Secrets Privilege, allowing the lawsuit to go forward. On August 15, 2007, the case was heard by the Ninth Circuit Court of Appeals and was dismissed on December 29, 2011 based on a retroactive grant of immunity by Congress for telecommunications companies that cooperated with the government. The U.S. Supreme Court declined to hear the case.[6] A different case by the EFF was filed on September 18, 2008, titled Jewel v. NSA.
http://en.wikipedia.org/wiki/Room_641A
List of government surveillance projects for the United States
United States
A top secret document leaked by Edward Snowden to The Guardian in 2013, originally due to be declassified on 12 April 2038.
- Nationwide Suspicious Activity Reporting Initiative: Under this initiative, a Suspicious Activity Report may be filed by law enforcers, public safety personnel, owners of critical infrastructure or the general public.
- PRISM: A clandestine national security electronic surveillance program operated by the United States National Security Agency (NSA) which can target customers of participating corporations outside or inside the United States
- DCSNet: The Federal Bureau of Investigation (FBI)’s point-and-click surveillance system that can perform instant wiretaps on any telecommunications device located in the United States.[6]
- Main Core: A personal and financial database storing information of millions of U.S. citizens believed to be threats to national security.[7] The data mostly comes from the NSA, FBI, CIA, as well as other government sources.[7]
- Magic Lantern: A keystroke logging software deployed by the FBI in the form of an e-mail attachment. When activated, it acts as a trojan horse and allows the FBI to decrypt user communications.[8]
- Carnivore: A system implemented by the Federal Bureau of Investigation that was designed to monitor email and electronic communications. Apparently replaced by commercial software such as NarusInsight
- NSA call database
- Intelligence Community (IC): A cooperative federation of 16 government agencies working together, but also separately, to gather intelligence and conduct espionage
- Comprehensive National Cybersecurity Initiative
- Utah Data Center: The Intelligence Community’s US$1.5 billion data storage that is designed to store extremely large amounts of data, on the scale of yottabytes[9][10][11]
- Financial Crimes Enforcement Network: A bureau of the Department of the Treasury that collects and analyzes financial transactions in order to combat financial crimes.
- Terrorist Finance Tracking Program: A joint initiative run by the CIA and the Department of the Treasury to access the SWIFT (Society for Worldwide Interbank Financial Telecommunication) transaction database as part of the Bush administration‘s “Global War on Terrorism“. According to the U.S. government, its efforts to counter terrorist activities were compromised after the existence of the Terrorist Finance Tracking Program was leaked to the media.[12]
- Tailored Access Operations: Intelligence-gathering unit of the NSA that is capable of harvesting approximately 2 petabytes of data per hour.[13][14]
- Boundless Informant: A system deployed by the National Security Agency to analyze global electronic information. In March 2013, Boundless Informant gathered 14 billion data reports from Iran, 6.3 billion from India, and 2.8 billion from the United States.[15]
http://en.wikipedia.org/wiki/List_of_government_surveillance_projects
Related Posts On Pronk Palisades
James Bamford — The National Security Agency (NSA) — Videos
National Security Agency (NSA) Wants To Build Supercomputer To Crack All Encryption — Videos
National Security Agency (NSA) Intercepts FedX and UPS Packages To Install Malware Software — Bugs iPhones and Laptops — Videos
No Such Agency — NSA — National Security Agency — Threat To The Liberty and Privacy of The American People — None Of Their Damn Business — Still Trust The Federal Government? — Videos
Enemy Of The State: Life Imitating Art –National Security Agency Targets American People — Vidoes
Big Brother Barack Targets All The American People As Enemies of The State and Democratic Party — National Security Agency’s PRISM Is The Secret Security Surveillance State (S4) Means of Invading Privacy and Limiting Liberty — Outrageous Overreach–Videos
National Security Agency (NSA) and Federal Bureau Investigation (FBI) Secret Security Surveillance State (S4) Uses Stellar Wind and PRISM To Create Secret Dossiers On All American Citizen Targets Similar To East Germany Stasi Files–Videos
NSA’s PRISM Political Payoff: 40 Million Plus Foreigners Are In USA As Illegal Aliens! — 75% Plus Lean Towards Democratic Party — Pathway To One Party Rule By 2025 If Senate Bill Becomes Law Giving Illegal Aliens Legal Status — 25 Million American Citizens Looking For Full Time Jobs! — Videos
Amnesty Before Enforcement — Congressional Gangsters’ Comprehensive Immigration “Reform” Bill Targets American Citizens For Unemployment — American Citizens Want All Illegal Aliens Deported Not Rewarded With Legal Status — Target The Amnesty Illegal Alien Gangsters For Defeat — Videos
U.S. Hacking China and Hong Kong — Videos
Digital Campaigns Using Microtargeting and Data Mining To Target Voters — Videos
Sasha Issenberg — The Victory Lab: The Secret Science of Winning Campaigns — Videos
Related Posts on Pronk Pops
Pronk Pops Show 112, June 7, 2013, Segment 0: Marxist-Leninists Go To The Wall With Holder — The Man Who Knows Where The Bodies Are Buried Enjoys President Obama’s Full Confidence Says Political Fixer Valerie Jarrett — Wall Street Wants Holder To Hang On — American People Say Hit The Road Jack — Videos
Pronk Pops Show 112, June 7, 2013: Segment 1: U.S. Real Gross Domestic Product Growth Still Stagnating At 2.4% in First Quarter of 2013 As Institute for Supply Management Factory Index Sinks to 49.0 Lowest Since June 2009 — Videos
Pronk Pops Show 112, June 7, 2013, Segment 2: Federal Advisory Council (FAC) May 17, 2013 Report — No Exit To A Bridge Over Troubled Waters — Keyboarding Money — We’re screwed! — Videos
Pronk Pops Show 112, June 7, 2013, Segment 3: Official Unemployment Rate Rises To 7.6% with 11.8 Million Americans Unemployed and Only 175,000 Jobs Created in May — Videos
Pronk Pops Show 112, June 7, 2013, Segment 4: No Such Agency — NSA — National Security Agency — Threat To The Liberty and Privacy of The American People — None Of Their Damn Business — Still Trust The Federal Government? — Videos
Read Full Post | Make a Comment ( None so far )The Pronk Pops Show 141, October 2, 2013, Segment 0: Breaking News — Tom Clancy — Rest In Peace — Photos — Videos
Posted on October 3, 2013. Filed under: Bombs, Books, Communications, Consitutional Law, Cruise Missiles, Culture, Disasters, Energy, Federal Government, Foreign Policy, Games, Government, Law, Media, Movies, Music, Philosophy, Photos, Pistols, Politics, Religion, Rifles, Security, Social Networking, Social Science, Success, Technology, Terror, Terrorism, Videos, Violence, War, Wealth, Weapons, Wisdom | Tags: Author, Books, Culture, Entertainment, Freedom, Games, Intelligence, Military, Movies, Novels, Power, Raymond Thomas Pronk, RIP, Technology, The Hunt for Red October, The Pronk Pops Show 141 |
Pronk Pops Show 141: October 2, 2013
Pronk Pops Show 140: September 30, 2013
Pronk Pops Show 139: September 27, 2013
Pronk Pops Show 138: September 26, 2013
Pronk Pops Show 137: September 25, 2013
Pronk Pops Show 136: September 24, 2013
Pronk Pops Show 135: September 23, 2013
Pronk Pops Show 134: September 20, 2013
Pronk Pops Show 133: September 19, 2013
Pronk Pops Show 132: September 18, 2013
Pronk Pops Show 131: September 17, 2013
Pronk Pops Show 130: September 16, 2013
Pronk Pops Show 129: September 13, 2013
Pronk Pops Show 128: September 12, 2013
Pronk Pops Show 127: September 11, 2013
Pronk Pops Show 126: September 10, 2013
Pronk Pops Show 125: September 9, 2013
Pronk Pops Show 124: September 6, 2013
Listen To Pronk Pops Podcast or Download Show 135-141
Listen To Pronk Pops Podcast or Download Show 131-134
Listen To Pronk Pops Podcast or Download Show 124-130
Listen To Pronk Pops Podcast or Download Shows 121-123
Listen To Pronk Pops Podcast or Download Shows 118-120
Listen To Pronk Pops Podcast or Download Shows 113 -117
Listen To Pronk Pops Podcast or Download Show 112
Listen To Pronk Pops Podcast or Download Shows 108-111
Listen To Pronk Pops Podcast or Download Shows 106-108
Listen To Pronk Pops Podcast or Download Shows 104-105
Listen To Pronk Pops Podcast or Download Shows 101-103
Listen To Pronk Pops Podcast or Download Shows 98-100
Listen To Pronk Pops Podcast or Download Shows 94-97
Listen To Pronk Pops Podcast or Download Shows 93
Listen To Pronk Pops Podcast or Download Shows 92
Listen To Pronk Pops Podcast or Download Shows 91
Listen To Pronk Pops Podcast or Download Shows 88-90
Listen To Pronk Pops Podcast or Download Shows 84-87
Listen To Pronk Pops Podcast or Download Shows 79-83
Listen To Pronk Pops Podcast or Download Shows 74-78
Listen To Pronk Pops Podcast or Download Shows 71-73
Listen To Pronk Pops Podcast or Download Shows 68-70
Listen To Pronk Pops Podcast or Download Shows 65-67
Listen To Pronk Pops Podcast or Download Shows 62-64
Listen To Pronk Pops Podcast or Download Shows 58-61
Listen To Pronk Pops Podcast or Download Shows 55-57
Listen To Pronk Pops Podcast or Download Shows 52-54
Listen To Pronk Pops Podcast or Download Shows 49-51
Listen To Pronk Pops Podcast or Download Shows 45-48
Listen To Pronk Pops Podcast or Download Shows 41-44
Listen To Pronk Pops Podcast or Download Shows 38-40
Listen To Pronk Pops Podcast or Download Shows 34-37
Listen To Pronk Pops Podcast or Download Shows 30-33
Listen To Pronk Pops Podcast or Download Shows 27-29
Listen To Pronk Pops Podcast or Download Shows 17-26
Listen To Pronk Pops Podcast or Download Shows 16-22
Listen To Pronk Pops Podcast or Download Shows 10-15
Listen To Pronk Pops Podcast or Download Shows 01-09
Segment 0: Breaking News — Tom Clancy — Rest In Peace — Photos — Video
Author Tom Clancy dies at 66
Best-selling Author Tom Clancy Dead at 66
Author Tom Clancy, master of the modern day thriller, dead at 66
VIDEO – Worldwide Trend Topic Tom Clancy’s Dead WorldWideTT
US author Tom Clancy dies aged 66
Archive Tom Clancy on prophetic 9 11 plot
Tom Clancy Dead Tom Clancy dies in Baltimore age 66 Author Tom Clancy’s Splinter Cell 1947-2013
Tom Clancy Dead Tom Clancy dies in Baltimore age 66 Author Tom Clancy’s Rainbow Six 1947 2013
9/11 Tom Clancy Coverage of the WTC 7 Collapse CNN 5 35 PM 9 11 2001
Politika (1997) – Tom Clancy’s Fictional Interview on Boris Yeltsin
Tom Clancy on Government
Tom Clancy – Greek Island Interview – SSN – 1996
Tom Clancy, Dead or Alive: Discussion w/ ‘Chuck’ A. Horner, retired Air Force General
Tom Clancy – OP Center (Full movie)
Tom Clancy’s Splinter Cell: Blacklist – All Cutscenes | Movie [HD]
The Hunt For Red October (1990) Trailer.flv
The Hunt for Red October (1/9) Movie CLIP – Another Possibility (1990) HD
The Hunt for Red October (2/9) Movie CLIP – Ryan’s Plan (1990) HD
The Sum of All Fears (1/9) Movie CLIP – Everyone Has Opinions (2002) HD
The Sum of All Fears (2/9) Movie CLIP – I Can’t Tell You That (2002) HD
The True Story The Hunt For Red October
Tom Clancy – Wiki Article
Published on May 21, 2013
Thomas Leo “Tom” Clancy, Jr. is an American author who is best known for his technically detailed espionage and military science storylines that are set during and in the aftermath of the Cold War, along with video games which bear his name for licensing and promotional purposes, although he did not actually work on them himself. His name is also a brand for similar movie scripts written by ghost writers and many series of non-fiction books on military subjects and merged biographies of key leaders. He is Vice Chairman of Community Activities and Public Affairs, as well as a part-owner of the Baltimore Orioles.
