The National Security Agency (NSA) is a military intelligence organization and a constituent of the United States Department of Defense (DOD). The NSA is responsible for global monitoring, collection, and processing of information and data for foreign intelligence and counterintelligence purposes, a discipline known as signals intelligence (SIGINT). NSA is concurrently charged with protection of U.S. government communications and information systems against penetration and network warfare.[8][9] Although many of NSA’s programs rely on “passive” electronic collection, the agency is authorized to accomplish its mission through active clandestine means,[10] among which are physically bugging electronic systems[11] and allegedly engaging in sabotage through subversive software.[12][13] Moreover, NSA maintains physical presence in a large number of countries across the globe, where its Special Collection Service (SCS) inserts eavesdropping devices in difficult-to-reach places. SCS collection tactics allegedly encompass “close surveillance, burglary, wiretapping, breaking and entering.”[14][15]
Unlike the Defense Intelligence Agency (DIA) and the Central Intelligence Agency (CIA), both of which specialize primarily in foreign human espionage, NSA does not unilaterally conduct human-source intelligence gathering, despite often being portrayed so in popular culture. Instead, NSA is entrusted with assistance to and coordination of SIGINT elements at other government organizations, which are prevented by law from engaging in such activities without the approval of the NSA via the Defense Secretary.[16] As part of these streamlining responsibilities, the agency has a co-located organization called the Central Security Service (CSS), which was created to facilitate cooperation between NSA and other U.S. military cryptanalysis components. Additionally, the NSA Director simultaneously serves as the Commander of the United States Cyber Command and as Chief of the Central Security Service.
Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Since then, it has become one of the largest U.S. intelligence organizations in terms of personnel and budget,[6][17] operating as part of the Department of Defense and simultaneously reporting to the Director of National Intelligence.
NSA surveillance has been a matter of political controversy on several occasions, such as its spying on anti-Vietnam-war leaders or economic espionage. In 2013, the extent of some of the NSA’s secret surveillance programs was revealed to the public by Edward Snowden. According to the leaked documents, the NSA intercepts the communications of over a billion people worldwide, many of whom are United States citizens, and tracks the movement of hundreds of millions of people using cellphones. Internationally, research has pointed to the NSA’s ability to surveil the domestic Internet traffic of foreign countries through “boomerang routing”.[18]
History
Army predecessor
The origins of the National Security Agency can be traced back to April 28, 1917, three weeks after the U.S. Congress declared war on Germany in World War I. A code and cipher decryption unit was established as the Cable and Telegraph Section which was also known as the Cipher Bureau. It was headquartered in Washington, D.C. and was part of the war effort under the executive branch without direct Congressional authorization. During the course of the war it was relocated in the army’s organizational chart several times. On July 5, 1917, Herbert O. Yardley was assigned to head the unit. At that point, the unit consisted of Yardley and two civilian clerks. It absorbed the navy’s cryptoanalysis functions in July 1918. World War I ended on November 11, 1918, and MI-8 moved to New York City on May 20, 1919, where it continued intelligence activities as the Code Compilation Company under the direction of Yardley.[19][20]
Black Chamber

Western Union allowed MI-8 to monitor telegraphic communications passing through the company’s wires until 1929.[21]
MI-8 also operated the so-called “Black Chamber“.[22] The Black Chamber was located on East 37th Street in Manhattan. Its purpose was to crack the communications codes of foreign governments. Jointly supported by the State Department and the War Department, the chamber persuaded Western Union, the largest U.S. telegram company, to allow government officials to monitor private communications passing through the company’s wires.[23]
Other “Black Chambers” were also found in Europe. They were established by the French and British governments to read the letters of targeted individuals, employing a variety of techniques to surreptitiously open, copy, and reseal correspondence before forwarding it to unsuspecting recipients.[24]
Despite the American Black Chamber’s initial successes, it was shut down in 1929 by U.S. Secretary of State Henry L. Stimson, who defended his decision by stating: “Gentlemen do not read each other’s mail”.[21]
World War II and its aftermath
During World War II, the Signal Security Agency (SSA) was created to intercept and decipher the communications of the Axis powers.[25] When the war ended, the SSA was reorganized as the Army Security Agency (ASA), and it was placed under the leadership of the Director of Military Intelligence.[25]
On May 20, 1949, all cryptologic activities were centralized under a national organization called the Armed Forces Security Agency (AFSA).[25] This organization was originally established within the U.S. Department of Defense under the command of the Joint Chiefs of Staff.[26] The AFSA was tasked to direct Department of Defense communications and electronic intelligence activities, except those of U.S. military intelligence units.[26] However, the AFSA was unable to centralize communications intelligence and failed to coordinate with civilian agencies that shared its interests such as the Department of State, Central Intelligence Agency (CIA) and the Federal Bureau of Investigation (FBI).[26] In December 1951, President Harry S. Truman ordered a panel to investigate how AFSA had failed to achieve its goals. The results of the investigation led to improvements and its redesignation as the National Security Agency.[27]
The agency was formally established by Truman in a memorandum of October 24, 1952, that revised National Security Council Intelligence Directive (NSCID) 9.[28] Since President Truman’s memo was a classified document,[28] the existence of the NSA was not known to the public at that time. Due to its ultra-secrecy the U.S. intelligence community referred to the NSA as “No Such Agency”.[29]
Vietnam War
In the 1960s, the NSA played a key role in expanding America’s commitment to the Vietnam War by providing evidence of a North Vietnamese attack on the American destroyer USS Maddox during the Gulf of Tonkin incident.[30]
A secret operation, code-named “MINARET“, was set up by the NSA to monitor the phone communications of Senators Frank Church and Howard Baker, as well as major civil rights leaders, including Martin Luther King, Jr., and prominent U.S. journalists and athletes who criticized the Vietnam War.[31] However, the project turned out to be controversial, and an internal review by the NSA concluded that its Minaret program was “disreputable if not outright illegal”.[31]
The NSA mounted a major effort to secure tactical communications among U.S. forces during the war with mixed success. The NESTOR family of compatible secure voice systems it developed was widely deployed during the Vietnam War, with about 30,000 NESTOR sets produced. However a variety of technical and operational problems limited their use, allowing the North Vietnamese to exploit intercepted U.S. communications.[32] :Vol I, p.79
Church Committee hearings
In the aftermath of the Watergate scandal, a congressional hearing in 1975 led by Sen. Frank Church[33] revealed that the NSA, in collaboration with Britain’s SIGINT intelligence agency Government Communications Headquarters (GCHQ), had routinely intercepted the international communications of prominent anti-Vietnam war leaders such as Jane Fonda and Dr. Benjamin Spock.[34] Following the resignation of President Richard Nixon, there were several investigations of suspected misuse of FBI, CIA and NSA facilities.[35] Senator Frank Church uncovered previously unknown activity,[35] such as a CIA plot (ordered by the administration of President John F. Kennedy) to assassinate Fidel Castro.[36] The investigation also uncovered NSA’s wiretaps on targeted American citizens.[37]
After the Church Committee hearings, the Foreign Intelligence Surveillance Act of 1978 was passed into law. This was designed to limit the practice of mass surveillance in the United States.[35]
From 1980s to 1990s
In 1986, the NSA intercepted the communications of the Libyan government during the immediate aftermath of the Berlin discotheque bombing. The White House asserted that the NSA interception had provided “irrefutable” evidence that Libya was behind the bombing, which U.S. President Ronald Reagan cited as a justification for the 1986 United States bombing of Libya.[38][39]
In 1999, a multi-year investigation by the European Parliament highlighted the NSA’s role in economic espionage in a report entitled ‘Development of Surveillance Technology and Risk of Abuse of Economic Information’.[40] That year, the NSA founded the NSA Hall of Honor, a memorial at the National Cryptologic Museum in Fort Meade, Maryland.[41] The memorial is a, “tribute to the pioneers and heroes who have made significant and long-lasting contributions to American cryptology”.[41] NSA employees must be retired for more than fifteen years to qualify for the memorial.[41]
NSA’s infrastructure deteriorated in the 1990s as defense budget cuts resulted in maintenance deferrals. On January 24, 2000, NSA headquarters suffered a total network outage for three days caused by an overloaded network. Incoming traffic was successfully stored on agency servers, but it could not be directed and processed. The agency carried out emergency repairs at a cost of $3 million to get the system running again. (Some incoming traffic was also directed instead to Britain’s GCHQ for the time being.) Director Michael Hayden called the outage a “wake-up call” for the need to invest in the agency’s infrastructure.[42]
War on Terror
In the aftermath of the September 11 attacks, the NSA created new IT systems to deal with the flood of information from new technologies like the Internet and cellphones. ThinThread contained advanced data mining capabilities. It also had a “privacy mechanism”; surveillance was stored encrypted; decryption required a warrant. The research done under this program may have contributed to the technology used in later systems. ThinThread was cancelled when Michael Hayden chose Trailblazer, which did not include ThinThread’s privacy system.[44]
Trailblazer Project ramped up in 2002 and was worked on by Science Applications International Corporation (SAIC), Boeing, Computer Sciences Corporation, IBM, and Litton Industries. Some NSA whistleblowers complained internally about major problems surrounding Trailblazer. This led to investigations by Congress and the NSA and DoD Inspectors General. The project was cancelled in early 2004.
Turbulence started in 2005. It was developed in small, inexpensive “test” pieces, rather than one grand plan like Trailblazer. It also included offensive cyber-warfare capabilities, like injecting malware into remote computers. Congress criticized Turbulence in 2007 for having similar bureaucratic problems as Trailblazer.[45] It was to be a realization of information processing at higher speeds in cyberspace.[46]
Global surveillance disclosures
The massive extent of the NSA’s spying, both foreign and domestic, was revealed to the public in a series of detailed disclosures of internal NSA documents beginning in June 2013. Most of the disclosures were leaked by former NSA contractor, Edward Snowden.