Personal life
Clancy was born in Baltimore, Maryland. He attended Loyola Blakefield in Towson, Maryland, graduating with the class of 1965. He then attended Loyola College in Baltimore, graduating in 1969. Before making his literary debut, he spent some time running an independent insurance agency. This agency thrived for a few years before joining a group of investors.
Clancy and his first wife Wanda married in 1969, separated briefly in 1995, and permanently separated in December 1996. Clancy filed for divorce in November 1997, which became final in January 1999.
In 1993, Tom Clancy joined a group of investors that included Peter Angelos and bought the Baltimore Orioles from Eli Jacobs. In 1998, he reached an agreement to purchase the Minnesota Vikings, but had to abandon the deal because of the divorce settlement cost.
On June 26, 1999, Clancy married freelance journalist Alexandra Marie Llewellyn, whom he had met in 1997. Llewellyn is the daughter of J. Bruce Llewellyn, and a family friend of Colin Powell, who originally introduced the couple to each other.
In 2008, the French video game manufacturer Ubisoft purchased the use of Clancy’s name for an undisclosed sum. It has been used in conjunction with video games and related products such as movies and books. Based on his interest in space, and his investment in the launch vehicle company Rotary Rocket, in 2007 Clancy was interviewed for the documentary film Orphans of Apollo.
Political views
Tom Clancy has been a lifetime supporter of conservative and Republican causes in America. His books bear dedications to conservative political figures, most notably Ronald Reagan. A week after the September 11, 2001 attacks, on The O’Reilly Factor, Clancy stated that left-wing politicians in the United States were partly responsible for September 11 due to their “gutting” of the Central Intelligence Agency. Clancy has also associated himself with General Anthony Zinni, a critic of the George W. Bush administration, and has been critical of former Defense Secretary Donald Rumsfeld as well.
On September 11, 2001, Clancy was interviewed by Judy Woodruff on CNN. During the interview, he asserted “Islam does not permit suicide” (see Islam and suicide). Among other observations during this interview, Clancy cited discussions he had with military experts on the lack of planning to handle a hijacked plane being used in a suicide attack and criticized the news media’s treatment of the United States Intelligence Community. Clancy appeared again on PBS’s Charlie Rose, to discuss the implications of the day’s events with Richard Holbrooke, New York Times journalist Judith Miller, and Senator John Edwards, among others. Clancy was interviewed on these shows because his 1994 book Debt of Honor included a scenario where a disgruntled Japanese character crashes a fueled Boeing 747 into the U.S. Capitol dome during a State of the Union address, killing the President and most of Congress. This plot device bore strong similarities to the attacks of Sept. 11, 2001.
Clancy has been a Life Member of the National Rifle Association since 1978.
Bibliography
The Hunt for Red October, Patriot Games, Clear and Present Danger, and The Sum of All Fears have been turned into commercially successful films with actors Alec Baldwin, Harrison Ford, and Ben Affleck as Clancy’s most famous fictional
Tom Clancy, Best-Selling Novelist of Military Thrillers, Dies
at 66
By JULIE BOSMAN
Tom Clancy, whose complex, adrenaline-fueled military novels made him one of the world’s best-selling and best-known authors, died on Tuesday in a hospital in Baltimore. He was 66.
Ivan Held, the president of G. P. Putnam’s Sons, his publisher, did not provide a cause of death.
Mr. Clancy’s books were successfully transformed into blockbuster Hollywood films, including “Patriot Games,” “The Hunt for Red October“ and “Clear and Present Danger.”
His next book, “Command Authority,” is planned for publication on Dec. 3.
Seventeen of his novels were No. 1 New York Times best sellers, including his most recent, “Threat Vector,” which was released in December 2012.
Mr. Clancy was an insurance salesman when he sold his first novel, “The Hunt for Red October,” to the Naval Institute Press for only $5,000.
That publisher had never released a novel before, but the editors were taken with Mr. Clancy’s manuscript. They were concerned, however, that there were too many technical descriptions, so they asked him to make cuts. Mr. Clancy made revisions and cut at least 100 pages.
The book took off when President Ronald Reagan, who had received a copy, called it was “my kind of yarn” and said that he couldn’t put it down.
After the book’s publication in 1985, Mr. Clancy was praised for his mastery of technical details about Soviet submarines and weaponry. Even high-ranking members of the military took notice of the book’s apparent inside knowledge.
In an interview in 1986, Mr. Clancy said, “When I met Navy Secretary John Lehman last year, the first thing he asked me about the book was, ‘Who the hell cleared it?’ “
David Shanks, a Penguin executive who worked with Mr. Clancy for decades, called him “a consummate author, creating the modern-day thriller, and one of the most visionary storytellers of our time.”Born to a middle-class family in Baltimore on April 12, 1947, Mr. Clancy skipped over the usual children’s literature and became obsessed by naval history from a young age, reading journals and books whose intended audience was career military officers and engineering experts.
He absorbed details of submarine warfare, espionage, missile systems and covert plots between superpowers.
He attended Loyola College in Baltimore, where he majored in English, and graduated in 1969. While Mr. Clancy harbored ambitions to join the military, even joining the Army R.O.T.C., he was told that he was too nearsighted to qualify.
Mr. Clancy began working at a small insurance agency in rural Maryland that was founded by his wife’s grandfather.
After “The Hunt for Red October” was published, Mr. Clancy’s fame was fairly instant. Frequently posing for photographs in darkened aviator sunglasses, jeans and holding a cigarette, Mr. Clancy spoke of the laserlike focus required to succeed.
“I tell them you learn to write the same way you learn to play golf,” he said. “You do it, and keep doing it until you get it right. A lot of people think something mystical happens to you, that maybe the muse kisses you on the ear. But writing isn’t divinely inspired — it’s hard work.”
He followed “The Hunt for Red October” with “Red Storm Rising“ in 1986, “Patriot Games” in 1987, “The Cardinal of the Kremlin“ in 1988 and “Clear and Present Danger” in 1989.
The critical reception to his novels was gushing from the start. Reviewing “Red Storm Rising” in The New York Times in 1986, Christopher Lehmann-Haupt wrote that the book “far surpassed” Mr. Clancy’s debut novel.
“Red Storm Rising” is a “superpower thriller,” he wrote, “the verbal equivalent of a high-tech video game.” (Mr. Clancy would eventually venture into video games, which were easily adapted from his novels.)
Other critics questioned the unwaveringly virtuous nature of many of Mr. Clancy’s heroes, particularly his protagonist Jack Ryan.
“All the Americans are paragons of courage, endurance and devotion to service and country,” Robert Lekachman wrote in the Times in 1986. “Their officers are uniformly competent and occasionally inspired. Men of all ranks are faithful husbands and devoted fathers.”
Mr. Clancy was frequently accused of using classified information in his novels, a claim that amused him. While he spent time on military bases, visited the Pentagon and dined with high-level military officials, he insisted that he didn’t want to know any classified information.
“I hang my hat on getting as many things right as I can,” Mr. Clancy once said in an interview. “I’ve made up stuff that’s turned out to be real, that’s the spooky part.”
Tom Clancy
Thomas Leo “Tom” Clancy, Jr. (April 12, 1947 – October 1, 2013)[1][2] was an American author best known for his technically detailed espionage and military science storylines that are set during and in the aftermath of the Cold War, along with video games which bear his name for licensing and promotional purposes. His name was also a brand for similar movie scripts written by ghost writers and many series of non-fiction books on military subjects and merged biographies of key leaders. He was Vice Chairman of Community Activities and Public Affairs, as well as a part-owner, of the Baltimore Orioles.
Literary career
Clancy’s fiction works, The Hunt for Red October, Patriot Games, Clear and Present Danger, and The Sum of All Fears, have been turned into commercially successful films with actors Alec Baldwin, Harrison Ford, and Ben Affleck as Clancy’s most famous fictional character Jack Ryan, while his second most famous character John Clark has been played by actors Willem Dafoe and Liev Schreiber. All but two of Clancy’s solely written novels feature Jack Ryan or John Clark.
The first NetForce novel was adapted as a television movie, starring Scott Bakula and Joanna Going. The first Op-Center novel was released to coincide with a 1995 NBC television mini-series of the same name (Tom Clancy’s Op-Center) starring Harry Hamlin and a cast of stars. Though the mini-series did not continue, the book series did, but it had little in common with the first mini-series other than the title and the names of the main characters.
With the release of The Teeth of the Tiger, Clancy introduced Jack Ryan’s son and two nephews as main characters; these characters continue in his three latest novels, Dead or Alive, Locked On and Threat Vector.
Clancy wrote several nonfiction books about various branches of the U.S. armed forces (see non-fiction listing, below). Clancy also branded several lines of books and video games with his name that are written by other authors, following premises or storylines generally in keeping with Clancy’s works. These are sometimes referred to by fans as “apostrophe” books; Clancy did not initially acknowledge that these series were being authored by others, only thanking the actual authors in the headnotes for their “invaluable contribution to the manuscript”.
By 1988, Clancy had earned $1.3 million for The Hunt for Red October and had signed a $3 million contract for his next three books.[3] By 1997, it was reported that Penguin Putnam Inc. (part of Pearson Education) would pay Clancy $50 million for world rights to two new books, and another $25 million to Red Storm Entertainment for a four-year book/multimedia deal.[4] Clancy followed this up with an agreement with Penguin’s Berkley Books for 24 paperbacks to tie in with the ABC television miniseries Tom Clancy’s Net Force aired in the fall/winter of 1998. The Op-Center universe has laid the ground for the series of books written by Jeff Rovin, which was in an agreement worth $22 million, bringing the total value of the package to $97 million.[4]
In 1993, Clancy joined a group of investors that included Peter Angelos and bought the Baltimore Orioles from Eli Jacobs. In 1998, he reached an agreement to purchase theMinnesota Vikings, but had to abandon the deal because of the divorce settlement cost.
On June 26, 1999, Clancy married freelance journalist Alexandra Marie Llewellyn, whom he had met in 1997.[5] Llewellyn is the daughter of J. Bruce Llewellyn, and a family friend ofColin Powell, who originally introduced the couple to each other.[6]
In 2008, the French video game manufacturer Ubisoft purchased the use of Clancy’s name for an undisclosed sum. It has been used in conjunction with video games and related products such as movies and books.[7] Based on his interest in space, and his investment in the launch vehicle company Rotary Rocket, in 2007 Clancy was interviewed for the documentary film Orphans of Apollo.
Political views
A longtime holder of conservative and Republican views, Clancy’s books bear dedications to American conservative political figures, most notably Ronald Reagan. A week after theSeptember 11, 2001 attacks, on The O’Reilly Factor, Clancy claimed that left-wing politicians in the United States were partly responsible for September 11 due to their “gutting” of the Central Intelligence Agency.[6]
In recent years, Clancy associated himself with General Anthony Zinni, a critic of the George W. Bush administration, and has been critical of former Defense Secretary Donald Rumsfeld as well.[8]
On September 11, 2001, Clancy was interviewed by Judy Woodruff on CNN.[9] During the interview, he asserted “Islam does not permit suicide” (see Islam and suicide). Among other observations during this interview, Clancy cited discussions he had with military experts on the lack of planning to handle a hijacked plane being used in a suicide attack and criticized the news media’s treatment of the United States Intelligence Community. Clancy appeared again on PBS‘s Charlie Rose, to discuss the implications of the day’s events with Richard Holbrooke, New York Times journalist Judith Miller, and Senator John Edwards, among others.[10] Clancy was interviewed on these shows because his 1994 book Debt of Honor included a scenario where a disgruntled Japanese character crashes a fueled Boeing 747 into the U.S. Capitol dome during an address by the President to a joint session of Congress, killing the President and most of Congress. This plot device bore strong similarities to the attacks of September 11, 2001.
Clancy was also a Life Member of the National Rifle Association since 1978.[11]
Personal
Clancy was born in Baltimore, Maryland.[1] He attended Loyola Blakefield in Towson, Maryland, graduating with the class of 1965.[1] He then attended Loyola College (now Loyola University) in Baltimore, graduating in 1969.[1] Before making his literary debut, he spent some time running an independent insurance agency.
Clancy and his first wife Wanda married in 1969, separated briefly in 1995, and permanently separated in December 1996.[12] Clancy filed for divorce in November 1997,[13] which became final in January 1999.[14] In 1999, Clancy married freelance journalist Alexandra Marie Llewellyn.[15]
Clancy died October 1, 2013, after a brief illness at Johns Hopkins Hospital, near his Baltimore home. He was 66 and no cause of death was released. He is survived by four children and his second wife, Alexandra Marie Llewellyn.[16]
Bibliography
Works, by year of publication
- The Hunt for Red October (1984)
- Clancy’s first published novel. CIA analyst Jack Ryan assists in the defection of a respected Soviet naval captain, along with the most advanced ballistic missile submarine of the Soviet fleet. The movie (1990) stars Alec Baldwin as Ryan and Sean Connery as Captain Ramius. Captain Mancuso is introduced here. Nearly every book after has Mancuso in ever increasing command of U.S. submarine forces.
- Red Storm Rising (1986)
- War between NATO and USSR. The basis of the combat game of the same name, this book is not a member of the Ryan story series (although the protagonist of the story has many similarities with Jack Ryan). Cowritten with Larry Bond.
- Patriot Games (1987)
- Patriot Games chronologically predates the first book that Clancy wrote, The Hunt for Red October. Jack Ryan foils an attack in London on the Prince and Princess of Wales by the “Ulster Liberation Army”. The ULA then attacks Ryan’s Maryland home while he is hosting the Prince and Princess for dinner. The movie stars Harrison Ford as Ryan and Samuel L. Jackson as Robby Jackson.
- The Cardinal of the Kremlin (1988)
- The sequel to “The Hunt for Red October.” First appearance of John Clark and Sergey Golovko. Ryan leads a CIA operation which forces the head of the KGB to defect. Other elements include anti-satellite lasers and other SDI-type weapons, and the Soviet war in Afghanistan. Major Alan Gregory is introduced here. (He appears later, updating SAMsoftware in The Bear and the Dragon). Colonel Bondarenko also is introduced here. (He appears in later books offering advice to Golovko in “Executive Orders” and commanding the Russian Army defenses against China in its sequel “The Bear and the Dragon”.)
- Clear and Present Danger (1989)
- The President authorizes the CIA to use American military forces in a covert war against cocaine producers in Colombia. The operation is betrayed. Ryan meets John Clark as they lead a mission to rescue abandoned soldiers. Domingo “Ding” Chavez (Clark’s protege in later novels) is one of the rescued soldiers. The 1994 film stars Harrison Ford as Ryan, Willem Dafoe as Clark, and Raymond Cruz as Chavez.
- The Sum of All Fears (1991)
- Arab terrorists find a nuclear weapon that had been lost by Israel, and use it to attack the United States. This nearly triggers a war between the U.S. and the Soviet Union, due to the incompetence of the new President and his mistress with an anti-Ryan agenda. Ryan intervenes to avert the war. The 2002 film stars Ben Affleck as Ryan and Liev Schreiber as Clark, and changes the identity and motivation of the terrorists to neo-Nazis.
- Without Remorse (1993)
- Without Remorse takes place during the Vietnam War, when Jack Ryan was a teenager. Ex-SEAL John Clark (then John Kelly) fights a one-man war against drug dealers in Baltimore, attracting the attention of Jack’s father Emmett, a Baltimore police detective. He also helps plan and execute a raid on a prisoner-of-war camp in North Vietnam. Clark joins the Central Intelligence Agency (CIA).
- Debt of Honor (1994)
- A secret cabal of extreme nationalists gains control of Japan (having acquired some nuclear weapons), and start a war with the U.S. Ryan, now National Security Advisor, and Clark and Chavez, agents in Japan, help win the war. The Vice President resigns in a scandal, and the President appoints Ryan to replace him. A vengeful, die-hard Japanese airline pilot then crashes a jetliner into the U.S. Capitol during a joint session of Congress attended by most senior U.S. government officials, including the President. Ryan thus becomes the new President through succession.
- Executive Orders (1996)
- This is the immediate sequel to Debt of Honor. President Ryan survives press hazing, an assassination attempt, and a biological warfare attack on the United States. Clark and Chavez trace the virus to a Middle Eastern madman, and the U.S. military goes to work.
- SSN: Strategies for Submarine Warfare (1996)
- Follows the missions of USS Cheyenne in a future war with China precipitated by China’s invasion of the disputed Spratly Islands. Also not a Ryan universe book, SSN is actually a loosely connected collection of “scenario” chapters in support of the eponymous video game.
- Rainbow Six (1998)
- Released to coincide with the video game of the same name. John Clark and Ding, who is now Clark’s son-in-law, lead an elite multi-national anti-terrorist unit that combats a worldwide genocide attempt by eco-terrorists. Ryan is the U.S. President and only mentioned or referred to as either ‘The President’ or ‘Jack’.
- The Bear and the Dragon (2000)
- War between Russia and China. Ryan recognizes the independence of Taiwan, Chinese police officers kill a Roman Catholic Cardinal, and the American armed forces help Russia defeat a Chinese invasion of Siberia.
- Red Rabbit (2002)
- In the early 1980s, CIA analyst Ryan aids in the defection of a Soviet officer who knows of a plan to assassinate Pope John Paul II.
- The Teeth of the Tiger (2003)
- Jack Ryan’s son, Jack Ryan, Jr., becomes an intelligence analyst, and then a field consultant, for The Campus, an off-the-books intelligence agency with the freedom to discreetly assassinate individuals “who threaten national security”, following the end of the Jack Ryan Sr. presidential administration. This book of the Jack Ryan series by Tom Clancy introduces Ryan’s son and two nephews as heirs to his spook-legacy.
- Dead or Alive (2010, with Grant Blackwood)
- The story picks up where The Teeth of the Tiger left off with Jack Ryan, Jr. and The Campus trying to catch a terrorist known as “The Emir”.
- Against All Enemies (2011, with Peter Telep)
- A terrorist bombing in Pakistan wipes out Max Moore’s entire CIA team. As the only survivor, the former Navy SEAL plunges deeper into the treacherous tribal lands to find the terrorist cell, but what he discovers there leads him to a much darker conspiracy in an unexpected part of the globe — the United States/Mexico border.
- Locked On (Dec 2011, with Mark Greaney)
- While Jack Ryan Jr. trains to become a field operative within The Campus, his father campaigns for re-election as President of the United States. A devout enemy of Jack Sr. launches a privately funded vendetta to discredit him, while a corrupt Pakistani general has entered into a deadly pact with a fanatical terrorist to procure nuclear warheads.
- Search and Destroy (July 2012, with Peter Telep) (Cancelled)
- Threat Vector (Dec 2012, with Mark Greaney)
- Jack Ryan has only just moved back into the Oval Office when he is faced with a new international threat. An aborted coup in the People’s Republic of China has left President Wei Zhen Lin with no choice but to agree with the expansionist policies of General Su Ke Quiang. They have declared the South China Sea a protectorate and are planning an invasion of Taiwan. The Ryan administration is determined to thwart China’s ambitions, but the stakes are dangerously high as a new breed of powerful Chinese anti-ship missiles endanger the US Navy’s plans to protect the island. Meanwhile, Chinese cyber warfare experts have launched a devastating attack on American infrastructure.
- Command Authority (December 2013, with Mark Greaney)
- There is a new strong man in Russia but his rise to power is based on a dark secret hidden decades in the past. The clue to the mystery lies with a most unexpected source, President Jack Ryan.[17]
Novels not in a series
- Red Storm Rising (1986)
- SSN (1996)
- Against All Enemies (2011)
Jack Ryan/John Clark universe chronology
In the order in which they occur in the storyline (and when they occur):
- Without Remorse (1969–70, 1973 – Starts late 1969, in Hurricane Camille’s aftermath. Continues the following spring, in 1970. Epilogue is titled “February 12, 1973”) Ryan briefly appears in this novel.
- Patriot Games (1982, based on a reference to Ryan’s age, which is 31 at the beginning of the novel. This roughly fits with a reference to the Princess of Wales’s first child being a baby and a few months old, Prince William was born in 1982) Discrepancies include the reference to a van having a likely year of manufacture of 1984.
- Red Rabbit (circa spring of 1982, based on references to living Leonid Brezhnev and Mikhail Suslov, both of whom died in 1982 (although Suslov died already in January of that year), as well as Jack Ryan, Jr.’s age in the novel, 6 months) Discrepancies with the estimate of 1982 include frequent references to “Transformers” which did not appear until 1984 and the fact that the Orioles played the Phillies in the World Series in 1983, not to mention that the World Series is played in the Fall, not the Spring. Also a reference to “Coke Classic” which did not debut until the summer of 1985.
- The Hunt for Red October (1984)
- The Cardinal of the Kremlin (1986) – “The first chapter is set in January and states that Ryan is 35 years old. It also has references to the other books set earlier. For example the Foleys have been in Moscow for almost four years. The book must begin (not including prologue which was set end of previous year) in January 1986.
Starting with the following novel, the series becomes distinctly different from real history as noted below.
- Clear and Present Danger (1988) The book refers to Jack’s age as 40.
- The Sum of All Fears (1990–1991) — Israel partially cedes sovereignty over Jerusalem to the Vatican and Saudi Arabia, and the city becomes a United Nations protectorate policed by Swiss Guards. Residents of Jerusalem can choose between either Vatican, Israeli or Islamic judicial law. Denver is devastated by a terrorist nuclear explosion. The book occurs after the Persian Gulf War and before the dissolution of the Soviet Union. It is implied that both events occur at the same time in the Ryan universe as in actual history (of the Soviet Union dissolution), 1991. In the earlier chapters it states that it had almost been two Novembers since President Fowler had been elected, making the beginning set in 1990. Interestingly, the video game Tom Clancy’s Rainbow Six puts the atomic detonation in Denver as having occurred in 1989.
- Debt of Honor (1995–1996) — The U.S. and Russia destroy all of their ballistic missiles. After crippling the U.S. economy and becoming a nuclear power, Japan invades and takes the Marianas Islands; the United States and Japan fight a brief war, which the Japanese lose (they are subsequently denuclearized); an embittered Japanese pilot and proponent of the war crashes a 747 into the United States Capitol Building immediately after Ryan’s confirmation vote for the Vice President, killing most of the House andSenate, the President, all nine Supreme Court justices, the senior military establishment (including the JCS), and most of the Cabinet; Ryan is left in charge of a gutted government. The end of the book occurs eleven months before 1997 presidential inauguration. Of interest, but not crucial to the plot of this or further books is that North and South Korea were said to be unified at some point between The Sum of All Fears and this book.
- Executive Orders (1996) — Saddam Hussein is assassinated; Iran and Iraq merge forming the United Islamic Republic; the UIR launches a biological attack on the U.S. using the Ebola virus; the United States launches the Second Persian Gulf War against the UIR and defeats them; the Ayatollah is killed in a smart-bomb attack by the U.S.
- Rainbow Six (1999–2000) – events are based on the Sydney Olympics held in 2000, RAINBOW – an elite counter-terrorist force – is created and engages terrorists acrossEurope. Ecoterrorists plan to create a genetically-enhanced virus based on Ebola and cancer cells, which they plan to use to wipe out much of the world’s population.
- The Bear and the Dragon (2002) — Russia is admitted to NATO; China and Russia fight a major war, in which the U.S. intervenes on its NATO ally’s side. It implies that theBritish Prime Minister is Tony Blair. Ryan has won re-election as president (2001). He resigns before the 2004 election making Robby Jackson president.
- The Teeth of the Tiger (2006, based on the age of Jack Ryan, Jr.) The U.S. is now engaged in a global war on terrorism, in response to the September 11 attacks, which occurred in the Ryan universe as they did in the real world. It is mentioned that the wars in Afghanistan and Iraq occurred in the Ryan universe continuity, and that the Jerusalem Treaty signed in The Sum of All Fears has failed as Israelis and Palestinians went back to fighting each other.
- Dead or Alive (2007, based on Jack Ryan’s announcement that he would run against Ed Kealty for President “in the coming year”) — The Umayyad Revolutionary Council (the Ryan universe version of Al-Qaeda) and its leader “The Emir” (based on Osama bin Laden) plan a string of major attacks on the U.S. The wars in Afghanistan and Iraq continue, as in our timeline, and President Kealty is in the process of withdrawing U.S. troops from Iraq. A character also explicitly refers to the date as May 2010, in the process of decoding encrypted messages, but this must be seen as a contradiction, as Ed Kealty is president and is only president for one term. In accordance with the Jack Ryan continuity, Kealty must be president in the term 2005-2009.