Scope of surveillance
It was revealed that the NSA intercepts telephone and Internet communications of over a billion people worldwide, seeking information on terrorism as well as foreign politics, economics[47] and “commercial secrets”.[48] In a declassified document it was revealed that 17,835 phone lines were on an improperly permitted “alert list” from 2006 to 2009 in breach of compliance, which tagged these phone lines for daily monitoring.[49][50][51] Eleven percent of these monitored phone lines met the agency’s legal standard for “reasonably articulable suspicion” (RAS).[49][52]
A dedicated unit of the NSA locates targets for the CIA for extrajudicial assassination in the Middle East.[53] The NSA has also spied extensively on the European Union, the United Nations and numerous governments including allies and trading partners in Europe, South America and Asia.[54][55]
The NSA tracks the locations of hundreds of millions of cellphones per day, allowing it to map people’s movements and relationships in detail.[56] It reportedly has access to all communications made via Google, Microsoft, Facebook, Yahoo, YouTube, AOL, Skype, Apple and Paltalk,[57] and collects hundreds of millions of contact lists from personal email and instant messaging accounts each year.[58] It has also managed to weaken much of the encryption used on the Internet (by collaborating with, coercing or otherwise infiltrating numerous technology companies), so that the majority of Internet privacy is now vulnerable to the NSA and other attackers.[59][60]
Domestically, the NSA collects and stores metadata records of phone calls,[61] including over 120 million US Verizon subscribers,[62] as well as Internet communications,[57] relying on a secret interpretation of the Patriot Act whereby the entirety of US communications may be considered “relevant” to a terrorism investigation if it is expected that even a tiny minority may relate to terrorism.[63] The NSA supplies foreign intercepts to the DEA, IRS and other law enforcement agencies, who use these to initiate criminal investigations. Federal agents are then instructed to “recreate” the investigative trail via parallel construction.[64]
The NSA also spies on influential Muslims to obtain information that could be used to discredit them, such as their use of pornography. The targets, both domestic and abroad, are not suspected of any crime but hold religious or political views deemed “radical” by the NSA.[65]
Although NSA’s surveillance activities are controversial, government agencies and private enterprises have common needs, and sometimes cooperate at subtle and complex technical levels. Big data is becoming more advantageous, justifying the cost of required computer hardware, and social media lead the trend. The interests of NSA and Silicon Valley began to converge as advances in computer storage technology drastically reduced the costs of storing enormous amounts of data and at the same time the value of the data for use in consumer marketing began to rise. On the other hand, social media sites are growing as voluntary data mining operations on a scale that rivals or exceeds anything the government could attempt on its own.[66]
According to a report in The Washington Post in July 2014, relying on information provided by Snowden, 90% of those placed under surveillance in the U.S. are ordinary Americans, and are not the intended targets. The newspaper said it had examined documents including emails, text messages, and online accounts that support the claim.[67]
Legal accountability
Despite President Obama’s claims that these programs have congressional oversight, members of Congress were unaware of the existence of these NSA programs or the secret interpretation of the Patriot Act, and have consistently been denied access to basic information about them.[68] Obama has also claimed that there are legal checks in place to prevent inappropriate access of data and that there have been no examples of abuse;[69] however, the secret FISC court charged with regulating the NSA’s activities is, according to its chief judge, incapable of investigating or verifying how often the NSA breaks even its own secret rules.[70] It has since been reported that the NSA violated its own rules on data access thousands of times a year, many of these violations involving large-scale data interceptions;[71] and that NSA officers have even used data intercepts to spy on love interests.[72] The NSA has “generally disregarded the special rules for disseminating United States person information” by illegally sharing its intercepts with other law enforcement agencies.[73] A March 2009 opinion of the FISC court, released by court order, states that protocols restricting data queries had been “so frequently and systemically violated that it can be fairly said that this critical element of the overall … regime has never functioned effectively.”[74][75] In 2011 the same court noted that the “volume and nature” of the NSA’s bulk foreign Internet intercepts was “fundamentally different from what the court had been led to believe”.[73] Email contact lists (including those of US citizens) are collected at numerous foreign locations to work around the illegality of doing so on US soil.[58]
Legal opinions on the NSA’s bulk collection program have differed. In mid-December 2013, U.S. District Court Judge Richard Leon ruled that the “almost-Orwellian” program likely violates the Constitution, and wrote, “I cannot imagine a more ‘indiscriminate’ and ‘arbitrary invasion’ than this systematic and high-tech collection and retention of personal data on virtually every single citizen for purposes of querying and analyzing it without prior judicial approval. Surely, such a program infringes on ‘that degree of privacy’ that the Founders enshrined in the Fourth Amendment. Indeed, I have little doubt that the author of our Constitution, James Madison, who cautioned us to beware ‘the abridgement of freedom of the people by gradual and silent encroachments by those in power,’ would be aghast.”[76]
Later that month, U.S. District Judge William Pauley ruled that the NSA’s collection of telephone records is legal and valuable in the fight against terrorism. In his opinion, he wrote, “a bulk telephony metadata collection program [is] a wide net that could find and isolate gossamer contacts among suspected terrorists in an ocean of seemingly disconnected data” and noted that a similar collection of data prior to 9/11 might have prevented the attack.[77]
An October 2014 United Nations report condemned mass surveillance by the United States and other countries as violating multiple international treaties and conventions that guarantee core privacy rights.[78]
Official responses
On March 20, 2013 the Director of National Intelligence, Lieutenant General James Clapper, testified before Congress that the NSA does not wittingly collect any kind of data on millions or hundreds of millions of Americans, but he retracted this in June after details of the PRISM program were published, and stated instead that meta-data of phone and Internet traffic are collected, but no actual message contents.[79] This was corroborated by the NSA Director, General Keith Alexander, before it was revealed that the XKeyscore program collects the contents of millions of emails from US citizens without warrant, as well as “nearly everything a user does on the Internet”. Alexander later admitted that “content” is collected, but stated that it is simply stored and never analyzed or searched unless there is “a nexus to al-Qaida or other terrorist groups”.[69]
Regarding the necessity of these NSA programs, Alexander stated on June 27 that the NSA’s bulk phone and Internet intercepts had been instrumental in preventing 54 terrorist “events”, including 13 in the US, and in all but one of these cases had provided the initial tip to “unravel the threat stream”.[80] On July 31 NSA Deputy Director John Inglis conceded to the Senate that these intercepts had not been vital in stopping any terrorist attacks, but were “close” to vital in identifying and convicting four San Diego men for sending US$8,930 to Al-Shabaab, a militia that conducts terrorism in Somalia.[81][82][83]
The U.S. government has aggressively sought to dismiss and challenge Fourth Amendment cases raised against it, and has granted retroactive immunity to ISPs and telecoms participating in domestic surveillance.[84][85] The U.S. military has acknowledged blocking access to parts of The Guardian website for thousands of defense personnel across the country,[86][87] and blocking the entire Guardian website for personnel stationed throughout Afghanistan, the Middle East, and South Asia.[88]
Organizational structure
The NSA is led by the Director of the National Security Agency (DIRNSA), who also serves as Chief of the Central Security Service (CHCSS) and Commander of the United States Cyber Command (USCYBERCOM) and is the highest-ranking military official of these organizations. He is assisted by a Deputy Director, who is the highest-ranking civilian within the NSA/CSS.
NSA also has an Inspector General, head of the Office of the Inspector General (OIG), a General Counsel, head of the Office of the General Counsel (OGC) and a Director of Compliance, who is head of the Office of the Director of Compliance (ODOC).[89]
Unlike other intelligence organizations such as CIA or DIA, NSA has always been particularly reticent concerning its internal organizational structure.
As of the mid-1990s, the National Security Agency was organized into five Directorates:
- The Operations Directorate, which was responsible for SIGINT collection and processing.
- The Technology and Systems Directorate, which develops new technologies for SIGINT collection and processing.
- The Information Systems Security Directorate, which was responsible for NSA’s communications and information security missions.
- The Plans, Policy and Programs Directorate, which provided staff support and general direction for the Agency.
- The Support Services Directorate, which provided logistical and administrative support activities.[90]
Each of these directorates consisted of several groups or elements, designated by a letter. There were for example the A Group, which was responsible for all SIGINT operations against the Soviet Union and Eastern Europe, and G Group, which was responsible for SIGINT related to all non-communist countries. These groups were divided in units designated by an additional number, like unit A5 for breaking Soviet codes, and G6, being the office for the Middle East, North Africa, Cuba, Central and South America.[91][92]
Structure
As of 2013, NSA has about a dozen directorates, which are designated by a letter, although not all of them are publicly known. The directorates are divided in divisions and units starting with the letter of the parent directorate, followed by a number for the division, the sub-unit or a sub-sub-unit.
The main elements of the organizational structure of the NSA are:[93]
- F – Directorate only known from unit F6, the Special Collection Service (SCS), which is a joint program created by CIA and NSA in 1978 to facilitate clandestine activities such as bugging computers throughout the world, using the expertise of both agencies.[94]
- G – Directorate only known from unit G112, the office that manages the Senior Span platform, attached to the U2 spy planes.[95]
- I – Information Assurance Directorate (IAD), which ensures availability, integrity, authentication, confidentiality, and non-repudiation of national security and telecommunications and information systems (national security systems).
- J – Directorate only known from unit J2, the Cryptologic Intelligence Unit
- L – Installation and Logistics
- M – Human Resources
- Q – Security and Counterintelligence
- R – Research Directorate, which conducts research on signals intelligence and on information assurance for the U.S. Government.[96]
- S – Signals Intelligence Directorate (SID), which is responsible for the collection, analysis, production and dissemination of signals intelligence. This directorate is led by a director and a deputy director. The SID consists of the following divisions:
- S1 – Customer Relations
- S2 – Analysis and Production Centers, with the following so-called Product Lines:
- S2A: South Asia, S2B: China and Korea, S2C: International Security, S2E: Middle East/Asia, S2F: International Crime, S2G: Counter-proliferation, S2H: Russia, S2I: Counter-terrorism, S2J: Weapons and Space, S2T: Current Threats
- S3 – Data Acquisition, with these divisions for the main collection programs:
- S31 – Cryptanalysis and Exploitation Services (CES)
- S32 – Tailored Access Operations (TAO), which hacks into foreign computers to conduct cyber-espionage and reportedly is “the largest and arguably the most important component of the NSA’s huge Signal Intelligence (SIGINT) Directorate, consisting of over 1,000 military and civilian computer hackers, intelligence analysts, targeting specialists, computer hardware and software designers, and electrical engineers.”[97]
- S33 – Global Access Operations (GAO), which is responsible for intercepts from satellites and other international SIGINT platforms.[98] A tool which details and maps the information collected by this unit is code-named Boundless Informant.
- S34 – Collections Strategies and Requirements Center
- S35 – Special Source Operations (SSO), which is responsible for domestic and compartmented collection programs, like for example the PRISM program.[98] Special Source Operations is also mentioned in connection to the FAIRVIEW collection program.[99]
- T – Technical Directorate (TD)
- Directorate for Education and Training
- Directorate for Corporate Leadership
- Foreign Affairs Directorate, which acts as liaison with foreign intelligence services, counter-intelligence centers and the UKUSA-partners.
- Acquisitions and Procurement Directorate
- Information Sharing Services (ISS), led by a chief and a deputy chief.[100]
In the year 2000, a leadership team was formed, consisting of the Director, the Deputy Director and the Directors of the Signals Intelligence (SID), the Information Assurance (IAD) and the Technical Directorate (TD). The chiefs of other main NSA divisions became associate directors of the senior leadership team.[101]
After president George W. Bush initiated the President’s Surveillance Program (PSP) in 2001, the NSA created a 24-hour Metadata Analysis Center (MAC), followed in 2004 by the Advanced Analysis Division (AAD), with the mission of analyzing content, Internet metadata and telephone metadata. Both units were part of the Signals Intelligence Directorate.[102]
A 2016 proposal would combine the Signals Intelligence Directorate with the Information Assurance Directorate into a Directorate of Operations.[103]
Watch centers
The NSA maintains at least two watch centers:
- National Security Operations Center (NSOC), which is the NSA’s current operations center and focal point for time-sensitive SIGINT reporting for the United States SIGINT System (USSS). This center was established in 1968 as the National SIGINT Watch Center (NSWC) and renamed into National SIGINT Operations Center (NSOC) in 1973. This “nerve center of the NSA” got its current name in 1996.[104]
- NSA/CSS Threat Operations Center (NTOC), which is the primary NSA/CSS partner for Department of Homeland Security response to cyber incidents. The NTOC establishes real-time network awareness and threat characterization capabilities to forecast, alert, and attribute malicious activity and enable the coordination of Computer Network Operations. The NTOC was established in 2004 as a joint Information Assurance and Signals Intelligence project.[105]
Employees
The number of NSA employees is officially classified[4] but there are several sources providing estimates. In 1961, NSA had 59,000 military and civilian employees, which grew to 93,067 in 1969, of which 19,300 worked at the headquarters at Fort Meade. In the early 1980s NSA had roughly 50,000 military and civilian personnel. By 1989 this number had grown again to 75,000, of which 25,000 worked at the NSA headquarters. Between 1990 and 1995 the NSA’s budget and workforce were cut by one third, which led to a substantial loss of experience.[106]
In 2012, the NSA said more than 30,000 employees worked at Fort Meade and other facilities.[2] In 2012, John C. Inglis, the deputy director, said that the total number of NSA employees is “somewhere between 37,000 and one billion” as a joke,[4] and stated that the agency is “probably the biggest employer of introverts.”[4] In 2013 Der Spiegel stated that the NSA had 40,000 employees.[5] More widely, it has been described as the world’s largest single employer of mathematicians.[107] Some NSA employees form part of the workforce of the National Reconnaissance Office (NRO), the agency that provides the NSA with satellite signals intelligence.
As of 2013 about 1,000 system administrators work for the NSA.[108]
Security issues
The NSA received criticism early on in 1960 after two agents had defected to the Soviet Union. Investigations by the House Un-American Activities Committee and a special subcommittee of the United States House Committee on Armed Services revealed severe cases of ignorance in personnel security regulations, prompting the former personnel director and the director of security to step down and leading to the adoption of stricter security practices.[109] Nonetheless, security breaches reoccurred only a year later when in an issue of Izvestia of July 23, 1963, a former NSA employee published several cryptologic secrets.