- Locked On (2008, based on Jack Ryan Sr.’s campaign for re-election). Jack Ryan is running for president again. Since it is only possible for Kealty to serve one term per the rules of the Constitution, that term must be from 2005 to 2009. The election happens in this book, too, making it only possible that the events take place in 2008. Jack Ryan Sr.’s opponent, Edward Kealty, tries to dig up dirt on him by going after John Clark. Meanwhile, a renegade Pakistani general steals nuclear weapons from his country and delivers them to rebel Dagestani forces. In the middle of all this, Jack Ryan Jr. and The Campus try to prevent the use of the lethal weapon and come to help Clark.
- Threat Vector (2012). Ryan has been sworn in as president of the United States after having been elected the previous year. It also states that the events of this novel happen six months after the previous novel.
- Command Authority To be released 12-3-2013
Op-Center universe
- Op-Center (1995)
- Mirror Image (1995)
- Games of State (1996)
- Acts of War (1996)
- Balance of Power (1998)
- State of Siege (1999)
- Divide and Conquer (2000)
- Line of Control (2001)
- Mission of Honor (2002)
- Sea of Fire (2003)
- Call to Treason (2004)
- War of Eagles (2005)
Net Force universe
- Net Force (1999)
- Hidden Agendas (1999)
- Night Moves (1999)
- Breaking Point (2000)
- Point of Impact (2001)
- CyberNation (2001)
- State of War (2003)
- Changing of the Guard (2003)
- Springboard (2005)
- The Archimedes Effect (2006)
Net Force Explorers universe
- Virtual Vandals (1998)
- The Deadliest Game (1999)
- One is the Loneliest Number (1999)
- The Ultimate Escape (1999)
- End Game (1999)
- Cyberspy (1999)
- The Great Race (2000)
- Shadow of Honor (2000)
- Private Lives (2000)
- Safe House (2000)
- GamePrey (2000)
- Duel Identity (2000)
- Deathworld (2001)
- High Wire (2001)
- Cold Case (2001)
- Runaways (2001)
- Cloak and Dagger (2002)
- Death Match (2002)
Power Plays series
- Politika (novel, 1997)
- Politika (video game) by Red Storm Entertainment
- Politika (board game)
- ruthless.com (novel, 1998)
- ruthless.com (video game, 1998) by Red Storm Entertainment
- Shadow Watch (novel, 1999) by Jerome Preisler
- Shadow Watch (video game, 1999) by Red Storm Entertainment
- Bio-Strike (novel, 2000) by Jerome Preisler
- Cold War (novel, 2001) by Jerome Preisler
- Cutting Edge (novel, 2002) by Jerome Preisler
- Zero Hour (novel, 2003) by Jerome Preisler
- Wild Card (novel, 2004) by Jerome Preisler
Ghost Recon universe
- Tom Clancy’s Ghost Recon by Grant Blackwood as David Michaels
- Tom Clancy’s Ghost Recon: Combat Ops by David Michaels
- Tom Clancy’s Ghost Recon: Choke Point by Peter Telep
EndWar universe
- Tom Clancy’s EndWar by Grant Blackwood as David Michaels
- Tom Clancy’s EndWar: The Hunted by Grant Blackwood as David Michaels
- Tom Clancy’s EndWar: The Missing by Peter Telep
H.A.W.X universe
- Tom Clancy’s H.A.W.X by Grant Blackwood as David Michaels
Non-fiction
Guided Tour
- Submarine: A Guided Tour Inside a Nuclear Warship (1993)
- Armored Cav (1994), Putnam Adult, ISBN 978-0399140549
- Fighter Wing: A Guided Tour of an Air Force Combat Wing (1995)
- Marine: A Guided Tour of a Marine Expeditionary Unit (1996)
- Airborne: A Guided Tour of an Airborne Task Force (1997, ISBN 0-425-15770-9)
- Carrier: A Guided Tour of an Aircraft Carrier (1999)
- Special Forces: A Guided Tour of U.S. Army Special Forces (2001)
Study in Command
- Into the Storm – On the Ground in Iraq (with Fred Franks) (1997)
- Every Man a Tiger — the Gulf War Air Campaign (with Chuck Horner) (1999)
- Shadow Warriors — Inside the Special Forces (with Carl Stiner) (2002)
- Battle Ready (with Anthony Zinni) (2004)
Other
- The Tom Clancy Companion — Edited by Martin H. Greenberg — Writings by Clancy along with a concordance of all his fiction novels, detailing characters and military units or equipment.
Video games
In 1996, Clancy co-founded the video game developer Red Storm Entertainment and ever since he has had his name on several of Red Storm’s most successful games. Red Storm was later bought by publisher Ubisoft Entertainment, which continued to use the Clancy name, though the extent of Clancy’s actual involvement with creation of the games and development of intellectual properties, if any, was unclear. This game series includes:
- The Hunt for Red October (1987): Submarine simulation loosely based on the novel of the same name. Produced by Grandslam Entertainment for IBM PC, C64, and Amiga.
- Red Storm Rising (1988): Submarine sim loosely based on the novel of the same name. Produced by MicroProse for IBM PC, C64, and Amiga.
- The Hunt for Red October (1990): Submarine sim based on the movie of the same name. Produced by Grandslam Entertainment for Amiga, Amstrad CPC, Atari ST, Commodore 64, DOS, ZX Spectrum.
- The Hunt for Red October (1990): Submarine sim based on the movie of the same name. Produced for Nintendo Entertainment System, Game Boy, and Super NES.
- SSN (1996): Submarine sim based on the novel of the same name. Produced by Simon & Schuster Interactive for IBM PC.
- ruthless.com (1998) by Red Storm Entertainment: Strategy game based loosely on the book of the same name.
- Shadow Watch (2000): Turn-based strategy based on the Power Play novel of the same name.[18]
- The Sum of All Fears (2002): Tactical first-person shooter similar in style to Rainbow Six, but based on the Ghost Recon engine. The plot is based on the movie of the same name. Produced by Ubisoft for the IBM PC and Nintendo GameCube system.
- Rainbow Six series: Squad-based first-person shooters, based on the novel of the same name, typically taking place in closed urban environments. 18 Rainbow Six games have been produced so far.
- Tom Clancy’s Rainbow Six (1998)
- Tom Clancy’s Rainbow Six: Eagle Watch (1999)
- Tom Clancy’s Rainbow Six: Rogue Spear (1999)
- Tom Clancy’s Rainbow Six: Urban Operations (2000)
- Tom Clancy’s Rainbow Six: Covert Operations Essentials (2000)
- Tom Clancy’s Rainbow Six: Take-Down – Missions in Korea (2001)
- Tom Clancy’s Rainbow Six: Black Thorn (2001)
- Tom Clancy’s Rainbow Six: Lone Wolf (2002)
- Tom Clancy’s Rainbow Six 3: Raven Shield (2003)
- Tom Clancy’s Rainbow Six 3: Black Arrow (2004)
- Tom Clancy’s Rainbow Six 3: Athena Sword (2004)
- Tom Clancy’s Rainbow Six 3: Iron Wrath (2005)
- Tom Clancy’s Rainbow Six: Lockdown (2005)
- Tom Clancy’s Rainbow Six: Critical Hour (2006)
- Tom Clancy’s Rainbow Six: Vegas (2006)
- Tom Clancy’s Rainbow Six: Vegas 2 (2008)
- Tom Clancy’s Rainbow Six: Shadow Vanguard (2011)
- Tom Clancy’s Rainbow 6: Patriots (2013)
- Tom Clancy’s Ghost Recon series: Squad-based first- and third-person shooters. As opposed to the Rainbow Six games, Ghost Recon usually takes place in larger, outdoor environments. There have been 13 Ghost Recon games so far.
- Tom Clancy’s Ghost Recon (2001)
- Tom Clancy’s Ghost Recon: Desert Siege (2003)
- Tom Clancy’s Ghost Recon: Island Thunder (2003)
- Tom Clancy’s Ghost Recon: Jungle Storm (2004)
- Tom Clancy’s Ghost Recon 2 (2004)
- Tom Clancy’s Ghost Recon 2: Summit Strike (2005)
- Tom Clancy’s Ghost Recon Advanced Warfighter (2006)
- Tom Clancy’s Ghost Recon Advanced Warfighter 2 (2007)
- Tom Clancy’s Ghost Recon Predator (2010)
- Tom Clancy’s Ghost Recon Wii (2010)
- Tom Clancy’s Ghost Recon: Shadow Wars (2011)
- Tom Clancy’s Ghost Recon: Future Soldier (2012)[19]
- Tom Clancy’s Ghost Recon Online (2012)
- Tom Clancy’s Splinter Cell series: Third person stealth games, lately spawned a line of books written by a series of different authors, all writing under the pseudonym David Michaels.
- Tom Clancy’s Splinter Cell (2002)
- Tom Clancy’s Splinter Cell: Pandora Tomorrow (2004)
- Tom Clancy’s Splinter Cell: Chaos Theory (2005)
- Tom Clancy’s Splinter Cell: Essentials (2006)
- Tom Clancy’s Splinter Cell: Double Agent (2006)
- Tom Clancy’s Splinter Cell: Conviction (2010)
- Tom Clancy’s Splinter Cell: Blacklist (2013)
- EndWar series: Franchise set in a speculative World War III, taking place in 2020.
- Tom Clancy’s EndWar (2008)
- Tom Clancy’s EndWar 2 (TBA)
- H.A.W.X series: Air combat
- Tom Clancy’s H.A.W.X (2009)
- Tom Clancy’s H.A.W.X 2 (2010)
- Tom Clancy’s The Division (2014)
Board games
- The Hunt for Red October (1988)
- Naval wargame published by TSR, Inc., based on the novel of the same name. It covered modern naval warfare between NATO and the Warsaw Pact.
- Red Storm Rising (1989)
- Ground warfare wargame published by TSR, Inc., based on the novel of the same name. It covered an attack on NATO forces in western Europe by the Warsaw Pact. It included rules for integration with The Hunt for Red October game of the year before. The publisher reused the system for Europe Aflame (1989), a strategic World War IIgame, and A Line in the Sand, a strategic game about the First Gulf War.
- Tom Clancy’s Politika (1997)[20]
Achievements and awards
- Clancy was one of only three authors to have sold two million copies on a first printing in the 1990s (the other two being John Grisham and J. K. Rowling). Clancy’s 1989 novelClear and Present Danger sold 1,625,544 hardcover copies, making it the #1 bestselling novel of the 1980s.[21]
- Clancy received an honorary doctorate in humane letters and delivered the commencement address at Rensselaer Polytechnic Institute in 1992, and has since worked a reference to the school into many of his main works.[22]
- Clancy was an honorary Yeoman Warder of The Tower of London holding the title “Supernumerary Yeoman”.[23] On the television show Ace of Cakes his wife commissioned, for his 60th birthday, a special cake in the shape of the Tower of London in acknowledgment of his status. In the episode, Tom Clancy referred to the Beefeaters as, “Just a terrific bunch of guys”.
- Clancy received the Alfred Thayer Mahan Award for Literary Achievement from the Navy League of the United States in 1990.
References
- ^ Jump up to:a b c d Clancy, Tom (October 31, 1997). “alt.books.tom-clancy”. groups.google.com. Retrieved 2012-03-20.
- Jump up^ A few sources, such as Who’s Who and “Tom Clancy”. Encyclopedia Britannica Online. Retrieved March 20, 2012., give his birth date as March 12, 1947. He died Wednesday October 2, 2013.
- Jump up^ Anderson, Patrick (1 May 1988). “King of the Techno-thriller”. New York Times Magazine.
- ^ Jump up to:a b Quinn, Judy (24 August 1997). “$100M Mega-Deals for Clancy”. Publishers Weekly 243 (34).[dead link]
- Jump up^ “Alexandra Llewellyn, Tom Clancy,” The New York Times, June 27, 1999.
- ^ Jump up to:a b “Tom Clancy”. NNDB. 1999-06-26. Retrieved 2010-02-28.
- Jump up^ Mitchell, Richard (2008-03-25). “Clancy name bought by Ubisoft, worth big bucks. SOURCE: www.chatwave.in”. Xbox360fanboy.com. Retrieved 2010-02-28.
- Jump up^ Paperback Writer, The New Republic, May 25, 2004.
- Jump up^ 23 October 2007. “Tom Clancy on Sept 11 2001 & WTC 7 Collapse”. Youtube.com. Retrieved 2010-02-28.
- Jump up^ “An hour about the 9/11 attacks”. Charlierose.com. 2001-09-11. Retrieved 2010-02-28.
- Jump up^ LaPierre, Wayne (1994). Guns, Crime, and Freedom. HarperPerennial. p. xiii.ISBN 978-0-06-097674-3.
- Jump up^ Schindehette, Susan (15 June 1998). “Storm Rising”. People Magazine 49 (23): 141.
- Jump up^ Jones, Brent (27 August 2008). “Reconsider Clancy case ruling”. Baltimore Sun.
- Jump up^ “Case No. 04-C-03-000749 OC”. Circuit Court for Calvert County. Retrieved March 23, 2012.
- Jump up^ Kennedy, John R. (2013-10-02). “Author Tom Clancy dead at 66 – Okanagan”. Globalnews.ca. Retrieved 2013-10-02.
- Jump up^ “Tom Clancy, author of ‘Hunt for Red October’ and ‘Patriot Games,’ dead at 66”. NY Times. Retrieved 2 October 2013.
- Jump up^ “Command Authority by Tom Clancy”. Barnesandnoble.com. Retrieved 2013-10-02.
- Jump up^ Ryan, Michael E. (12 April 2000). “Shadow Watch”. Gamespot. Retrieved 23 March 2012.
- Jump up^ Totilo, Stephen (May 12, 2011). “Ghost Recon: Future Soldier Will Rival the Shooter Heavyweights, but is Getting Far Out of the Way”. Kotaku. Retrieved May 12, 2011.
- Jump up^ “Tom Clancy’s Politika | Board Game”. BoardGameGeek. Retrieved 2011-12-19.
- Jump up^ “Washington Post”. Washington Post. 1997-06-01. Retrieved 2010-02-28.
- Jump up^ “Rensselaer Magazine: Summer 2004: At Rensselaer”. Rpi.edu. Retrieved 2010-02-28.
- Jump up^ “TC Post: Clancy Speaks Again Briefly”. Clancyfaq.com. 2000-06-25. Retrieved 2010-02-28.
External links
 Media related to Tom Clancy at Wikimedia Commons
Media related to Tom Clancy at Wikimedia Commons Quotations related to Tom Clancy at Wikiquote
Quotations related to Tom Clancy at Wikiquote- Library resources in your library and in other libraries by Tom Clancy
- Official Tom Clancy website
- Transcript of interview with Deborah Norville on the War in Iraq — April 2004
- Tom Clancy at the Internet Book Database of Fiction
- Tom Clancy at the Internet Movie Database
- The Page of Tom Clancy’s Primary Publisher
- Booknotes interview with Clancy and Gen. Fred Franks on Into the Storm: A Study in Command, July 13, 1997.
- In Depth interview with Clancy, February 3, 2002
Related Posts on Pronk Pops
The Pronk Pops Show 141, October 2, 2013, Segment 1: Democratic Demands For Raising National Debt Limit — Obama: “I Will Not Negotiate On The Debt” — I Will Just Print Debt Free Money! — Videos
Pronk Pops Show 115, June 28, 2013: Segment 0: Enemy Of The State: Life Imitating Art –National Security Agency Targets American People — Vidoes
Posted on June 28, 2013. Filed under: American History, Books, Budgetary Policy, Communications, Consitutional Law, Economics, Education, Employment, Federal Government, Fiscal Policy, Foreign Policy, Government, Government Spending, History, Illegal Immigration, Immigration, Law, Media, Philosophy, Politics, Regulation, Resources, Security, Tax Policy, Taxes, Videos, Violence, War, Wisdom | Tags: Art, Bill Binney, Culture, Economics, Enemy of The State, James Banford, Life, Movies, NSA, Photos, Politics, PRISM, Privacy, Pronk Pops Show 115, Raymond Thomas Pronk, Videos |
Pronk Pops Show 115: June 28, 2013
Pronk Pops Show 114: June 21, 2013
Pronk Pops Show 113: June 14, 2013
Pronk Pops Show 112: June 7, 2013
Pronk Pops Show 111: May 31, 2013
Pronk Pops Show 110: May 24, 2013
Pronk Pops Show 109: May 17, 2013
Pronk Pops Show 108: May 10, 2013
Pronk Pops Show 107: May 3, 2013
Listen To Pronk Pops Podcast or Download Shows 113 -115
Listen To Pronk Pops Podcast or Download Show 112
Listen To Pronk Pops Podcast or Download Shows 108-111
Listen To Pronk Pops Podcast or Download Shows 106-108
Listen To Pronk Pops Podcast or Download Shows 104-105
Listen To Pronk Pops Podcast or Download Shows 101-103
Listen To Pronk Pops Podcast or Download Shows 98-100
Listen To Pronk Pops Podcast or Download Shows 94-97
Listen To Pronk Pops Podcast or Download Shows 93
Listen To Pronk Pops Podcast or Download Shows 92
Listen To Pronk Pops Podcast or Download Shows 91
Listen To Pronk Pops Podcast or Download Shows 88-90
Listen To Pronk Pops Podcast or Download Shows 84-87
Listen To Pronk Pops Podcast or Download Shows 79-83
Listen To Pronk Pops Podcast or Download Shows 74-78
Listen To Pronk Pops Podcast or Download Shows 71-73
Listen To Pronk Pops Podcast or Download Shows 68-70
Listen To Pronk Pops Podcast or Download Shows 65-67
Listen To Pronk Pops Podcast or Download Shows 62-64
Listen To Pronk Pops Podcast or Download Shows 58-61
Listen To Pronk Pops Podcast or Download Shows 55-57
Listen To Pronk Pops Podcast or Download Shows 52-54
Listen To Pronk Pops Podcast or Download Shows 49-51
Listen To Pronk Pops Podcast or Download Shows 45-48
Listen To Pronk Pops Podcast or Download Shows 41-44
Listen To Pronk Pops Podcast or Download Shows 38-40
Listen To Pronk Pops Podcast or Download Shows 34-37
Listen To Pronk Pops Podcast or Download Shows 30-33
Listen To Pronk Pops Podcast or Download Shows 27-29
Listen To Pronk Pops Podcast or Download Shows 17-26
Listen To Pronk Pops Podcast or Download Shows 16-22
Listen To Pronk Pops Podcast or Download Shows 10-15
Listen To Pronk Pops Podcast or Download Shows 01-09
Segment 0: Enemy Of The State: Life Imitating Art –National Security Agency Targets American People — Vidoes
ENEMY OF THE STATE… (1998) MUST WATCH..TAKE SERIOUSLY..
Nova: The Spy Factory Full Video
INTERVIEW with NSA WHISTLEBLOWER: Confirm EVERYONE in US is under VIRTUAL SURVEILLANCE since 9/11
He told you so: Bill Binney talks NSA leaks
James Bamford on NSA Leaks – Charlie Rose 06/13/2013
Companies With Ties to Israel Wiretap the U.S. for the NSA
James Bamford: Inside the NSA’s Largest Secret Domestic Spy Center
James Bamford on NSA’s un democratic Surveillance
Enemy of the State
Enemy of the State is a 1998 American action-thriller about a group of rogue NSA agents who kill a US Congressman and try to cover up the murder. It was written by David Marconi, directed by Tony Scott, and produced by Jerry Bruckheimer. It stars Will Smith and Gene Hackman, with Jon Voight, Lisa Bonet, and Regina King in supporting roles.
The film grossed over $250,000,000 worldwide ($111,549,836 within the US).
Plot
As the U.S. Congress moves to pass new legislation that dramatically expands the surveillance powers of intelligence agencies, Congressman Phil Hammersley (Robards) remains firmly opposed to its passage. To ensure the bill’s passage, National Security Agency official Thomas Reynolds (Voight) kills Hammersley, but he is unaware of a video camera set up by wildlife researcher Daniel Zavitz (Lee) that has captured the entire incident. Zavitz discovers the murder, and alerts an underground journalist, at the same time transferring the video to an innocuous computer disc. Reynolds learns of Zavitz’s footage, and sends a team to recover the video. While fleeing, Zavitz runs into an old college friend, labor lawyer Robert Clayton Dean (Smith). Zavitz secretly passes the computer disc into Dean’s shopping bag without his knowledge. Zavitz flees and is killed when hit by a fire truck. Reynolds soon has the underground journalist killed.
When the NSA discovers that Dean may have the video, a team raids his house and plants surveillance devices. Unable to find the video, the NSA proceeds to falsely incriminate Dean of passing classified information to Rachel Banks (Bonet), a former girlfriend. The subterfuge destroys Dean’s life: he is fired from his job, his bank accounts are frozen, and his wife (King) throws him out of the house. Dean, trailed by the NSA, meets with Banks, who sets up a meeting with “Brill”, one of her secret contacts. After meeting an NSA agent posing as Brill (Byrne), Dean realizes his error, only to have the real Brill, retired NSA agent Edward Lyle (Hackman), ferry him to temporary safety and help rid Dean of most of the tracking devices he is unwittingly carrying. Dean ultimately rids himself of the final device and, fleeing his pursuers, escapes.
With Dean and Lyle in hiding, the NSA agents kill Banks and frame Dean for the murder. Lyle is able to find evidence that the NSA executed Hammersley’s murder, but it is destroyed during an escape from an NSA raid.
It is then revealed that Lyle was an expert in communications for the NSA; he was stationed in Iran before the Iranian Revolution. When the revolution occurred, Lyle made it out of the country, but his partner, Rachel’s father, was killed. Since then he has been in hiding. Lyle tries to coax Dean into trying to run away, but Dean is adamant about clearing his name.
Dean and Lyle blackmail another supporter of the surveillance bill, Congressman Sam Albert (Wilson), by videotaping him having an affair with his aide. Dean and Lyle “hide” bugs that Reynolds had used on Dean in Albert’s room so Albert will find them and have the NSA start an investigation. Lyle also deposits $140,000 into Reynolds’ bank account to make it appear that he is taking bribes.
Lyle contacts Reynolds to tell him he has the video of the Hammersley murder and asks to meet. Dean tells them that the Hammersley murder footage is in the hands of Mafia boss Joey Pintero (Sizemore), whose office is under FBI surveillance. Dean, Reynolds, and the NSA team head into Pintero’s restaurant, precipitating a gunfight that kills the mobsters, Reynolds, and several of his NSA team.
Dean and Lyle escape, with Lyle quickly disappearing from the authorities. The FBI discovers the plot behind the legislation, causing it to fail, though they cover up the NSA’s involvement. Dean is cleared of all charges and is reunited with his wife. Lyle escapes to a tropical location, but sends a “goodbye” message to Dean.
Cast
- Will Smith as Robert Clayton Dean
- Gene Hackman as Edward “Brill” Lyle
- Jon Voight as Thomas Brian Reynolds
- Barry Pepper as David Pratt
- Regina King as Carla Dean
- Ian Hart as John Bingham
- Lisa Bonet as Rachel F. Banks
- Jascha Washington as Eric Dean
- James LeGros as Jerry Miller
- Jake Busey as Krug
- Scott Caan as Jones
- Jamie Kennedy as Jamie Williams
- Jason Lee as Daniel Leon Zavitz
- Gabriel Byrne as Fake Brill
- Stuart Wilson as Congressman Sam Albert
- Jack Black as Fiedler
- Anna Gunn as Emily Reynolds
- Laura Cayouette as Christa Hawkins
- Loren Dean as Loren Hicks
- Bodhi Elfman as Van
- Dan Butler as NSA Director Admiral Shaffer
- Seth Green as Selby (uncredited)
- Tom Sizemore as Boss Paulie Pintero (uncredited)
- Jason Robards as Congressman Phil Hammersley (uncredited)
- Philip Baker Hall as Attorney Mark Silverberg (uncredited)
- Brian Markinson as Attorney Brian Blake (uncredited)
- Larry King as Himself (uncredited)
- Ivana Miličević as Ruby’s Sales Clerk
Production
Although the story is set in both Washington, D.C., and Baltimore, most of the filming was done in Baltimore. Location shooting began on a ferry in Fells Point. In mid-January, the company moved to Los Angeles to complete production in April 1998.[3]
Mel Gibson and Tom Cruise were considered for the part that went to Will Smith, who took the role largely because he wanted to work with Gene Hackman and had previously enjoyed working with producer Jerry Bruckheimer on Bad Boys. George Clooney was also considered for a role in the film. Sean Connery was considered for the role that went to Hackman. The film’s crew included a technical surveillance counter-measures consultant who also had a minor role as a spy shop merchant. Hackman had previously acted in a similar thriller about spying and surveillance film, The Conversation (1974).