The very same day, an NSA clerk-messenger committed suicide as ongoing investigations disclosed that he had sold secret information to the Soviets on a regular basis. The reluctance of Congressional houses to look into these affairs had prompted a journalist to write, “If a similar series of tragic blunders occurred in any ordinary agency of Government an aroused public would insist that those responsible be officially censured, demoted, or fired.” David Kahn criticized the NSA’s tactics of concealing its doings as smug and the Congress’ blind faith in the agency’s right-doing as shortsighted, and pointed out the necessity of surveillance by the Congress to prevent abuse of power.[109]
Edward Snowden‘s leaking of the existence of PRISM in 2013 caused the NSA to institute a “two-man rule“, where two system administrators are required to be present when one accesses certain sensitive information.[108]Snowden claims he suggested such a rule in 2009.[110]
Polygraphing
The NSA conducts polygraph tests of employees. For new employees, the tests are meant to discover enemy spies who are applying to the NSA and to uncover any information that could make an applicant pliant to coercion.[111] As part of the latter, historically EPQs or “embarrassing personal questions” about sexual behavior had been included in the NSA polygraph.[111]The NSA also conducts five-year periodic reinvestigation polygraphs of employees, focusing on counterintelligence programs. In addition the NSA conducts periodic polygraph investigations in order to find spies and leakers; those who refuse to take them may receive “termination of employment”, according to a 1982 memorandum from the director of the NSA.[112]
NSA-produced video on the polygraph process
There are also “special access examination” polygraphs for employees who wish to work in highly sensitive areas, and those polygraphs cover counterintelligence questions and some questions about behavior.[112] NSA’s brochure states that the average test length is between two and four hours.[113] A 1983 report of the Office of Technology Assessment stated that “It appears that the NSA [National Security Agency] (and possibly CIA) use the polygraph not to determine deception or truthfulness per se, but as a technique of interrogation to encourage admissions.”[114] Sometimes applicants in the polygraph process confess to committing felonies such as murder, rape, and selling of illegal drugs. Between 1974 and 1979, of the 20,511 job applicants who took polygraph tests, 695 (3.4%) confessed to previous felony crimes; almost all of those crimes had been undetected.[111]
In 2010 the NSA produced a video explaining its polygraph process.[115] The video, ten minutes long, is titled “The Truth About the Polygraph” and was posted to the Web site of the Defense Security Service. Jeff Stein of The Washington Post said that the video portrays “various applicants, or actors playing them — it’s not clear — describing everything bad they had heard about the test, the implication being that none of it is true.”[116] AntiPolygraph.org argues that the NSA-produced video omits some information about the polygraph process; it produced a video responding to the NSA video.[115] George Maschke, the founder of the Web site, accused the NSA polygraph video of being “Orwellian“.[116]
After Edward Snowden revealed his identity in 2013, the NSA began requiring polygraphing of employees once per quarter.[117]
Arbitrary firing
The number of exemptions from legal requirements has been criticized. When in 1964 the Congress was hearing a bill giving the director of the NSA the power to fire at will any employee,The Washington Post wrote: “This is the very definition of arbitrariness. It means that an employee could be discharged and disgraced on the basis of anonymous allegations without the slightest opportunity to defend himself.” Yet, the bill was accepted by an overwhelming majority.[109]
Insignia and memorials
The heraldic insignia of NSA consists of an eagle inside a circle, grasping a key in its talons.[118] The eagle represents the agency’s national mission.[118] Its breast features a shield with bands of red and white, taken from the Great Seal of the United States and representing Congress.[118] The key is taken from the emblem of Saint Peter and represents security.[118]
When the NSA was created, the agency had no emblem and used that of the Department of Defense.[119] The agency adopted its first of two emblems in 1963.[119] The current NSA insignia has been in use since 1965, when then-Director, LTG Marshall S. Carter (USA) ordered the creation of a device to represent the agency.[120]
The NSA’s flag consists of the agency’s seal on a light blue background.

National Cryptologic Memorial
Crews associated with NSA missions have been involved in a number of dangerous and deadly situations.[121] The USS Liberty incident in 1967 and USS Pueblo incident in 1968 are examples of the losses endured during the Cold War.[121]
The National Security Agency/Central Security Service Cryptologic Memorial honors and remembers the fallen personnel, both military and civilian, of these intelligence missions.[122] It is made of black granite, and has 171 names carved into it, as of 2013 .[122] It is located at NSA headquarters. A tradition of declassifying the stories of the fallen was begun in 2001.[122]
NSANet (NSA’s intranet)

Behind the Green Door – Secure communications room with separate computer terminals for access to SIPRNET, GWAN, NSANET, and JWICS
NSANet stands for National Security Agency Network and is the official NSA intranet.[123] It is a classified network,[124] for information up to the level of TS/SCI[125] to support the use and sharing of intelligence data between NSA and the signals intelligence agencies of the four other nations of the Five Eyes partnership. The management of NSANet has been delegated to the Central Security Service Texas (CSSTEXAS).[126]
NSANet is a highly secured computer network consisting of fiber-optic and satellite communication channels which are almost completely separated from the public Internet. The network allows NSA personnel and civilian and military intelligence analysts anywhere in the world to have access to the agency’s systems and databases. This access is tightly controlled and monitored. For example, every keystroke is logged, activities are audited at random and downloading and printing of documents from NSANet are recorded.[127]
In 1998, NSANet, along with NIPRNET and SIPRNET, had “significant problems with poor search capabilities, unorganized data and old information”.[128] In 2004, the network was reported to have used over twenty commercial off-the-shelf operating systems.[129] Some universities that do highly sensitive research are allowed to connect to it.[130]
The thousands of Top Secret internal NSA documents that were taken by Edward Snowden in 2013 were stored in “a file-sharing location on the NSA’s intranet site” so they could easily be read online by NSA personnel. Everyone with a TS/SCI-clearance had access to these documents and as a system administrator, Snowden was responsible for moving accidentally misplaced highly sensitive documents to more secure storage locations.[131]
National Computer Security Center
The DoD Computer Security Center was founded in 1981 and renamed the National Computer Security Center (NCSC) in 1985. NCSC was responsible for computer security throughout the federal government.[132] NCSC was part of NSA,[133] and during the late 1980s and the 1990s, NSA and NCSC published Trusted Computer System Evaluation Criteria in a six-foot high Rainbow Series of books that detailed trusted computing and network platform specifications.[134] The Rainbow books were replaced by the Common Criteria, however, in the early 2000s.[134]
Facilities
Headquarters

National Security Agency headquarters in Fort Meade, 2013
Headquarters for the National Security Agency is located at 39°6′32″N 76°46′17″W in Fort George G. Meade, Maryland, although it is separate from other compounds and agencies that are based within this same military installation. Ft. Meade is about 20 mi (32 km) southwest of Baltimore,[135] and 25 mi (40 km) northeast of Washington, DC.[136] The NSA has its own exit off Maryland Route 295 South labeled “NSA Employees Only”.[137][138] The exit may only be used by people with the proper clearances, and security vehicles parked along the road guard the entrance.[139]
NSA is the largest employer in the U.S. state of Maryland, and two-thirds of its personnel work at Ft. Meade.[140] Built on 350 acres (140 ha; 0.55 sq mi)[141] of Ft. Meade’s 5,000 acres (2,000 ha; 7.8 sq mi),[142] the site has 1,300 buildings and an estimated 18,000 parking spaces.[136][143]
The main NSA headquarters and operations building is what James Bamford, author of Body of Secrets, describes as “a modern boxy structure” that appears similar to “any stylish office building.”[144] The building is covered with one-way dark glass, which is lined with copper shielding in order to prevent espionage by trapping in signals and sounds.[144] It contains 3,000,000 square feet (280,000 m2), or more than 68 acres (28 ha), of floor space; Bamford said that the U.S. Capitol “could easily fit inside it four times over.”[144]
The facility has over 100 watchposts,[145] one of them being the visitor control center, a two-story area that serves as the entrance.[144] At the entrance, a white pentagonal structure,[146] visitor badges are issued to visitors and security clearances of employees are checked.[147] The visitor center includes a painting of the NSA seal.[146]
The OPS2A building, the tallest building in the NSA complex and the location of much of the agency’s operations directorate, is accessible from the visitor center. Bamford described it as a “dark glass Rubik’s Cube“.[148] The facility’s “red corridor” houses non-security operations such as concessions and the drug store. The name refers to the “red badge” which is worn by someone without a security clearance. The NSA headquarters includes a cafeteria, a credit union, ticket counters for airlines and entertainment, a barbershop, and a bank.[146] NSA headquarters has its own post office, fire department, and police force.[149][150][151]
The employees at the NSA headquarters reside in various places in the Baltimore-Washington area, including Annapolis, Baltimore, and Columbia in Maryland and the District of Columbia, including the Georgetown community.[152]
Power consumption

Due to massive amounts of data processing, NSA is the largest electricity consumer in Maryland.[140]
Following a major power outage in 2000, in 2003 and in follow-ups through 2007, The Baltimore Sun reported that the NSA was at risk of electrical overload because of insufficient internal electrical infrastructure at Fort Meade to support the amount of equipment being installed. This problem was apparently recognized in the 1990s but not made a priority, and “now the agency’s ability to keep its operations going is threatened.”[153]
Baltimore Gas & Electric (BGE, now Constellation Energy) provided NSA with 65 to 75 megawatts at Ft. Meade in 2007, and expected that an increase of 10 to 15 megawatts would be needed later that year.[154] In 2011, NSA at Ft. Meade was Maryland’s largest consumer of power.[140] In 2007, as BGE’s largest customer, NSA bought as much electricity as Annapolis, the capital city of Maryland.[153]
One estimate put the potential for power consumption by the new Utah Data Center at US$40 million per year.[155]
History of headquarters
When the agency was established, its headquarters and cryptographic center were in the Naval Security Station in Washington, D.C. The COMINT functions were located in Arlington Hall in Northern Virginia, which served as the headquarters of the U.S. Army‘s cryptographic operations.[156] Because the Soviet Union had detonated a nuclear bomb and because the facilities were crowded, the federal government wanted to move several agencies, including the AFSA/NSA. A planning committee considered Fort Knox, but Fort Meade, Maryland, was ultimately chosen as NSA headquarters because it was far enough away from Washington, D.C. in case of a nuclear strike and was close enough so its employees would not have to move their families.[157]
Construction of additional buildings began after the agency occupied buildings at Ft. Meade in the late 1950s, which they soon outgrew.[157] In 1963 the new headquarters building, nine stories tall, opened. NSA workers referred to the building as the “Headquarters Building” and since the NSA management occupied the top floor, workers used “Ninth Floor” to refer to their leaders.[158] COMSEC remained in Washington, D.C., until its new building was completed in 1968.[157] In September 1986, the Operations 2A and 2B buildings, both copper-shielded to prevent eavesdropping, opened with a dedication by President Ronald Reagan.[159] The four NSA buildings became known as the “Big Four.”[159] The NSA director moved to 2B when it opened.[159]
Fort Meade shooting
On March 30, 2015, shortly before 9 am, a stolen sports utility vehicle approached an NSA police vehicle blocking the road near the gate of Fort Meade, after it was told to leave the area. NSA officers fired on the SUV, killing the 27-year-old driver, Mya Hall, and seriously injuring her 20-year-old passenger. An NSA officer’s arm was injured when Hall subsequently crashed into his vehicle.[160][161]
The two women were transgender[162] and had just gotten off from a night of partying at a motel with the man they’d stolen the SUV from that morning. They “attempted to drive a vehicle into the National Security Agency portion of the installation without authorization”, according to an NSA statement.[163] FBI spokeswoman Amy Thoreson said the incident is not believed to be related to terrorism.[164] In June 2015 the FBI closed its investigation into the incident and federal prosecutors have declined to bring charges against anyone involved.[165]
An anonymous police official told The Washington Post, “This was not a deliberate attempt to breach the security of NSA. This was not a planned attack.” The two are believed to have made a wrong turn off the highway, while fleeing from the motel after stealing the vehicle. A small amount of cocaine was found in the SUV. A local CBS reporter initially said a gun was found,[166] but her later revision does not.[167] Dozens of journalists were corralled into a parking lot blocks away from the scene, and were barred from photographing the area.[168]
Computing
In 1995, The Baltimore Sun reported that the NSA is the owner of the single largest group of supercomputers.[169]
NSA held a groundbreaking ceremony at Ft. Meade in May 2013 for its High Performance Computing Center 2, expected to open in 2016.[170] Called Site M, the center has a 150 megawatt power substation, 14 administrative buildings and 10 parking garages.[149] It cost $3.2 billion and covers 227 acres (92 ha; 0.355 sq mi).[149] The center is 1,800,000 square feet (17 ha; 0.065 sq mi)[149] and initially uses 60 megawatts of electricity.[171]
Increments II and III are expected to be completed by 2030, and would quadruple the space, covering 5,800,000 square feet (54 ha; 0.21 sq mi) with 60 buildings and 40 parking garages.[149] Defense contractors are also establishing or expanding cybersecurity facilities near the NSA and around the Washington metropolitan area.[149]
Other U.S. facilities

Buckley Air Force Base in Colorado
As of 2012, NSA collected intelligence from four geostationary satellites.[155] Satellite receivers were at Roaring Creek Station in Catawissa, Pennsylvania and Salt Creek Station in Arbuckle, California.[155] It operated ten to twenty taps on U.S. telecom switches. NSA had installations in several U.S. states and from them observed intercepts from Europe, the Middle East, North Africa, Latin America, and Asia.[155]
NSA had facilities at Friendship Annex (FANX) in Linthicum, Maryland, which is a 20 to 25-minute drive from Ft. Meade;[172] the Aerospace Data Facility at Buckley Air Force Base in Aurora outside Denver, Colorado; NSA Texas in the Texas Cryptology Center at Lackland Air Force Base in San Antonio, Texas; NSA Georgia at Fort Gordon in Augusta, Georgia; NSA Hawaii in Honolulu; the Multiprogram Research Facility in Oak Ridge, Tennessee, and elsewhere.[152][155]
On January 6, 2011 a groundbreaking ceremony was held to begin construction on NSA’s first Comprehensive National Cyber-security Initiative (CNCI) Data Center, known as the “Utah Data Center” for short. The $1.5B data center is being built at Camp Williams, Utah, located 25 miles (40 km) south of Salt Lake City, and will help support the agency’s National Cyber-security Initiative.[173] It is expected to be operational by September 2013.[155]
In 2009, to protect its assets and to access more electricity, NSA sought to decentralize and expand its existing facilities in Ft. Meade and Menwith Hill,[174] the latter expansion expected to be completed by 2015.[175]
The Yakima Herald-Republic cited Bamford, saying that many of NSA’s bases for its Echelon program were a legacy system, using outdated, 1990s technology.[176] In 2004, NSA closed its operations at Bad Aibling Station (Field Station 81) in Bad Aibling, Germany.[177] In 2012, NSA began to move some of its operations at Yakima Research Station, Yakima Training Center, in Washington state to Colorado, planning to leave Yakima closed.[178] As of 2013, NSA also intended to close operations at Sugar Grove, West Virginia.[176]
International stations
Following the signing in 1946–1956[179] of the UKUSA Agreement between the United States, United Kingdom, Canada, Australia and New Zealand, who then cooperated on signals intelligence and ECHELON,[180] NSA stations were built at GCHQ Bude in Morwenstow, United Kingdom; Geraldton, Pine Gap and Shoal Bay, Australia; Leitrim and Ottawa, Canada; Misawa, Japan; and Waihopai and Tangimoana,[181] New Zealand.[182]
NSA operates RAF Menwith Hill in North Yorkshire, United Kingdom, which was, according to BBC News in 2007, the largest electronic monitoring station in the world.[183] Planned in 1954, and opened in 1960, the base covered 562 acres (227 ha; 0.878 sq mi) in 1999.[184]
The agency’s European Cryptologic Center (ECC), with 240 employees in 2011, is headquartered at a US military compound in Griesheim, near Frankfurt in Germany. A 2011 NSA report indicates that the ECC is responsible for the “largest analysis and productivity in Europe” and focusses on various priorities, including Africa, Europe, the Middle East and counterterrorism operations.[185]
In 2013, a new Consolidated Intelligence Center, also to be used by NSA, is being built at the headquarters of the United States Army Europe in Wiesbaden, Germany.[186] NSA’s partnership with Bundesnachrichtendienst (BND), the German foreign intelligence service, was confirmed by BND president Gerhard Schindler.[186]
Thailand
Thailand is a “3rd party partner” of the NSA along with nine other nations.[187] These are non-English-speaking countries that have made security agreements for the exchange of SIGINT raw material and end product reports.
Thailand is the site of at least two US SIGINT collection stations. One is at the US Embassy in Bangkok, a joint NSA-CIA Special Collection Service (SCS) unit. It presumably eavesdrops on foreign embassies, governmental communications, and other targets of opportunity.[188]
The second installation is a FORNSAT (foreign satellite interception) station in the Thai city of Khon Kaen. It is codenamed INDRA, but has also been referred to as LEMONWOOD.[188] The station is approximately 40 ha (100 acres) in size and consists of a large 3,700–4,600 m2 (40,000–50,000 ft2) operations building on the west side of the ops compound and four radome-enclosed parabolic antennas. Possibly two of the radome-enclosed antennas are used for SATCOM intercept and two antennas used for relaying the intercepted material back to NSA. There is also a PUSHER-type circularly-disposed antenna array (CDAA) array just north of the ops compound.[189][190]
NSA activated Khon Kaen in October 1979. Its mission was to eavesdrop on the radio traffic of Chinese army and air force units in southern China, especially in and around the city of Kunming in Yunnan Province. Back in the late 1970s the base consisted only of a small CDAA antenna array that was remote-controlled via satellite from the NSA listening post at Kunia, Hawaii, and a small force of civilian contractors from Bendix Field Engineering Corp. whose job it was to keep the antenna array and satellite relay facilities up and running 24/7.[189]
According to the papers of the late General William Odom, the INDRA facility was upgraded in 1986 with a new British-made PUSHER CDAA antenna as part of an overall upgrade of NSA and Thai SIGINT facilities whose objective was to spy on the neighboring communist nations of Vietnam, Laos, and Cambodia.[189]
The base apparently fell into disrepair in the 1990s as China and Vietnam became more friendly towards the US, and by 2002 archived satellite imagery showed that the PUSHER CDAA antenna had been torn down, perhaps indicating that the base had been closed. At some point in the period since 9/11, the Khon Kaen base was reactivated and expanded to include a sizeable SATCOM intercept mission. It is likely that the NSA presence at Khon Kaen is relatively small, and that most of the work is done by civilian contractors.[189]
Mission
NSA’s eavesdropping mission includes radio broadcasting, both from various organizations and individuals, the Internet, telephone calls, and other intercepted forms of communication. Its secure communications mission includes military, diplomatic, and all other sensitive, confidential or secret government communications.[191]
According to the Washington Post, “[e]very day, collection systems at the National Security Agency intercept and store 1.7 billion e-mails, phone calls and other types of communications. The NSA sorts a fraction of those into 70 separate databases.”[192]
Because of its listening task, NSA/CSS has been heavily involved in cryptanalytic research, continuing the work of predecessor agencies which had broken many World War II codes and ciphers (see, for instance, Purple, Venona project, and JN-25).
In 2004, NSA Central Security Service and the National Cyber Security Division of the Department of Homeland Security (DHS) agreed to expand NSA Centers of Academic Excellence in Information Assurance Education Program.[193]
As part of the National Security Presidential Directive 54/Homeland Security Presidential Directive 23 (NSPD 54), signed on January 8, 2008 by President Bush, the NSA became the lead agency to monitor and protect all of the federal government’s computer networks from cyber-terrorism.[9]
Operations
Operations by the National Security Agency can be divided in three types:
- Collection overseas, which falls under the responsibility of the Global Access Operations (GAO) division.
- Domestic collection, which falls under the responsibility of the Special Source Operations (SSO) division.
- Hacking operations, which falls under the responsibility of the Tailored Access Operations (TAO) division.
Collection overseas
Echelon
Echelon was created in the incubator of the Cold War.[194] Today it is a legacy system, and several NSA stations are closing.[176]
NSA/CSS, in combination with the equivalent agencies in the United Kingdom (Government Communications Headquarters), Canada (Communications Security Establishment), Australia (Defence Signals Directorate), and New Zealand (Government Communications Security Bureau), otherwise known as the UKUSA group,[195] was reported to be in command of the operation of the so-called ECHELON system. Its capabilities were suspected to include the ability to monitor a large proportion of the world’s transmitted civilian telephone, fax and data traffic.[196]
During the early 1970s, the first of what became more than eight large satellite communications dishes were installed at Menwith Hill.[197] Investigative journalist Duncan Campbell reported in 1988 on the ECHELON surveillance program, an extension of the UKUSA Agreement on global signals intelligence SIGINT, and detailed how the eavesdropping operations worked.[198] In November 3, 1999 the BBC reported that they had confirmation from the Australian Government of the existence of a powerful “global spying network” code-named Echelon, that could “eavesdrop on every single phone call, fax or e-mail, anywhere on the planet” with Britain and the United States as the chief protagonists. They confirmed that Menwith Hill was “linked directly to the headquarters of the US National Security Agency (NSA) at Fort Meade in Maryland”.[199]
NSA’s United States Signals Intelligence Directive 18 (USSID 18) strictly prohibited the interception or collection of information about “… U.S. persons, entities, corporations or organizations….” without explicit written legal permission from the United States Attorney General when the subject is located abroad, or the Foreign Intelligence Surveillance Court when within U.S. borders. Alleged Echelon-related activities, including its use for motives other than national security, including political and industrial espionage, received criticism from countries outside the UKUSA alliance.[200][201]
Other SIGINT operations overseas
The NSA is also involved in planning to blackmail people with “SEXINT“, intelligence gained about a potential target’s sexual activity and preferences. Those targeted had not committed any apparent crime nor were charged with one.[202]
In order to support its facial recognition program, the NSA is intercepting “millions of images per day”.[203]
The Real Time Regional Gateway is a data collection program introduced in 2005 in Iraq by NSA during the Iraq War that consisted of gathering all electronic communication, storing it, then searching and otherwise analyzing it. It was effective in providing information about Iraqi insurgents who had eluded less comprehensive techniques.[204] This “collect it all” strategy introduced by NSA director, Keith B. Alexander, is believed by Glenn Greenwald of The Guardian to be the model for the comprehensive worldwide mass archiving of communications which NSA is engaged in as of 2013.[205]
BoundlessInformant
Edward Snowden revealed in June 2013 that between February 8 and March 8, 2013, the NSA collected about 124.8 billion telephone data items and 97.1 billion computer data items throughout the world, as was displayed in charts from an internal NSA tool codenamed Boundless Informant. It was reported that some of these data reflected eavesdropping on citizens in countries like Germany, Spain and France.[206]
BoundlessInformant employs big data databases, cloud computing technology, and Free and Open Source Software (FOSS) to analyze data collected worldwide by the NSA.[207]
Bypassing encryption
In 2013, reporters uncovered a secret memo that claims the NSA created and pushed for the adoption of the Dual_EC_DRBG encryption standard that contained built-in vulnerabilities in 2006 to the United States National Institute of Standards and Technology (NIST), and the International Organization for Standardization (aka ISO).[208][209] This memo appears to give credence to previous speculation by cryptographers at Microsoft Research.[210]Edward Snowden claims that the NSA often bypasses encryption altogether by lifting information before it is encrypted or after it is decrypted.[209]
XKeyscore rules (as specified in a file xkeyscorerules100.txt, sourced by German TV stations NDR and WDR, who claim to have excerpts from its source code) reveal that the NSA tracks users of privacy-enhancing software tools, including Tor; an anonymous email service provided by the MIT Computer Science and Artificial Intelligence Laboratory (CSAIL) in Cambridge, Massachusetts; and readers of the Linux Journal.[211][212]
Domestic activity
NSA’s mission, as set forth in Executive Order 12333 in 1981, is to collect information that constitutes “foreign intelligence or counterintelligence” while not “acquiring information concerning the domestic activities of United States persons“. NSA has declared that it relies on the FBI to collect information on foreign intelligence activities within the borders of the United States, while confining its own activities within the United States to the embassies and missions of foreign nations.[213] The appearance of a ‘Domestic Surveillance Directorate’ of the NSA was soon exposed as a hoax in 2013.[214][215]
NSA’s domestic surveillance activities are limited by the requirements imposed by the Fourth Amendment to the U.S. Constitution. The Foreign Intelligence Surveillance Court for example held in October 2011, citing multiple Supreme Court precedents, that the Fourth Amendment prohibitions against unreasonable searches and seizures applies to the contents of all communications, whatever the means, because “a person’s private communications are akin to personal papers.”[216] However, these protections do not apply to non-U.S. persons located outside of U.S. borders, so the NSA’s foreign surveillance efforts are subject to far fewer limitations under U.S. law.[217] The specific requirements for domestic surveillance operations are contained in the Foreign Intelligence Surveillance Act of 1978 (FISA), which does not extend protection to non-U.S. citizens located outside of U.S. territory.[217]
George W. Bush administration
George W. Bush, president during the 9/11 terrorist attacks, approved the Patriot Act shortly after the attacks to take anti-terrorist security measures. Title 1, 2, and 9 specifically authorized measures that would be taken by the NSA. These titles granted enhanced domestic security against terrorism, surveillance procedures, and improved intelligence, respectively. On March 10, 2004, there was a debate between President Bush and White House Counsel Alberto Gonzales, Attorney General John Ashcroft, and Acting Attorney General James Comey. The Attorney Generals were unsure if the NSA’s programs could be considered constitutional. They threatened to resign over the matter, but ultimately the NSA’s programs continued.[218] On March 11, 2004, President Bush signed a new authorization for mass surveillance of Internet records, in addition to the surveillance of phone records.This allowed the president to be able to override laws such as the Foreign Intelligence Surveillance Act, which protected civilians from mass surveillance. In addition to this, President Bush also signed that the measures of mass surveillance were also retroactively in place.[219]
Warrantless wiretaps
On December 16, 2005, The New York Times reported that, under White House pressure and with an executive order from President George W. Bush, the National Security Agency, in an attempt to thwart terrorism, had been tapping phone calls made to persons outside the country, without obtaining warrants from the United States Foreign Intelligence Surveillance Court, a secret court created for that purpose under the Foreign Intelligence Surveillance Act (FISA).[220]
One such surveillance program, authorized by the U.S. Signals Intelligence Directive 18 of President George Bush, was the Highlander Project undertaken for the National Security Agency by the U.S. Army 513th Military Intelligence Brigade. NSA relayed telephone (including cell phone) conversations obtained from ground, airborne, and satellite monitoring stations to various U.S. Army Signal Intelligence Officers, including the 201st Military Intelligence Battalion. Conversations of citizens of the U.S. were intercepted, along with those of other nations.[221]
Proponents of the surveillance program claim that the President has executive authority to order such action, arguing that laws such as FISA are overridden by the President’s Constitutional powers. In addition, some argued that FISA was implicitly overridden by a subsequent statute, the Authorization for Use of Military Force, although the Supreme Court’s ruling in Hamdan v. Rumsfeld deprecates this view. In the August 2006 case ACLU v. NSA, U.S. District Court Judge Anna Diggs Taylor concluded that NSA’s warrantless surveillance program was both illegal and unconstitutional. On July 6, 2007 the 6th Circuit Court of Appeals vacated the decision on the grounds that the ACLU lacked standing to bring the suit.[222]
On January 17, 2006, the Center for Constitutional Rights filed a lawsuit, CCR v. Bush, against the George W. Bush Presidency. The lawsuit challenged the National Security Agency’s (NSA’s) surveillance of people within the U.S., including the interception of CCR emails without securing a warrant first.[223][224]
In September 2008, the Electronic Frontier Foundation (EFF) filed a class action lawsuit against the NSA and several high-ranking officials of the Bush administration,[225] charging an “illegal and unconstitutional program of dragnet communications surveillance,”[226] based on documentation provided by former AT&T technician Mark Klein.[227]
As a result of the USA Freedom Act passed by Congress in June 2015, the NSA had to shut down its bulk phone surveillance program on November 29 of the same year. The USA Freedom Act forbids the NSA to collect metadata and content of phone calls unless it has a warrant for terrorism investigation. In that case the agency has to ask the telecom companies for the record, which will only be kept for six months.