Reception
Enemy of the State was moderately well received by critics. Rotten Tomatoes presented a 71% “Fresh” rating for the movie, with 57 critics approving of the movie and 24 noting the film as “Rotten;”[4] similar results could be found at the website Metacritic, which displayed a normalized ranking of 67 out of 100 on the basis of the views of 22 critics.[5] Kenneth Turan of the Los Angeles Times expressed enjoyment in the movie, noting how its “pizazz [overcame] occasional lapses in moment-to-moment plausibility;”[6] Janet Maslin of the New York Times approved of the film’s action-packed sequences, but cited how it was similar in manner to the rest of the members of “Simpson’s and Bruckheimer’s school of empty but sensation-packed filming.”[7] In a combination of the two’s views, Edvins Beitiks of the San Francisco Examiner praised many of the movie’s development aspects, but criticized the overall concept that drove the film from the beginning — the efficiency of government intelligence — as unrealistic.[8]
According to film critic Kim Newman, Enemy of the State could be construed as a “continuation of The Conversation,” the 1974 psychological thriller that starred Hackman as a paranoid, isolated surveillance expert.[9]
Box office
The film opened at #2, behind The Rugrats Movie, grossing $20,038,573 over its first weekend in 2,393 theatres and averaging about $8,374 per venue.[10][11]
Real life
An episode of PBS’ Nova titled “Spy Factory” reports that the film’s portrayal of the NSA’s capabilities are fiction: although the agency can intercept transmissions, connecting the dots is difficult.[12] However, in 2001, then-NSA director Gen. Michael Hayden, who was appointed to the position during the release of the film, told CNN’s Kyra Philipps that “I made the judgment that we couldn’t survive with the popular impression of this agency being formed by the last Will Smith movie.[13]” James Risen wrote in his 2006 book State of War: The Secret History of the CIA and the Bush Administration that Hayden “was appalled” by the film’s depiction of the NSA, and sought to counter it with a PR campaign on behalf of the agency.[14]
In June 2013 the NSA’s PRISM and Boundless Informant programs for domestic and international surveillance were uncovered by the Guardian and Washington Post as the result of information provided by whistleblower Edward Snowden. This information revealed much more extensive capabilities than those represented by the film, such as collection of internet browsing, email and telephone data of not only every American, but citizens of other nations as well. The Guardian’s John Patterson opined that Hollywood depictions of NSA surveillance, including Enemy of the State and Echelon Conspiracy, had “softened” up the American public to “the notion that our spending habits, our location, our every movement and conversation, are visible to others whose motives we cannot know.[15]“
http://en.wikipedia.org/wiki/Enemy_of_the_State_%28film%29
Related Posts On Pronk Palisades
Big Brother Barack Targets All The American People As Enemies of The State and Democratic Party — National Security Agency’s PRISM Is The Secret Security Surveillance State (S4) Means of Invading Privacy and Limiting Liberty — Outrageous Overreach–Videos
No Such Agency — NSA — National Security Agency — Threat To The Liberty and Privacy of The American People — None Of Their Damn Business — Still Trust The Federal Government? — Videos
National Security Agency (NSA) and Federal Bureau Investigation (FBI) Secret Security Surveillance State (S4) Uses Stellar Wind and PRISM To Create Secret Dossiers On All American Citizen Targets Similar To East Germany Stasi Files–Videos
NSA’s PRISM Political Payoff: 40 Million Plus Foreigners Are In USA As Illegal Aliens! — 75% Plus Lean Towards Democratic Party — Pathway To One Party Rule By 2025 If Senate Bill Becomes Law Giving Illegal Aliens Legal Status — 25 Million American Citizens Looking For Full Time Jobs! — Videos
Read Full Post | Make a Comment ( None so far )Pronk Pops Shows 1-27–Podcasts or Download–Give It A Listen!
Posted on May 12, 2011. Filed under: American History, Budgetary Policy, Climate Change, Coal, College, Economics, Education, Energy, European History, Federal Government, Fiscal Policy, Government, Government Spending, Labor Economics, Monetary Policy, Oil, Philosophy, Politics, Private Sector Unions, Public Sector Unions, Radio, Resources, Sports, Tax Policy, Unions, Videos, Violence, War, Wisdom | Tags: Atlas Shrugged, Ayn Rand, Barack Obama, Baseball, Battle of the Budget, Ben Bernanke, Black History Month, BLS, Brooklyn Dodgers, Cap and Tax, Carbon Dioxide Emissions, Climate Change, Conservative Movement, CPI, Deficit Spending, Depression, Duke Snider, Earthquake, Economics, Employment, Energy, Eva Cassidy, Films, Fiscal Policy, Flat Tax, Fukushima Daiichi, Glenn Beck, Global Warming, Japan, John Boehner, Julian Assange, Marco Rubio, Misery Index, Monetary Policy, Movies, Music, National Debt, National Debt Ceiling, Nuclear Plants, Obama Misery Index, Oil, OMI, Peace, Podcasts, Politics, Power Outages, President Obama, Progressives, Prosperity, Public Finance, Rand Paul, Recession, Ron Paul, Shooting At University of Texas at Austing, Sidney Lumet, Talk Radio, Taxes, Tea Party, Tea Party Movement, The FairTax, The Fed, The Federal Reserve System, TSA, Unemployment, Videos, War, WikiLeaks |
Listen To Pronk Pops Podcast or Download Shows 27
Listen To Pronk Pops Podcast or Download Shows 22 (Part 2)-26
Listen To Pronk Pops Podcast or Download Shows 16-22 (Part 1)
Listen To Pronk Pops Podcast or Download Shows 10-15
Listen To Pronk Pops Podcast or Download Shows 1-9
Pronk Pops Show 27
May 11, 2011 10:13 AM PDT
Pronk Pops Show 27, May 10, 2011
Segment 1: Bureau of Labor Statistics Official Unemployment Rate (U-3) Increased To 9.0% With 13.7 Million Americans Unemployed and Total Unemployment Rate (U-6) Increased To 15.9% With 24.4 Million Americans Seeking Full Time Job–Economy Adds 244,000 Jobs But Initial Unemployment Claims Hit Eight Month High of 474,000!–Videos
For additional information and videos:
Segment 2: OMI-Obama Misery Index–U.S. Misery Index Is Rising As Both The Unemployment Rate and Inflation Rate Increase!–Videos
For additional information and videos:
Segment 3: Segment 3: Speaker Boehner’s Address to the Economic Club of New York on Jobs, Debt, Gas Prices–Videos
For additional information and videos:
Pronk Pops Show 26
April 27, 2011 11:28 AM PDT
Pronk Pops Show 25, April 26, 2011
Segment 0: Eva Cassidy–A Singer’s Singer
Segment 1: Ron Paul Is Running For President of The United States In 2012!–The Third Time Is The Charm–A Man Of Integrity–A Candidate For Peace and Prosperity–Neither A Big Government Warfare Republican Nor A Massive Government Welfare Democrat–A Man Of And For The American People–A Tea Party Patriot–Ron Paul–Videos
For additional information and videos:
Segment 3: President Obama Is The Reason Your Gasoline Prices Are Going Up!–American People Favor Drilling For Oil and Gas!–Drill Baby Drill–Videos
For additional information and videos:
Pronk Pops Show 24
Pronk Pops Show 24: April 19, 2011
Segment 0: S&P Rating Outlook Changed From “Stable” To “Negative” For U.S. Treasury Debt–Videos
Segment 1: Who is John Galt? Who is Ayn Rand–Videos
For additional information and videos:
Segment 2: President Obama’s Fiscal Year 2012 Budget Speech Of April 13, 2011–Eat The Rich And Killing The American Dream Class Warfare–Cuts National Security Spending and Raise Taxes On The Rich–Produces Massive Deficits, National Debt, and Higher Unemployment For 12 More Years–Progressive Radical Socialist Economic Stagflation–Videos
For additional information and videos:
https://pronkpops.wordpress.com/2011/04/18/pronk-pops-show-24-april-18-2011-segment-2-president-obamas-fiscal-year-2012-budget-speech-of-april-13-2011-eat-the-rich-and-killing-the-american-dream-class-warfare-cuts-national-security-sp/
Segment 3: The FairTax (National Consumption Sales Tax) vs. The Flat Tax (One Rate Federal Income Tax)–Who Pays The Most Federal Individual Income Tax? Videos
For additional information and videos:
Pronk Pops Show 23
Pronk Pops Show 23: April 12, 2011
Segment 0: Sidney Lumet–Rest In Peace–Videos
Segment 1: Tea Party Movement Demands Passage of Balanced Budget Amendment and The FairTax As The Price For Raising The National Statutory Debt Limit of $ 14,294,000,000 One Last Time By $1,000,000,000,000!–Videos
For additional information and videos:
Segment 2: The FairTax (National Consumption Sales Tax) vs. The Flat Tax (One Rate Federal Income Tax)–Who Pays The Most Federal Individual Income Tax? Videos
For additional information and videos:
Pronk Pops Show 22 (Part 2)
Pronk Pops Show 22, April 7, 2011
Segment 1: 3,500,000 Million Americans Unemployed in March 2011 Still Exceeds Great Depression High of 13,000,000 In March 1933–The Obama Depressions Continues–Bureau of Labor Statistics: 8.8% Official Unemployment Rate (U-3) vs. Gallup Unemployment Rate of 10.0%–Nonfarm Payroll Increased By 216,000–The Government Makes The Depression Worse!–Videos
Segment 2: Obama’s Anti-American, Anti-Capitalist, Anti-Growth, Anti-Jobs, and Anti-Security Energy Policy–Videos
Segment 3: Republican Establishment Will Propose A Ten Year $6,200 Billion Cut In Spending Over Ten Years–The Problem Is It Does Not Balance The Budget For Another Five Years At The Earliest–Tea Party Movement Demands Balanced Budgets Starting In 2012 For The Next Ten Years!–A Jet Plane To Prosperity Not A Path To Prosperity–Videos
Segment 4: Just One More Thing Congressman Ryan: When Does The Republican’s Path To Prosperity Balance The Budget?–The Twelth of Never!–Videos
For additional information and videos on the above segments:
Pronk Pops Show 22 (Part 1)
Pronk Pops: Show 22, April 7, 2011
Segment 0: Glenn Beck Ending His Show At Fox News
Segment 1: 3,500,000 Million Americans Unemployed in March 2011 Still Exceeds Great Depression High of 13,000,000 In March 1933–The Obama Depressions Continues–Bureau of Labor Statistics: 8.8% Official Unemployment Rate (U-3) vs. Gallup Unemployment Rate of 10.0%–Nonfarm Payroll Increased By 216,000–The Government Makes The Depression Worse!–Videos
Segment 2: Obama’s Anti-American, Anti-Capitalist, Anti-Growth, Anti-Jobs, and Anti-Security Energy Policy–Videos
Segment 3: Republican Establishment Will Propose A Ten Year $6,200 Billion Cut In Spending Over Ten Years–The Problem Is It Does Not Balance The Budget For Another Five Years At The Earliest–Tea Party Movement Demands Balanced Budgets Starting In 2012 For The Next Ten Years!–A Jet Plane To Prosperity Not A Path To Prosperity–Videos
Segment 4: Just One More Thing Congressman Ryan: When Does The Republican’s Path To Prosperity Balance The Budget?–The Twelth of Never!–Videos
For additional information and videos on the above segments:
Pronk Pops Show 21
Pronk Pops Show 21, March 29, 2010
Segment 1: The Truth And Consequences About Undeclared Wars–Real Strange Bedfellows–Obama Allies U.S. with Libyan Rebels Including Islamic Jihadists, Moslem Brotherhood, and Al-Qaeda!–Give Peace A Chance–AC-130 Gunship–A-10 Warthogs–F-15E Strike Eagles and Special Operation Smash Squads
For Additional Information and Videos:
Pronk Pops Show 20
Pronk Pops Show 20: March 22, 2011
Segment 1:F-15 Crashes In Libya
Segment 2![]() ne Unconstitutional and Undeclared War Too Many: The Great Pretender, Peace Candidate And Noble Peace Prize Winner, President Barack Obama Undeclared War On Libya’s Muammar Ghaddafi In Defense Of Libyian Islamic Fighting Group (LIFG) Rebels Linked To al-Qaeda and The BP Libyian Oil Deal Linked To Obama Campaign Contributions–A Political Payoff!–Obama Has To Go In 2012–Videos
ne Unconstitutional and Undeclared War Too Many: The Great Pretender, Peace Candidate And Noble Peace Prize Winner, President Barack Obama Undeclared War On Libya’s Muammar Ghaddafi In Defense Of Libyian Islamic Fighting Group (LIFG) Rebels Linked To al-Qaeda and The BP Libyian Oil Deal Linked To Obama Campaign Contributions–A Political Payoff!–Obama Has To Go In 2012–Videos
Segment 3:Earthquake Damages Japanese Nuclear Plant At Fukushima Daiichi, Four Explosions and Four Nuclear Reactors Flooded With Seawater To Contain Release Of Radioactive Material and Plant Released Radioactive Materials To Stop Pressure Buildup–Partial Meltdown Of Nuclear Core Feared–Radioactive Material Escaping From Plant–Over 250,000 Ordered Evacuated From 20 Kilometer (12.4 Miles) Radius From Plant–Videos
For Additional Information and Videos:
Pronk Pops Show 19
Pronk Pops Show 19: March 8, 2011
Segment 1: The Washington Political Elites of Both Parties Are Not Serious About Balancing The Federal Budget And Funding Entitlement Liabilities–Send In The Clowns–Don’t Bother There Here–Videos
Segment 2, Gallup–U.S. Unemployment Hits 10.3% In February 2011 Vs. Bureau of Labor Statistics (BLS) U.S. Unemployment Rate Declined By .1% To 8.9% in February 2011 With Job Creation of 192,000 In February 2011–Over 13.7 Million Americans Unemployed More Than Worse Month of Great Depression!