AT&T Internet monitoring
In May 2006, Mark Klein, a former AT&T employee, alleged that his company had cooperated with NSA in installing Narus hardware to replace the FBI Carnivore program, to monitor network communications including traffic between American citizens.[228]
Data mining
NSA was reported in 2008 to use its computing capability to analyze “transactional” data that it regularly acquires from other government agencies, which gather it under their own jurisdictional authorities. As part of this effort, NSA now monitors huge volumes of records of domestic email data, web addresses from Internet searches, bank transfers, credit-card transactions, travel records, and telephone data, according to current and former intelligence officials interviewed by The Wall Street Journal. The sender, recipient, and subject line of emails can be included, but the content of the messages or of phone calls are not.[229]
A 2013 advisory group for the Obama administration, seeking to reform NSA spying programs following the revelations of documents released by Edward J. Snowden.[230] mentioned in ‘Recommendation 30’ on page 37, “…that the National Security Council staff should manage an interagency process to review on a regular basis the activities of the US Government regarding attacks that exploit a previously unknown vulnerability in a computer application.” Retired cyber security expert Richard A. Clarke was a group member and stated on April 11 that NSA had no advance knowledge of Heartbleed.[231]
Illegally obtained evidence
In August 2013 it was revealed that a 2005 IRS training document showed that NSA intelligence intercepts and wiretaps, both foreign and domestic, were being supplied to the Drug Enforcement Administration (DEA) and Internal Revenue Service (IRS) and were illegally used to launch criminal investigations of US citizens. Law enforcement agents were directed to conceal how the investigations began and recreate an apparently legal investigative trail by re-obtaining the same evidence by other means.[232][233]
Barack Obama administration
In the months leading to April 2009, the NSA intercepted the communications of American citizens, including a Congressman, although the Justice Department believed that the interception was unintentional. The Justice Department then took action to correct the issues and bring the program into compliance with existing laws.[234] United States Attorney General Eric Holder resumed the program according to his understanding of the Foreign Intelligence Surveillance Act amendment of 2008, without explaining what had occurred.[235]
Polls conducted in June 2013 found divided results among Americans regarding NSA’s secret data collection.[236] Rasmussen Reports found that 59% of Americans disapprove,[237] Gallup found that 53% disapprove,[238] and Pew found that 56% are in favor of NSA data collection.[239]
Section 215 metadata collection
On April 25, 2013, the NSA obtained a court order requiring Verizon‘s Business Network Services to provide metadata on all calls in its system to the NSA “on an ongoing daily basis” for a three-month period, as reported by The Guardian on June 6, 2013. This information includes “the numbers of both parties on a call … location data, call duration, unique identifiers, and the time and duration of all calls” but not “[t]he contents of the conversation itself”. The order relies on the so-called “business records” provision of the Patriot Act.[240][241]
In August 2013, following the Snowden leaks, new details about the NSA’s data mining activity were revealed. Reportedly, the majority of emails into or out of the United States are captured at “selected communications links” and automatically analyzed for keywords or other “selectors”. Emails that do not match are deleted.[242]
The utility of such a massive metadata collection in preventing terrorist attacks is disputed. Many studies reveal the dragnet like system to be ineffective. One such report, released by the New America Foundation concluded that after an analysis of 225 terrorism cases, the NSA “had no discernible impact on preventing acts of terrorism.”[243]
Defenders of the program say that while metadata alone can’t provide all the information necessary to prevent an attack, it assures the ability to “connect the dots”[244] between suspect foreign numbers and domestic numbers with a speed only the NSA’s software is capable of. One benefit of this is quickly being able to determine the difference between suspicious activity and real threats.[citation needed] As an example, NSA director General Keith Alexander mentioned at the annual Cybersecurity Summit in 2013, that metadata analysis of domestic phone call records after the Boston Marathon bombing helped determine that[clarification needed] another attack in New York was baseless.[244]
In addition to doubts about its effectiveness, many people argue that the collection of metadata is an unconstitutional invasion of privacy. As of 2015, the collection process remains legal and grounded in the ruling from Smith v. Maryland (1979). A prominent opponent of the data collection and its legality is U.S. District Judge Richard J. Leon, who issued a report in 2013[245] in which he stated: “I cannot imagine a more ‘indiscriminate’ and ‘arbitrary invasion’ than this systematic and high tech collection and retention of personal data on virtually every single citizen for purposes of querying and analyzing it without prior judicial approval…Surely, such a program infringes on ‘that degree of privacy’ that the founders enshrined in the Fourth Amendment”.
The PRISM program[edit]
Under the PRISM program, which started in 2007,[246][247] NSA gathers Internet communications from foreign targets from nine major U.S. Internet-based communication service providers: Microsoft,[248] Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube and Apple. Data gathered include email, video and voice chat, videos, photos, VoIP chats such as Skype, and file transfers.
June 2015 – WikiLeaks: Industrial espionage
In June 2015, Wikileaks published documents, which showed that NSA spied on French companies.[249]
July 2015 – WikiLeaks: Espionage against German federal ministries
In July 2015, WikiLeaks published documents, which showed that NSA spied on federal German ministries since 1990s.[250][251] Even Germany’s Chancellor Angela Merkel‘s cellphones and phone of her predecessors had been intercepted.[252]
Claims of prevented terrorist attacks
Former NSA director General Keith Alexander claimed that in September 2009 the NSA prevented Najibullah Zazi and his friends from carrying out a terrorist attack.[253] However, this claim has been debunked and no evidence has been presented demonstrating that the NSA has ever been instrumental in preventing a terrorist attack.[254][255][256][257]
Hacking operations
Besides the more traditional ways of eavesdropping in order to collect signals intelligence, NSA is also engaged in hacking computers, smartphones and their networks. These operations are conducted by the Tailored Access Operations (TAO) division.
NSA’s China hacking group
According to the Foreign Policy magazine, “… the Office of Tailored Access Operations, or TAO, has successfully penetrated Chinese computer and telecommunications systems for almost 15 years, generating some of the best and most reliable intelligence information about what is going on inside the People’s Republic of China.”[258][259]
Syrian internet blackout
In an interview with Wired magazine, Edward Snowden said the Tailored Access Operations division accidentally caused Syria‘s internet blackout in 2012.[260]
Suspected responsibility for hacking operations by the Equation Group
The espionage group named the Equation Group, described by discoverers Kaspersky Labs as one of the most advanced (if not the most advanced) in the world as of 2015,[261]:31 and connected to over 500 malware infections in at least 42 countries over many years, is suspected of being a part of NSA.[262][263] The group’s known espionage methods have been documented to include interdiction (interception of legitimate CDs sent by a scientific conference organizer by mail),[261]:15 and the “unprecedented” ability to infect and be transmitted through the hard drive firmware of several of the major hard drive manufacturers, and create and use hidden disk areas and virtual disk systems for its purposes, a feat demanding access to the manufacturer’s source code of each to achieve.[261]:16–18 The methods used to deploy the tools demonstrated “surgical precision”, going so far as to exclude specific countries by IP and allow targeting of specific usernames on discussion forums.[261]:23–26 The techniques and knowledge used by the Equation Group are considered in summary to be “out of the reach of most advanced threat groups in the world except [this group].[261]:31
Software backdoors
Linux kernel
Linus Torvalds, the founder of Linux kernel, joked during a LinuxCon keynote on September 18, 2013 that the NSA, who are the founder of SELinux, wanted a backdoor in the kernel.[264] However, later, Linus’ father, a Member of the European Parliament (MEP), revealed that the NSA actually did this.[265]
When my oldest son was asked the same question: “Has he been approached by the NSA about backdoors?” he said “No”, but at the same time he nodded. Then he was sort of in the legal free. He had given the right answer, everybody understood that the NSA had approached him.
— Nils Torvalds, LIBE Committee Inquiry on Electronic Mass Surveillance of EU Citizens – 11th Hearing, 11 November 2013[266]
Microsoft Windows
_NSAKEY was a variable name discovered in Microsoft‘s Windows NT 4 Service Pack 5 (which had been released unstripped of its symbolic debugging data) in August 1999 by Andrew D. Fernandes of Cryptonym Corporation. That variable contained a 1024-bit public key.
IBM Notes
IBM Notes was the first widely adopted software product to use public key cryptography for client–server and server–server authentication and for encryption of data. Until US laws regulating encryption were changed in 2000, IBM and Lotus were prohibited from exporting versions of Notes that supported symmetric encryption keys that were longer than 40 bits. In 1997, Lotus negotiated an agreement with the NSA that allowed export of a version that supported stronger keys with 64 bits, but 24 of the bits were encrypted with a special key and included in the message to provide a “workload reduction factor” for the NSA. This strengthened the protection for users of Notes outside the US against private-sector industrial espionage, but not against spying by the US government.[267][268]
Boomerang routing
While it is assumed that foreign transmissions terminating in the U.S. (such as a non-U.S. citizen accessing a U.S. website) subject non-U.S. citizens to NSA surveillance, recent research into boomerang routing has raised new concerns about the NSA’s ability to surveil the domestic Internet traffic of foreign countries.[18] Boomerang routing occurs when an Internet transmission that originates and terminates in a single country transits another. Research at the University of Toronto has suggested that approximately 25% of Canadian domestic traffic may be subject to NSA surveillance activities as a result of the boomerang routing of Canadian Internet service providers.[18]
Hardware implanting
Intercepted packages are opened carefully by NSA employees
A “load station” implanting a beacon
A document included in NSA files released with Glenn Greenwald‘s book No Place to Hide details how the agency’s Tailored Access Operations (TAO) and other NSA units gain access to hardware. They intercept routers, servers and other network hardware being shipped to organizations targeted for surveillance and install covert implant firmware onto them before they are delivered. This was described by an NSA manager as “some of the most productive operations in TAO because they preposition access points into hard target networks around the world.”[269]
Computers seized by the NSA due to interdiction are often modified with a physical device known as Cottonmouth.[270] Cottonmouth is a device that can be inserted in the USB port of a computer in order to establish remote access to the targeted machine. According to NSA’s Tailored Access Operations (TAO) group implant catalog, after implanting Cottonmouth, the NSA can establish Bridging (networking) “that allows the NSA to load exploit software onto modified computers as well as allowing the NSA to relay commands and data between hardware and software implants.”[271]
Role in scientific research and development
NSA has been involved in debates about public policy, both indirectly as a behind-the-scenes adviser to other departments, and directly during and after Vice Admiral Bobby Ray Inman‘s directorship. NSA was a major player in the debates of the 1990s regarding the export of cryptography in the United States. Restrictions on export were reduced but not eliminated in 1996.
Its secure government communications work has involved the NSA in numerous technology areas, including the design of specialized communications hardware and software, production of dedicated semiconductors (at the Ft. Meade chip fabrication plant), and advanced cryptography research. For 50 years, NSA designed and built most of its computer equipment in-house, but from the 1990s until about 2003 (when the U.S. Congress curtailed the practice), the agency contracted with the private sector in the fields of research and equipment.[272]
Data Encryption Standard
NSA was embroiled in some minor controversy concerning its involvement in the creation of the Data Encryption Standard (DES), a standard and public block cipher algorithm used by the U.S. government and banking community. During the development of DES by IBM in the 1970s, NSA recommended changes to some details of the design. There was suspicion that these changes had weakened the algorithm sufficiently to enable the agency to eavesdrop if required, including speculation that a critical component—the so-called S-boxes—had been altered to insert a “backdoor” and that the reduction in key length might have made it feasible for NSA to discover DES keys using massive computing power. It has since been observed that the S-boxes in DES are particularly resilient against differential cryptanalysis, a technique which was not publicly discovered until the late 1980s, but which was known to the IBM DES team.
The United States Senate Select Committee on Intelligence reviewed NSA’s involvement, and concluded that while the agency had provided some assistance, it had not tampered with the design.[273][274] In late 2009 NSA declassified information stating that “NSA worked closely with IBM to strengthen the algorithm against all except brute force attacks and to strengthen substitution tables, called S-boxes. Conversely, NSA tried to convince IBM to reduce the length of the key from 64 to 48 bits. Ultimately they compromised on a 56-bit key.”[275][276]
Advanced Encryption Standard
The involvement of NSA in the selection of a successor to Data Encryption Standard (DES), the Advanced Encryption Standard (AES), was limited to hardware performance testing (see AES competition).[277] NSA has subsequently certified AES for protection of classified information (for at most two levels, e.g. SECRET information in an unclassified environment[clarification needed]) when used in NSA-approved systems.[278]
NSA encryption systems
The NSA is responsible for the encryption-related components in these legacy systems:
The NSA oversees encryption in following systems which are in use today:
The NSA has specified Suite A and Suite B cryptographic algorithm suites to be used in U.S. government systems; the Suite B algorithms are a subset of those previously specified by NIST and are expected to serve for most information protection purposes, while the Suite A algorithms are secret and are intended for especially high levels of protection.[278]
SHA
The widely used SHA-1 and SHA-2 hash functions were designed by NSA. SHA-1 is a slight modification of the weaker SHA-0 algorithm, also designed by NSA in 1993. This small modification was suggested by NSA two years later, with no justification other than the fact that it provides additional security. An attack for SHA-0 that does not apply to the revised algorithm was indeed found between 1998 and 2005 by academic cryptographers. Because of weaknesses and key length restrictions in SHA-1, NIST deprecates its use for digital signatures, and approves only the newer SHA-2 algorithms for such applications from 2013 on.[288]
A new hash standard, SHA-3, has recently been selected through the competition concluded October 2, 2012 with the selection of Keccak as the algorithm. The process to select SHA-3 was similar to the one held in choosing the AES, but some doubts have been cast over it,[289][290] since fundamental modifications have been made to Keccak in order to turn it into a standard.[291] These changes potentially undermine the cryptanalysis performed during the competition and reduce the security levels of the algorithm.[289]
Dual_EC_DRBG random number generator cryptotrojan
NSA promoted the inclusion of a random number generator called Dual_EC_DRBG in the U.S. National Institute of Standards and Technology‘s 2007 guidelines. This led to speculation of a backdoor which would allow NSA access to data encrypted by systems using that pseudo random number generator.[292]
This is now deemed to be plausible based on the fact that the output of the next iterations of the PRNG can provably be determined if the relation between two internal elliptic curve points is known.[293][294] Both NIST and RSA are now officially recommending against the use of this PRNG.[295][296]
Clipper chip
Because of concerns that widespread use of strong cryptography would hamper government use of wiretaps, NSA proposed the concept of key escrow in 1993 and introduced the Clipper chip that would offer stronger protection than DES but would allow access to encrypted data by authorized law enforcement officials.[297] The proposal was strongly opposed and key escrow requirements ultimately went nowhere.[298] However, NSA’s Fortezza hardware-based encryption cards, created for the Clipper project, are still used within government, and NSA ultimately declassified and published the design of the Skipjack cipher used on the cards.[299][300]
Perfect Citizen
Perfect Citizen is a program to perform vulnerability assessment by the NSA on U.S. critical infrastructure.[301][302] It was originally reported to be a program to develop a system of sensors to detect cyber attacks on critical infrastructure computer networks in both the private and public sector through a network monitoring system named Einstein.[303][304] It is funded by the Comprehensive National Cybersecurity Initiative and thus far Raytheon has received a contract for up to $100 million for the initial stage.
Academic research
NSA has invested many millions of dollars in academic research under grant code prefix MDA904, resulting in over 3,000 papers (as of 2007-10-11). NSA/CSS has, at times, attempted to restrict the publication of academic research into cryptography; for example, the Khufu and Khafre block ciphers were voluntarily withheld in response to an NSA request to do so. In response to a FOIA lawsuit, in 2013 the NSA released the 643-page research paper titled, “Untangling the Web: A Guide to Internet Research,[305] ” written and compiled by NSA employees to assist other NSA workers in searching for information of interest to the agency on the public Internet.[306]
Patents
NSA has the ability to file for a patent from the U.S. Patent and Trademark Office under gag order. Unlike normal patents, these are not revealed to the public and do not expire. However, if the Patent Office receives an application for an identical patent from a third party, they will reveal NSA’s patent and officially grant it to NSA for the full term on that date.[307]
One of NSA’s published patents describes a method of geographically locating an individual computer site in an Internet-like network, based on the latency of multiple network connections.[308] Although no public patent exists, NSA is reported to have used a similar locating technology called trilateralization that allows real-time tracking of an individual’s location, including altitude from ground level, using data obtained from cellphone towers.[309]
Controversy
Excerpt from when James Clapper lied to Congress on NSA surveillance programs
In the United States, at least since 2001,[310] there has been legal controversy over what signal intelligence can be used for and how much freedom the National Security Agency has to use signal intelligence.[311] The government has made, in 2015, slight changes in how it uses and collects certain types of data,[312] specifically phone records. President Barack Obama has asked lawyers and his national security team to look at the tactics that are being used by the NSA. President Obama made a speech on January 17, 2014 where he defended the national security measures, including the NSA, and their intentions for keeping the country safe through surveillance. He said that it is difficult to determine where the line should be drawn between what is too much surveillance and how much is needed for national security because technology is ever changing and evolving. Therefore, the laws cannot keep up with the rapid advancements.
President Obama did make some changes to national security regulations and how much data can be collected and surveyed.[citation needed] The first thing he added, was more presidential directive and oversight so that privacy and basic rights are not violated. The president would look over requests on behalf of American citizens to make sure that their personal privacy is not violated by the data that is being requested. Secondly, surveillance tactics and procedures are becoming more public, including over 40 rulings of the FISC that have been declassified.[citation needed] Thirdly, further protections are being placed on activities that are justified under Section 702, such as the ability to retain, search and use data collected in investigations, which allows the NSA to monitor and intercept interaction of targets overseas. Finally, national security letters, which are secret requests for information that the FBI uses in their investigations, are becoming less secretive. The secrecy of the information requested will not be indefinite and will terminate after a set time if future secrecy is not required.[citation needed] Concerning the bulk surveillance of American’s phone records, President Obama also ordered a transition from bulk surveillance under Section 215 to a new policy that will eliminate unnecessary bulk collection of metadata.
As of May 7, 2015, the U.S. Court of Appeals for the Second Circuit ruled that the interpretation of Section 215 of the Patriot Act was wrong and that the NSA program that has been collecting Americans’ phone records in bulk is illegal.[313] It stated that Section 215 cannot be clearly interpreted to allow government to collect national phone data and, as a result, expired on June 1, 2015. This ruling “is the first time a higher-level court in the regular judicial system has reviewed the N.S.A. phone records program.” [314] The new bill getting passed later in May taking its place is known as the U.S.A. Freedom Act, which will enable the NSA to continue hunting for terrorists by analyzing telephone links between callers but “keep the bulk phone records in the hands of phone companies.”[314] This would give phone companies the freedom to dispose the records in an 18-month period. The White House argued that this new ruling validated President Obama’s support of the government being extracted from bulk data collection and giving power to the telecommunications companies.
Previously, the NSA paid billions of dollars to telecommunications companies in order to collect data from them.[315] While companies such as Google and Yahoo! claim that they do not provide “direct access” from their servers to the NSA unless under a court order,[316] the NSA had access to emails, phone calls and cellular data users.[317] With this new ruling, telecommunications companies would not provide the NSA with bulk information. The companies would allow the disposal of data in every 18 months,[314] which is arguably putting the telecommunications companies at a higher advantage.
This ruling made the collecting of phone records illegal, but it did not rule on Section 215’s constitutionality. Senate Majority Leader Mitch McConnell has already put forth a new bill to re-authorize the Patriot Act.[318] Defenders of this surveillance program are claiming that judges who sit on the Foreign Intelligence Surveillance Court (FISC) had ruled 37 times that this kind of collection of data is, in fact, lawful.[318] The FISC is the court specifically mandated to grant surveillance orders in the name of foreign intelligence. The new ruling made by the Second District Court of Appeals now retroactively dismisses the findings of the FISC on this program.