For more information and videos related to this show click on links below:
Pronk Pops Show 18
Pronk Pops Show 18: March 3, 2011
Segment 1: Remembering The Brooklyn Dodgers and Duke Snider
Segment 2: The National Debt Will Hit $20,000,000,000,000 By 2020!
Segment 3 Public Sector Unions vs. The America People: Replacing The American Dream With The Socialist Union Nightmare
For additional information and videos on the above segments:
Pronk Pop Show 17
Pronk Pops Show 17: February 22, 2011
Black History Month–Progressives–Eugenics–Black Population Control–Abortion–Black Genocide–Planned Parenthood–Barack Obama
For more information and videos relating to the show:
Pronk Pops Show 16
Pronk Pops Show 16: February 15, 2011
Conservative Political Action Conference 2011
President Obama’s Saint Valentine’s Massacre of The American People–Fiscal Year 2012 Budget Buster–Spending $3,729 Billion–Taxes $2,627 Billion–Deficit $1,101 Billion–Dead On Arrival–DOA– 3 Million Tea Party Patriots To March On Washington D.C. On Friday, April 15, 2011 In Protest!
For more information and videos related to this show click on link below:
Pronk Pops Show 15: Hour 3
Pronk Pops Show 15:February 8,2011, Hour 3
Lies, Damn Lies, Statistics, and Obama’s Unbelievable Unemployment Numbers
For more information and videos related to this show click on link below:
Pronk Pops Show 15: Hour 2
Pronk Pops Show 15: February 8, 2011 Hour 2
Rolling Power Outages in Texas
Obama Care Declared Unconstitutional and Void By Federal Judge
For more information and videos related to this show click on link below:
Pronk Pops Show 15: Hour 1
Pronk Pops Show 15: February 8,2011, Hour 1
Super Storm and Super Bowl In Dallas, Texas
Man-Made Carbon Dioxide Emission and Global Warming–Science vs. Politics
For more information and videos related to this show click on link below:
Pronk Pops Show 14
Pronk Pops Show 14: January 27, 2011
The Big Lie and Free Speech
President Obama’s State of the Union Campaign Speech
For more information and videos related to this show click on link below:
Pronk Pops Show 13
Pronk Pops Show 13: December 9, 2010
Latest News Update on WikiLeaks
Federal Reserve Unconventional Monetary Policy
President Obama and Republicans Agree To Two Year Tax Rate Extension and
One Year Unemployment Benefit Extension–More Deficit Spending and Debt!
For more information and videos related to this show click on link below:
Pronk Pops Show 12
Pronk Pops Show 12: December 8, 2010
News Update On WikiLeaks and Julian Assange
The Chairman of The Federal Reserve and Quantitative Easing 2
For more information and videos related to this show click on link below:
Pronk Pops Show 11
Pronk Pops Show 11: December 3, 2010
News and Commentary On November 2010 Unemployment Rate and Level Statistics
WikiLeaks
For more information and videos related to this show click on link below:
Pronk Pops Show 10
Pronk Pops Show 10: December 1, 2010
Update on new TSA Airport Screening Procedures
Portland, Oregon Terrorist Bomber Arrested by F.B.I.
WikiLeaks Posts Department of State Cables
For more information and videos related to this show click on link below:
https://pronkpops.wordpress.com/2010/11/24/pronk-pops-show-10-november-24-2010-food-prices-rising-fairtax-updates-on-tsa-and-quantitative-easing-money-printing-videos/
Pronk Pops Show 9
Pronk Pops Show 9: November 19, 2010
Federal Reserve Chairman Bernanke Responds To Critics of Monetary Policy
Transportation Security Administration or TSA New Screening Procedures:
Full Body Scanners and Extended Pat-Downs
For more information and videos related to this show click on link below:
Pronk Pops Commentary 1
Pronk Pops Commentary 1: November 11, 2010
Stop Federal Reserve Quantitative Easing or Money Printing
Pronk Pops Show 8
Pronk Pops Show 8: November 10, 2010
Tea Party Major Issues: Jobs, Spending, Deficits, Debt, Taxes, Health Care and Illegal Immigration
Tea Party Stars: Senators: Rand Paul and Marco Rubio
Republican Tea Party Test: Cutting Federal Spending By Over $1,000 Billion To Balance The Budget For Fiscal Years 2011, 2012, and 2013.
For more information and videos related to this show click on link below:
Pronk Pops Show 7
Pronk Pops Show 7: November 9, 2010
Unemployment News
Tea Party Effect On 2010 Elections
Key Issues: Federal Budget Deficits and National Debt
Cutting Federal Government Spending and Balancing The Federal Budget
For more information and videos related to this show click on link below:
Pronk Pops Show 6
Pronk Pops Show 6: November 3, 2010
Winning Elections With MOMMA (Money, Organization, Message, Momentum, Ambition) and The Tea Party Movement Effect
For more information and videos related to this show click on link below:
Pronk Pops Show 5
Pronk Pops Show 5: October 27, 2010
Democratic Party’s National Attack Ad Campaign on Candidates and the Flat Tax
For more information and videos related to this show click on link below:
Pronk Pops Show 4
Pronk Pops Show 4: October 20, 2010
Money, Quantitative Easing and Inflation in the United States Economy
For more information and videos related to this show click on link below:
Pronk Pops Show 3
Pronk Pops Show 3: October 14, 2010
Unemployment and inflation in the United States economy
For more information and videos related to this show click on link below:
Pronk Pops Show 2
Pronk Pops Show 2: October 13, 2010
The 10:10 carbon emission ad campaign on climate change
http://www.youtube.com/watch?v=wliC2Eiwoyw
Secretary of State Hillary Clinton replacing Vice President Joseph Biden on the 2010 Democratic Party ticket
For more information and videos related to this show click on link below:
Pronk Pops Show 1
Pronk Pops Show 1: September 29, 2010
University of Texas at Austin shooting/suicide
The Tea Party Movement in the United States
For more information and videos related to this show click on link below:
Listen To Pronk Pops Podcast or Download Shows 27
Listen To Pronk Pops Podcast or Download Shows 22 (Part 2)-26
Listen To Pronk Pops Podcast or Download Shows 16-22 (Part 1)
Listen To Pronk Pops Podcast or Download Shows 10-15
Listen To Pronk Pops Podcast or Download Shows 1-9
Read Full Post | Make a Comment ( None so far )Pronk Pops Show 24: April 19, 2011, Segment 0: S&P Rating Outlook Changed From “Stable” To “Negative” For U.S. Treasury Debt–Videos, Segment 1: Who is John Galt? Who is Ayn Rand–Videos
Posted on April 17, 2011. Filed under: American History, Budgetary Policy, Business, Crime, Culture, Economics, Education, European History, Federal Government, Fiscal Policy, Government, Government Spending, History, Labor Economics, Monetary Policy, Philosophy, Politics, Private Sector Unions, Public Sector Unions, Radio, Tax Policy, Unions, Videos, War, Wisdom | Tags: America, Art, Atlas Shrugged, Ayn Rand, Books, Capitalism, Collectivism, Communications, Culture, Films, Freedom, Individualism, John Galt, Liberty, Literature, Movies, Philosophy, Socialism, The Fountainhead, Videos |
Pronk Pops Show 24: April 19, 2011
Pronk Pops Show 23: April 12, 2011
Pronk Pops Show 22 (Part 2): April 7, 2011
Pronk Pops Show 22 (Part 1): April 7, 2011
Listen To Pronk Pops Podcast or Download Shows 22 (Part 2)-24
Listen To Pronk Pops Podcast or Download Shows 16-22 (Part 1)
Listen To Pronk Pops Podcast or Download Shows 10-15
Listen To Pronk Pops Podcast or Download Shows 1-9
Segment 0: S&P Rating Outlook Changed From “Stable” To “Negative” For U.S. Treasury Debt–Videos
U.S. Debt Clock
http://www.usdebtclock.org/
U.S. Debt Rating Drops to “Negative”
Why Did S&P Issue Warning on US Bond Rating?
Stocks Tumble after US Outlook Downgraded; Ron Paul Discusses
S&P Lowers U.S. Debt Outlook To “Negative”
S&P Downgrades U.S. Debt Rating to “Negative”
Fink Calls S&P U.S. Outlook Cut a `Warning’ to Lawmakers
Taxation is Theft
MacGuineas Says U.S. Should Take S&P Action Seriously
Eizenstat Says S&P Action a `Political Warning’ for U.S.
Standard and Poor’s
“….Credit Ratings Definitions & FAQs
Credit ratings are forward-looking opinions about credit risk. Standard & Poor’s credit ratings express the agency’s opinion about the ability and willingness of an issuer, such as a corporation or state or city government, to meet its financial obligations in full and on time.
Credit ratings can also speak to the credit quality of an individual debt issue, such as a corporate note, a municipal bond or a mortgage-backed security, and the relative likelihood that the issue may default.
Ratings are provided by organizations such as Standard & Poor’s, commonly called credit rating agencies, which specialize in evaluating credit risk.
Each agency applies its own methodology in measuring creditworthiness and uses a specific rating scale to publish its ratings opinions. Typically, ratings are expressed as letter grades that range, for example, from ‘AAA’ to ‘D’ to communicate the agency’s opinion of relative level of credit risk.
For more information view the detailed Ratings Definitions
What do the letter ratings mean?
Are Credit Ratings indicators of investment merit?
Are Credit Ratings absolute measures of default probability?
What do the letter ratings mean?
The general meaning of our credit rating opinions is summarized below.
‘AAA’—Extremely strong capacity to meet financial commitments. Highest Rating.
‘AA’—Very strong capacity to meet financial commitments.
‘A’—Strong capacity to meet financial commitments, but somewhat susceptible to adverse economic conditions and changes in circumstances.
‘BBB’—Adequate capacity to meet financial commitments, but more subject to adverse economic conditions.
‘BBB-‘—Considered lowest investment grade by market participants.
‘BB+’—Considered highest speculative grade by market participants.
‘BB’—Less vulnerable in the near-term but faces major ongoing uncertainties to adverse business, financial and economic conditions.
‘B’—More vulnerable to adverse business, financial and economic conditions but currently has the capacity to meet financial commitments.
‘CCC’—Currently vulnerable and dependent on favorable business, financial and economic conditions to meet financial commitments.
‘CC’—Currently highly vulnerable.
‘C’—Currently highly vulnerable obligations and other defined circumstances.
‘D’—Payment default on financial commitments.
Note: Ratings from ‘AA’ to ‘CCC’ may be modified by the addition of a plus (+) or minus (-) sign to show relative standing within the major rating categories.
http://www.standardandpoors.com/ratings/gfir/en/us
DoubleLine says S&P warning “good” for US debt
By Jennifer Ablan
“…S&P revised its outlook on the United States’ AAA credit rating to negative from stable, citing the country’s deteriorating fiscal position. The shift reflects the rating agency’s belief that there is a one in three chance that the U.S. credit rating could be downgraded within two years.