See also
Notes




















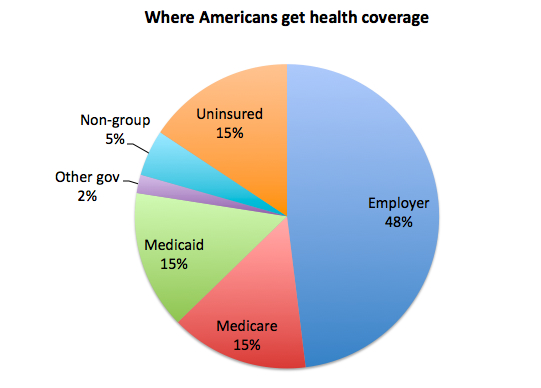





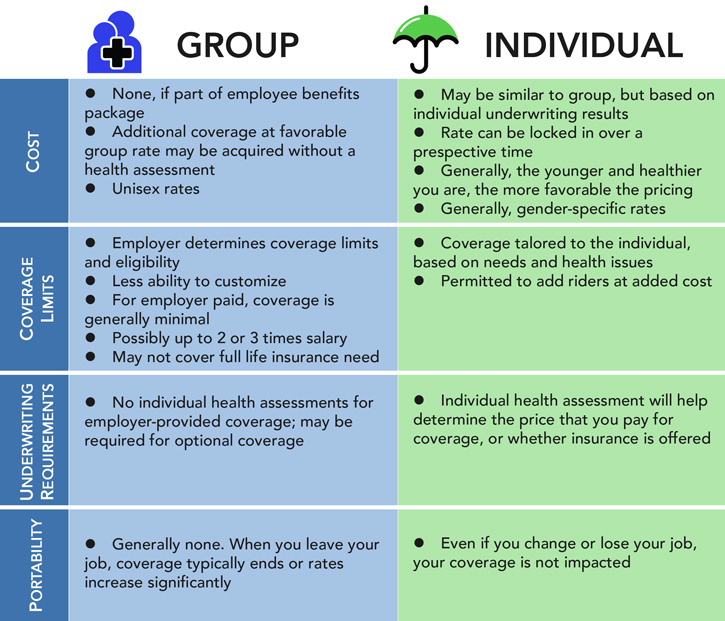


































 Trump lashes out over reported obstruction of justice probe
Trump lashes out over reported obstruction of justice probe










































































































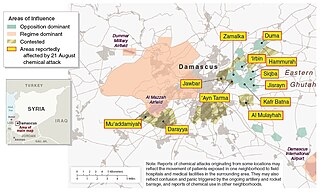






























































































































































































































































The Pronk Pops Show 1183, December 6, 2018, Story 1: The Smoking Gun Email Chain of The Clinton Obama Democrat Criminal Conspiracy — Videos — Story 2: Time Running Out For $25 Billion of Federal Funding of Wall — Trump Should Not Sign Any Bills Without Inclusion of Wall Funding of $25 Billion — Shut Government Down — Videos — Story 3: President Trump Will Nominate Former U.S. Attorney General William Barr as Permanent Replacement for Former AG Jeff Sessions — Videos — Story 4: United States Net Oil Exporter — First Time Since 1949 — Videos
Posted on December 7, 2018. Filed under: 2016 Presidential Candidates, 2018 United States Elections, Addiction, American History, Applications, Barack H. Obama, Benghazi, Bill Clinton, Blogroll, Breaking News, Bribery, Bribes, Budgetary Policy, Cartoons, Central Intelligence Agency, Clinton Obama Democrat Criminal Conspiracy, Communications, Computers, Congress, Constitutional Law, Corruption, Countries, Crime, Culture, Deep State, Defense Spending, Disasters, Donald J. Trump, Donald J. Trump, Donald Trump, Economics, Education, Elections, Empires, Employment, Energy, European History, Fast and Furious, Federal Bureau of Investigation (FBI), Federal Bureau of Investigation (FBI) and Department of Justice (DOJ), Federal Government, Fifth Amendment, First Amendment, Fiscal Policy, Foreign Policy, Former President Barack Obama, Fourth Amendment, Freedom of Speech, Government, Government Dependency, Government Spending, Hardware, Health, Health Care, Health Care Insurance, High Crimes, Hillary Clinton, Hillary Clinton, Hillary Clinton, Hillary Clinton, Hillary Clinton, History, House of Representatives, Human, Human Behavior, Illegal Immigration, Illegal Immigration, Immigration, Independence, Iran Nuclear Weapons Deal, James Comey, Law, Legal Immigration, Libya, Life, Lying, Media, Mexico, Middle East, Monetary Policy, National Interest, National Security Agency, Natural Gas, Natural Gas, News, Obama, Oil, Oil, People, Philosophy, Photos, Politics, President Trump, Public Corruption, Public Relations, Qatar, Radio, Rand Paul, Raymond Thomas Pronk, Regulation, Resources, Robert S. Mueller III, Rule of Law, Saudi Arabia, Scandals, Second Amendment, Senate, Servers, Social Networking, South America, South Korea, Spying, Spying on American People, Surveillance and Spying On American People, Surveillance/Spying, Tax Policy, Taxation, Taxes, Technology, Ted Cruz, Treason, Trump Surveillance/Spying, Unemployment, United Kingdom, United States Constitution, United States of America, United States Supreme Court, Videos, Violence, War, Wealth, Wisdom | Tags: 6 December 2018, America, Articles, Audio, Breaking News, Broadcasting, Capitalism, Cartoons, Charity, Citizenship, Clarity, Classical Liberalism, Clinton Obama Democrat Criminal Conspiracy, Collectivism, Commentary, Commitment, Communicate, Communication, Concise, Convincing, Courage, Culture, Current Affairs, Current Events, Department of Justice (DOJ), Destruction of Government Records and Classified Documents, E-Mail Chain, Economic Growth, Economic Policy, Economics, Education, Evil, Experience, Faith, Family, Federal Bureau of Investigation (FBI), Felonies, First, FISA Court Warrant Application Omissions, Fiscal Policy, Foreign Intelligence Surveillance Act, Foreign Intelligence Surveillance Act (FISA) Amendments Act (FAA), former Deputy FBI Director Andrew McCabe, Former FBI Director James Comey, Fracking, Free Enterprise, Freedom, Freedom of Speech, Friends, Funding The Wall, Give It A Listen!, God, Good, Goodwill, Growth, Hope, Individualism, Knowledge, Liberty, Life, Love, Lovers of Liberty, Mishandling of Classified Documents, Monetary Policy, MPEG3, News, No One Is Above The Law, Obstruction of Justice, Opinions, Peace, Photos, Plotters, Podcasts, Political Philosophy, Politics, President Trump Will Nominate Former U.S. Attorney General William Barr as Permanent Replacement for Former AG Jeff Sessions, Prosperity, Public Corruption, Radio, Raymond Thomas Pronk, Representative Republic, Republic, Resources, Respect, Rule of Law, Rule of Men, Show Notes, Shutting Down Big Government Departments, Spying on American People, Talk Radio, The Pronk Pops Show, The Pronk Pops Show 1182, The Smoking Gun Email Chain of The Clinton Obama Democrat Criminal Conspiracy, Time Running Out For $25 Billion of Federal Funding of Wall, Truth, Tyranny, U.S. Constitution, United States of America, Videos, Virtue, War, William Barr To Be nominated Attorney General, Wisdom |
The Pronk Pops Show Podcasts
Pronk Pops Show 1183 December 6, 2018
Pronk Pops Show 1182 December 5, 2018
Pronk Pops Show 1181 December 4, 2018
Pronk Pops Show 1180 December 3, 2018
Pronk Pops Show 1179 November 27, 2018
Pronk Pops Show 1178 November 26, 2018
Pronk Pops Show 1177 November 20, 2018
Pronk Pops Show 1176 November 19, 2018
Pronk Pops Show 1175 November 16, 2018
Pronk Pops Show 1174 November 15, 2018
Pronk Pops Show 1173 November 14, 2018
Pronk Pops Show 1172 November 9, 2018
Pronk Pops Show 1171 November 8, 2018
Pronk Pops Show 1170 November 7, 2018
Pronk Pops Show 1169 November 5, 2018
Pronk Pops Show 1168 November 2, 2018
Pronk Pops Show 1167 November 1, 2018
Pronk Pops Show 1166 October 31, 2018
Pronk Pops Show 1165 October 30, 2018
Pronk Pops Show 1164 October 29, 2018
Pronk Pops Show 1163 October 26, 2018
Pronk Pops Show 1162 October 24, 2018
Pronk Pops Show 1161 October 23, 2018
Pronk Pops Show 1160 October 22, 2018
Pronk Pops Show 1159 October 19, 2018
Pronk Pops Show 1158 October 18, 2018
Pronk Pops Show 1157 October 16, 2018
Pronk Pops Show 1156 October 15, 2018
Pronk Pops Show 1155 October 12, 2018
Pronk Pops Show 1154 October 11, 2018
Pronk Pops Show 1153 October 10, 2018
Pronk Pops Show 1152 October 5, 2018
Pronk Pops Show 1151 October 4, 2018
Pronk Pops Show 1150 October 3, 2018
Pronk Pops Show 1149, October 1, 2018
Pronk Pops Show 1148, September 28, 2018
Pronk Pops Show 1147, September 27, 2018
Pronk Pops Show 1146, September 25, 2018
Pronk Pops Show 1145, September 24, 2018
Pronk Pops Show 1144, September 20, 2018
Pronk Pops Show 1143, September 19, 2018
Pronk Pops Show 1142, September 18, 2018
Pronk Pops Show 1141, September 17, 2018
Pronk Pops Show 1140, September 14, 2018
Pronk Pops Show 1139, September 13, 2018
Pronk Pops Show 1138, September 12, 2018
Pronk Pops Show 1137, September 7, 2018
Pronk Pops Show 1136, September 6, 2018
Pronk Pops Show 1135, September 5, 2018
Pronk Pops Show 1134, September 4, 2018
Clinton Obama Democrat Criminal Conspiracy
Story 1: The Smoking Gun Email Chain of The Clinton Obama Democrat Criminal Conspiracy — Videos —
Sean Hannity 12/6/18 – Hannity Fox News December 6, 2018
Sean Hannity Fox News 12/6/18 Breaking Fox News December 6, 2018
Hannity 12/06/18 1AM | December 06, 2018 Breaking News
FBI email chain may provide most damning evidence of FISA abuses yet
12/5/2018
By John Solomon
Opinion Contributor
Just before Thanksgiving, House Republicans amended the list of documents they’d like President Trump to declassify in the Russia investigation. With little fanfare or explanation, the lawmakers, led by House Intelligence Committee Chairman Devin Nunes (R-Calif.), added a string of emails between the FBI and the Department of Justice (DOJ) to their wish list.
Sources tell me the targeted documents may provide the most damning evidence to date of potential abuses of the Foreign Intelligence Surveillance Act (FISA), evidence that has been kept from the majority of members of Congress for more than two years.
The email exchanges included then-FBI Director James Comey, key FBI investigators in the Russia probe and lawyers in the DOJ’s national security division, and they occurred in early to mid-October, before the FBI successfully secured a FISA warrant to spy on Trump campaign adviser Carter Page.
The email exchanges show the FBI was aware — before it secured the now-infamous warrant — that there were intelligence community concerns about the reliability of the main evidence used to support it: the Christopher Steele dossier.
The exchanges also indicate FBI officials were aware that Steele, the former MI6 British intelligence operative then working as a confidential human source for the bureau, had contacts with news media reporters before the FISA warrant was secured.
The FBI fired Steele on Nov. 1, 2016 — two weeks after securing the warrant — on the grounds that he had unauthorized contacts with the news media.
But the FBI withheld from the American public and Congress, until months later, that Steele had been paid to find his dirt on Trump by a firm doing political opposition research for the Democratic Party and for Democratic presidential candidate Hillary Clinton, and that Steele himself harbored hatred for Trump.
If the FBI knew of his media contacts and the concerns about the reliability of his dossier before seeking the warrant, it would constitute a serious breach of FISA regulations and the trust that the FISA court places in the FBI.
That’s because the FBI has an obligation to certify to the court before it approves FISA warrants that its evidence is verified, and to alert the judges to any flaws in its evidence or information that suggest the target might be innocent.
We now know the FBI used an article from Yahoo News as independent corroboration for the Steele dossier when, in fact, Steele had talked to the news outlet.
If the FBI knew Steele had that media contact before it submitted the article, it likely would be guilty of circular intelligence reporting, a forbidden tactic in which two pieces of evidence are portrayed as independent corroboration when, in fact, they originated from the same source.
These issues are why the FBI email chain, kept from most members of Congress for the past two years, suddenly landed on the declassification list.
The addition to the list also comes at a sensitive time, as House Republicans prepare on Friday to question Comey, who signed off on the FISA warrant while remaining an outlier in the intelligence community about the Steele dossier.
Most intelligence officials, such as former CIA Director John Brennan and former Director of National Intelligence James Clapper, have embraced the concerns laid out in the Steele dossier of possible — but still unproven — collusion between the Trump campaign and Russia.
Yet, 10 months after the probe started and a month after Robert Mueller was named special counsel in the Russia probe, Comey cast doubt on the the Steele dossier, calling it “unverified” and “salacious” in sworn testimony before Congress.
Former FBI lawyer Lisa Page further corroborated Comey’s concerns in recent testimony before House lawmakers, revealing that the FBI had not corroborated the collusion charges by May 2017, despite nine months of exhaustive counterintelligence investigation.
Lawmakers now want to question Comey about whether the information in the October email string contributed to the former FBI director’s assessment.
The question long has lingered about when the doubts inside the FBI first surfaced about the allegations in the Steele dossier.
Sources tell me the email chain provides the most direct evidence that the bureau, and possibly the DOJ, had reasons to doubt the Steele dossier before the FISA warrant was secured.
Sources say the specifics of the email chain remain classified, but its general sentiments about the Steele dossier and the media contacts have been discussed in nonclassified settings.
“If these documents are released, the American public will have clear and convincing evidence to see the FISA warrant that escalated the Russia probe just before Election Day was flawed and the judges [were] misled,” one knowledgeable source told me.
Congressional investigators also have growing evidence that some evidence inserted into the fourth and final application for the FISA — a document signed by current Deputy Attorney General Rod Rosenstein — was suspect.
Nunes hinted as much himself in comments he made on Sean Hannity’s Fox News TV show on Nov. 20, when he disclosed the FBI email string was added to the declassification request. The release of the documents will “give finality to everyone who wants to know what their government did to a political campaign” and verify that the Trump campaign did not collude with Russia during the election, Nunes said.
As more of the secret evidence used to justify the Russia probe becomes public, an increasingly dark portrait of the FBI’s conduct emerges.