Mohamed El-Erian, the co-chief investment officer at PIMCO, told Reuters Insider television that the S&P warning reflects the United States’ deteriorating standing in the global economy.
“The U.S. risks losing their AAA rating under our internal ratings,” El-Erian said. He added that the $1.2 trillion fund will continue to avoid long-term U.S. Treasuries, particularly at these “low” yield levels. Benchmark 10-year yields fell to 3.37 percent, marking the lowest since March 24. …”
http://www.reuters.com/article/2011/04/18/us-ratings-usa-gundlach-idUSTRE73H48Z20110418
A surprise warning about U.S. debt by credit rating agency Standard & Poor’s sent stocks plunging Monday and crystallized the threat that mounting federal budget deficits and national debt pose to the U.S. financial system and the American way of life.
“…S&P maintained the coveted AAA rating on U.S. government debt, but switched its outlook from stable to negative, a sign that the ratings agency has doubts about Washington’s prospects for taking effective action to curb deficits and debt.
“The negative outlook on our rating on the U.S. sovereign signals that we believe there is at least a one-in-three likelihood that we could lower our long-term rating on the U.S. within two years,” S&P analysts noted in their credit report. “The outlook reflects our view of the increased risk that the political negotiations over when and how to address both the medium- and long-term fiscal challenges will persist until at least after national elections in 2012.” …”
“…Question: What is Standard & Poor’s, and why does its opinion matter?
Answer: S&P is a nationally recognized statistical rating organization. It rates debt, in this case U.S. Treasury bonds, in terms of the risk of default they pose to investors in them. U.S. government securities have long enjoyed the top AAA rating but are now viewed as at risk for a downgrade of creditworthiness.
Q: Why would a downgrade affect borrowing costs in the economy?
A: The ratings issued by S&P and its main competitors – Moody’s Investors Service and Fitch Ratings – are used by investors to calculate what sort of return they should demand in exchange for the default risk they assume when investing in a given security. A lower rating means a higher chance of default.
The issuer, in this case the U.S. government, would have to pay a higher interest rate to investors to market its lower-rated bonds. Since the government must borrow to pay off existing debt, the cost of that would snowball into an even more costly fix for our fiscal problems. …”
S&P’s Credibility Under Fire As Agency Issues US Debt Warning
“…, just last week a Senate investigations subcommittee ripped Standard & Poor’s in a comprehensive report on the financial meltdown. The bipartisan report — issued by Sen. Carl Levin, D-Mich., and Sen. Tom Coburn, R-Okla. — in part blamed S&P for the crisis, saying the agency had inflated ratings on mortgage-backed securities for their own profit, only to later downgrade those ratings, destroying the value of the securities and contributing to the crisis.
“It was not in the short-term economic interest of either Moody’s or S&P, however, to provide accurate credit ratings for high-risk RMBS and CDO securities, because doing so would have hurt their own revenues,” Levin and Coburn said in their report. “Instead, the credit rating agencies’ profits became increasingly reliant on the fees generated by issuing a large volume of structured finance ratings.”
In short, the senators say, “Inaccurate AAA credit ratings introduced risk into the U.S. financial system and constituted a key cause of the financial crisis.”
The credibility of S&P is especially significant in the wake of the rating agency’s statement on Monday that it was starting to lose faith in the government’s creditworthiness. While S&P maintained its best-possible AAA rating for US federal debt, the firm lowered its outlook from “stable” to “negative.” The statement means the agency now thinks there is a one-in-three chance that it will reduce the rating of the bonds in the next few years. …”
“We view President Obama’s and Congressman Ryan’s proposals as the starting point of a process aimed at broader engagement, which could result in substantial and lasting U.S. government fiscal consolidation,” S&P noted. “That said, we see the path to agreement as challenging because the gap between the parties remains wide. We believe there is a significant risk that Congressional negotiations could result in no agreement on a medium-term fiscal strategy until after the fall 2012 Congressional and Presidential elections.”
http://abcnews.go.com/Politics/standard-poors-credibility-fire-us-debt-warning/story?id=13407823
Background Articles and Videos
Senator Rand Paul on balancing the budget
Sen. Rand Paul Introduces Five-Year Balanced Budget Plan
Shelby Introduces Balanced Budget Amendment to Constitution
Which Budgets Are Fiscally Responsible?
Which Budgets Are Living Within Ones Means?
Democratic Party Budget Proposals
| S-1 FY2012 President’s Budget(Nominal Dollars in Billions) | ||||
| Fiscal Year | Outlays | Revenues | Deficits | Debt Held By Public |
| 2011 | 3,819 | 2,174 | -1,645 | 10,856 |
| 2012 | 3,729 | 2,627 | -1,101 | 11,881 |
| 2013 | 3,771 | 3,003 | -768 | 12,784 |
| 2014 | 3,977 | 3,333 | -646 | 13,562 |
| 2015 | 4,190 | 3,583 | -607 | 14,301 |
| 2016 | 4,468 | 3,819 | -649 | 15,064 |
| 2017 | 4,669 | 4,042 | -627 | 15,795 |
| 2018 | 4,876 | 4,257 | -619 | 16,513 |
| 2019 | 5,154 | 4,473 | -681 | 17,284 |
| 2020 | 5,442 | 4,686 | -735 | 18,103 |
| 2021 | 5,697 | 4,923 | -774 | 18,967 |
| 2012-2021 | 45,952 | 38,747 | -7,205 | n.a. |
http://www.whitehouse.gov/sites/default/files/omb/budget/fy2012/assets/tables.pdf
Republican Party Budget Proposals
| S-1 FY2012 Chairman’s Markup(Nominal Dollars in Billions) | ||||
| Fiscal Year | Outlays | Revenues | Deficits | Debt Held By Public |
| 2011 | 3,618 | 2,230 | -1,388 | 10,351 |
| 2012 | 3,529 | 2,533 | -995 | 11,418 |
| 2013 | 3,559 | 2,860 | -699 | 12,217 |
| 2014 | 3,586 | 3,094 | -492 | 12,801 |
| 2015 | 3,671 | 3,237 | -434 | 13,326 |
| 2016 | 3,858 | 3,377 | -481 | 13,886 |
| 2017 | 3,998 | 3,589 | -408 | 14,363 |
| 2018 | 4,123 | 3,745 | -379 | 14,800 |
| 2019 | 4,352 | 3,939 | -414 | 15,254 |
| 2020 | 4,544 | 4,142 | -402 | 15,681 |
| 2021 | 4,739 | 4,354 | -385 | 16,071 |
| 2012-2021 | 39,958 | 34,870 | -5,088 | n.a. |
http://budget.house.gov/UploadedFiles/PathToProsperityFY2012.pdf
Tea Party Budget Proposals
| S-1 FY2012 Tea Party’s Balanced/Surplus Budget(Nominal Dollars in Billions) | ||||
| Fiscal Year | Outlays | Revenues | Surpluses | Debt Held By Public |
| 2012 | 2,500 | 2,500 | 0 | 10,900 |
| 2013 | 2,800 | 2,800 | 0 | 10,900 |
| 2014 | 3,000 | 3,000 | 0 | 10,900 |
| 2015 | 3,200 | 3,200 | 0 | 10,900 |
| 2016 | 3,300 | 3,300 | 0 | 10,900 |
| 2017 | 3,400 | 3,500 | 100 | 10,800 |
| 2018 | 3,500 | 3,700 | 200 | 10,600 |
| 2019 | 3,600 | 3,900 | 300 | 10,300 |
| 2020 | 3,700 | 4,000 | 300 | 10,000 |
| 2021 | 3,800 | 4,300 | 500 | 9,500 |
| 2012-2021 | 32,800 | 34,200 | 1,400 | n.a. |
Milton Friedman on Libertarianism (Part 4 of 4)
The FairTax: It’s Time
Segment 1: Who is John Galt? Who is Ayn Rand–Videos
Rand-O-Rama: The Long Shelf Life of Ayn Rand’s Legacy
Atlas Shrugged Trailer
On the Set of Atlas Shrugged: 53 Years in the Making
Mr. Galt Goes to Washington: Ayn Rand’s Atlas Shrugged Premiers Among DC’s Capitalist Elite
Atlas Shrugged The Movie Part 1 Review
Who Is John Galt?
Why Atlas Shrugged Changes Lives
Atlas Shrugged and the Tea Party Revolts
The Relevance of Atlas Shrugged in Today’s World – Ayn Rand Center for Individual Rights
Ayn Rand Interview with Tom Snyder, (1 of 3)
Ayn Rand Interview with Tom Snyder, (2 of 3)
Ayn Rand Interview with Tom Snyder, (3 of 3)
1 of 2 Money, the root of all evil? Francisco d’Anconia
2 of 2 Money, the root of all evil? Francisco d’Anconia
John Galt Speech FULL part 1 of 3
John Galt Speech FULL part 2 of 3
John Galt Speech FULL part 3 of 3
AYN RAND’s message to AMERICA
Background Articles and Videos
Ayn Rand: A Sense of Life 01
Ayn Rand – A Sense of Life 02
Ayn Rand A Sense of Life 03
Ayn Rand – A Sense of Life 04
Ayn Rand – A Sense of Life 05
Ayn Rand – A Sense of Life 06
Ayn Rand – A Sense of Life 07
Ayn Rand – A Sense of Life 08
Ayn Rand – A Sense of Life 09
Ayn Rand – A Sense of Life 10
Atlas Shrugged Trailer
Ayn Rand & The World She Made: Q&A with Anne Heller
Anne Heller on Ayn Rand–SHORT VERSION on The Woman’s Connection®
Ayn Rand: Prophet or Scapegoat?
Nathaniel Branden on “My Years With Ayn Rand”
Barbara Branden on the Passion of Ayn Rand
‘Atlas Shrugged’ at Fifty | by Barbara Branden
Reason Foundation Co-Founder Tibor Machan on Ayn Rand
Reason Foundation Co-Founder Manny Klausner on Ayn Rand
Ayn Rand Grave
Related Posts On Pronk Palisades
Ayn Rand–Videos
Ayn Rand: A Sense Of Life–Videos
The Fountainhead, Atlas Shrugged and The Ideas of Ayn Rand
Francisco d’Anconia’s ‘Money Speech’ from Atlas Shrugged, by Ayn Rand–Videos
Yaron Brook On Capitalism and Atlas Shrugged–Videos
Jennifer Burns–Goddess of the Market: Ayn Rand and the American Right–Videos
Anne C. Heller–Ayn Rand And The World She Made–Videos
John Stossel On Ayn Rand’s Atlas Shrugged
Ayn Rand’s Howard Roark–Individualist–Replies To Barack Obama–Collectivist–Videos
WordPress Is At It Again In Censoring Posts–This Time On The April 15, 2011 Opening Of Atlas Shrugged Movie and March On Washington D.C.–Videos
Atlas Shrugged Part 1 Opens April 15, 2011–See The Movie and March On Washington D.C. For Tea Party Rally On April 15!–Videos
Read Full Post | Make a Comment ( None so far )Next Entries »



















































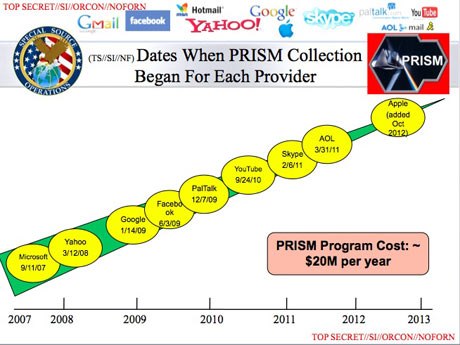
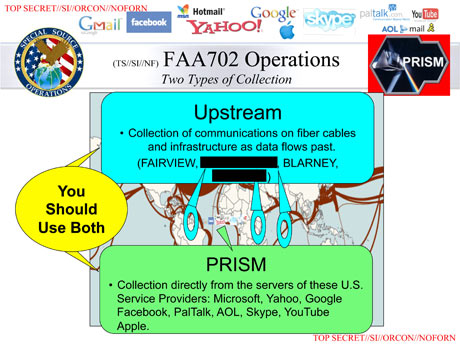




You must be logged in to post a comment.