The bureau, under a Democratic-controlled Justice Department, sought a warrant to spy on the duly nominated GOP candidate for president in the final weeks of the 2016 election, based on evidence that was generated under a contract paid by his political opponent.
That evidence, the Steele dossier, was not fully vetted by the bureau and was deemed unverified months after the warrant was issued.
At least one news article was used in the FISA warrant to bolster the dossier as independent corroboration when, it fact, it was traced to a news organization that had been in contact with Steele, creating a high likelihood it was circular intelligence reporting.
And the entire warrant, the FBI’s own document shows, was being rushed to approval by two agents who hated Trump and stated in their own texts that they wanted to “stop” the Republican from becoming president.
If ever there were grounds to investigate the investigators, these facts provide the justification.
Director Comey and Deputy Attorney General Rosenstein likely hold the answers, as do the still-classified documents. It’s time all three be put under a public microscope.
John Solomon is an award-winning investigative journalist whose work over the years has exposed U.S. and FBI intelligence failures before the Sept. 11 attacks, federal scientists’ misuse of foster children and veterans in drug experiments, and numerous cases of political corruption. He is The Hill’s executive vice president for video.
https://thehill.com/hilltv/rising/419901-fbi-email-chain-may-provide-most-damning-evidence-of-fisa-abuses-yet
FBI Knew Steele Dossier Was Bogus Before Using In FISA Application: Solomon
The email exchanges – kept from Congressional investigators for over two years, “included then-FBI Director James Comey, key FBI investigators in the Russia probe and lawyers in the DOJ’s national security division,” according to the report – and took place in early to mid-October of 2016, prior to the FBI successfully securing a FISA warrant to spy on Trump campaign adviser Carter Page.
Also withheld from both Congress and the general public until months later is the fact that Steele had been paid by Fusion GPS – an opposition research firm hired by Hillary Clinton and the DNC to dig up dirt on Donald Trump. Moreover, Steele absolutely hated Donald Trump.
And as Solomon notes; “If the FBI knew of his media contacts and the concerns about the reliability of his dossier before seeking the warrant, it would constitute a serious breach of FISA regulations and the trust that the FISA court places in the FBI.”
The FBI, however, went to extreme lengths to convince the FISA judge that Steele (“Source #1”), was reliable when they could not verify the unsubstantiated claims in his dossier – while also having to explain why they still trusted his information after having terminated Steele’s contract over inappropriate disclosures he made to the media.
120 people are talking about this
Of course, none of this mattered to the FBI – which painted Carter Page in the most criminal light possible, as intended, in order to convince the FISA judge to grant the warrant.In order to reinforce their argument, the FBI presented various claims from the dossier as facts, such as “The FBI learned that Page met with at least two Russian officials” – when in fact that was simply another unverified claim from the dossier.
It flat out accuses Page of being a Russian spy who was recruited by the Kremlin, which sought to “undermine and influence the outcome of the 2016 U.S. presidential election in violation of U.S. criminal law,” the application reads.
1,291 people are talking about this
View image on Twitter
1,718 people are talking about this
Another approach used to beef up the FISA application’s curb appeal was circular evidence, via the inclusion of a letter from Democratic Senate Minority Leader Harry Reid (NV) to former FBI Director James Comey, citing information Reid got from John Brennan, which was in turn from the Clinton-funded dossier.
Congressional investigators now want to question Comey about the October email string and whether it contributed to his assessment. According to Solomon, the newly requested email chain “provides the most direct evidence that the bureau, and possibly the DOJ, had reasons to doubt the Steele dossier before the FISA warrant was secured.”
“If these documents are released, the American public will have clear and convincing evidence to see the FISA warrant that escalated the Russia probe just before Election Day was flawed and the judges [were] misled,” one source told Solomon.
What’s more, House GOP investigators now have a growing pile of evidence that some of the information inserted into a fourth and final application for the FISA – signed by Deputy Attorney General Rod Rosenstein, was suspect – as evidence by hints by House Intelligence Committee member Devin Nunes (R-CA) on Fox News‘s Sean Hannity TV show November 20. Nunes said that the declassification of the requested documents will “give finality to everyone who wants to know what their government did to a political campaign.”
As Solomon bluntly puts it:
No wonder Comey wanted a public testimony – where he wouldn’t have to discuss any of this.
https://www.zerohedge.com/news/2018-12-06/fbi-knew-steele-dossier-was-bogus-using-fisa-application-solomon
Obama Political Spying Scandal: Trump Associates Were Not the First Targets
By ANDREW C. MCCARTHY
This list includes Dennis Kucinich and investigative journalists.In 2011, Dennis Kucinich was still a Democratic congressman from Ohio. But he was not walking in lockstep with President Obama — at least not on Libya. True to his anti-war leanings, Kucinich was a staunch opponent of Obama’s unauthorized war against the Qaddafi regime.
Kucinich’s very public efforts included trying to broker negotiations between the administration and the Qaddafi regime, to whom the White House was turning a deaf ear. It was in that context that he took a call in his Washington office from Saif al-Islam Qaddafi, the ruler’s son and confidant. Four years later, as he recalled in a recent opinion piece, Kucinich learned that the call had been recorded and leaked to the Washington Times.
To be sure, it is not a solid case. Kucinich is now a commentator at Fox News, on whose website he explains his side of the story, and on whose programming ardently pro-Trump contributors are a staple — including contributors who have been sympathetic to the new president’s claim that he was monitored by his predecessor. The gist of Kucinich’s piece is to “vouch for the fact that extracurricular surveillance does occur.” The express point is to counter the ridicule heaped on Trump’s claim that he personally was wiretapped at Trump Tower.
As we’ve repeatedly noted (see, e.g., here, here, and here), there is no known support for Trump’s narrow claim (made in a series of March 4 tweets). Yet, there is now overwhelming evidence that the Obama administration monitored Trump associates and campaign and transition officials. There were, moreover, leaks of classified information to the media — particularly in the case of Trump’s original national-security adviser, Michael Flynn, whose telephone communications with Russia’s ambassador to the U.S. were unlawfully disclosed to the Washington Post.
The answer is no.
In an important analysis published by Tablet magazine, Lee Smith considers the likely abuse of foreign-intelligence-collection authority by the Obama administration in connection with negotiations over Iran’s nuclear program. The White House knew there would be vigorous Israeli opposition to the Iran deal — just as there was ardent American opposition to the highly objectionable pact. Notwithstanding that Israel is an important ally, Prime Minister Benjamin Netanyahu and Ron Dermer, Israel’s ambassador to the U.S., became surveillance targets — agents of a foreign power, treated no differently under the law than such operatives of hostile foreign powers. Fair enough — it is simply a fact that allies occasionally spy on each other. Obviously, their interests sometimes diverge.
But there was something different about this monitoring initiative. It was not targeted merely at Israeli officials plotting their opposition strategy. The Wall Street Journal, Smith notes, reported in late December 2015 that the targeting “also swept up the contents of some of [the Israeli officials’] private conversations with U.S. lawmakers and American-Jewish groups.”
Do you really think the Obama administration, which turned the Internal Revenue Service and the Justice Department into process cudgels for beating Obama detractors, would be above that sort of thing?
At her website, Sharyl Attkisson provides a very useful “Obama-era Surveillance Timeline” — with “surveillance” broadly construed to encompass many varieties of government power to collect and coerce the production of information. Attkisson notes, for example:
‐The IRS’s targeting of conservative groups seeking tax-exempt status, a politicized initiative that stymied the groups’ ability to contest Obama’s reelection in 2012.
‐The administration’s targeting of journalists, including (a) attorney general Eric Holder’s approval of the seizure of personal and business phone records of Associated Press reporters en masse (i.e., not a particularized search targeting a specific journalist suspected of wrongdoing); and (b) Holder’s approval of a warrant targeting the e-mails of Fox News reporter James Rosen in a leak investigation — based on an application in which the government represented to a federal court that the journalist could be guilty of a felony violation of the Espionage Act in connection with a leak of classified information (in addition to purportedly being a “flight risk”).
‐The administration’s 2011 loosening of minimization procedures to enable more-liberal scrutiny of communications of American citizens incidentally swept up in foreign-intelligence gathering
‐The CIA’s accessing of Senate Intelligence Committee computers and staff e-mails — which CIA director John Brennan initially denied, then apologized for after it was confirmed by an inspector-general report.
‐The investigation of Trump associate Carter Page, including a Foreign Intelligence Surveillance Act warrant based on the claim that Page was a Russian agent, which would have authorized monitoring of Page’s communications — including any with Trump, then the Republican nominee for president.
‐The criminal leaking to the media of former Trump national-security adviser Michael Flynn’s communications with the Russian ambassador to the U.S.
‐The “unmasking” of identities of Americans (connected to Trump) at the behest of Obama national-security adviser Susan Rice, a White House staffer and Obama confidant.
Ms. Attkisson also has her own story to tell. Formerly at CBS News, she was one of the few journalists at mainstream outlets who aggressively reported on the Fast and Furious scandal and the Benghazi massacre. In the latter, we recall, Rice and other Obama officials falsely told the public that the attack, which resulted in the killing of four Americans including the U.S. ambassador, grew out of spontaneous protest against an anti-Muslim video (rather than being a coordinated jihadist strike). The Obama administration later used its criminal-prosecution authority to trump up a case against its chosen scapegoat: the video producer.
Attkisson’s reporting prompted internal administration complaints that she was “out of control.”
Based on examinations by two forensic experts, Attkisson and CBS eventually reported that her personal and work computers were “accessed by an unauthorized, external, unknown party on multiple occasions.” Was this “unknown party” the government? The experts say it was a highly advanced intruder, which “used sophisticated methods to remove all possible indications of unauthorized activity.” Moreover, one computer was infiltrated remotely by the use of “new spy software proprietary to a federal agency.”
It is a good bet that the National Security Agency was monitoring the communications of Qaddafi’s son and other regime figures in 2011. If so, it is likely that then-congressman Kucinich was lawfully intercepted “incidentally.” It is also entirely possible, however, that the Libyans themselves were recording their conversations with prominent Americans and that the Kucinich–Qaddafi call was found after the regime fell.
The Washington Times reporters did not reveal to Kucinich how they had gotten the tape, but the paper’s related stories had referred to “secret audio recordings recovered from Tripoli.” Moreover, if the Obama administration had been behind a vindictive leak against Kucinich, one might have expected the leak to have happened in 2011, during Kucinich’s prominent opposition to the Libya war, rather than four years later, when the regime had long been toppled and Kucinich had retired from Congress.
On the other hand, Kucinich recounts that the recording is very clear on both ends (one might expect a Libyan recording would be distinctly clearer on the Libyan end). The Washington Timesalso does not seem the most natural destination for a secret disclosure from Libya. Furthermore, Kucinich explains, he made routine FOIA requests regarding information pertinent to him before leaving Congress in 2012. Although he did not learn of the recording until 2015, these FOIA requests would have covered his communication with Qaddafi, he adds. Kucinich says that some of the intelligence agencies have failed to respond.
On its own, Dennis Kucinich’s story would not be worth telling — not as a tale of political spying intrigue. But can it so easily be dismissed after the spying on American critics of the Iran deal? The measures taken to make “incidental” monitoring of Americans easier, its fruits far more widely disseminated and, inevitably, criminally leaked? The shocking abuse of IRS processes to collect information on, and procedurally persecute, Barack Obama’s political adversaries? Fast and Furious — the use of government police powers to create a political anti-gun narrative, then the contemptuous cover-up when it went horribly wrong, resulting in a Border Patrol officer’s death? The scandalous Benghazi cover-up — including a bogus prosecution of a pathetic video producer to help prop up the fraud? The monitoring of Trump associates and members of his campaign and transition staffs — the unmasking, the intentional wide dissemination of raw intelligence, the willful felony publication of classified information?
There is considerably more evidence that the Obama administration grossly abused its awesome intelligence-gathering and law-enforcement powers than that Russian meddling had a meaningful impact on the 2016 election. And these abuses of power certainly did not start with the targeting of Donald Trump’s campaign.
— Andrew C. McCarthy is a senior policy fellow at the National Review Institute and a contributing editor of National Review.
Editor’s Note: This piece has been emended since its initial posting.
https://www.nationalreview.com/2017/04/barack-obama-spying-journalists-dennis-kucinich-sharyl-attkisson-donald-trump-campaign-transition/
Could the President Spy on His Political Opponents?
Under the government’s current interpretation of the law, unfortunately, the answer is yes.
By NEEMA GULIANI • March 22, 2017
he controversy continues over President Trump’s Twitter storm accusing President Obama of wiretapping him. On Monday, members of Congress peppered FBI Director James Comey with questions about the claims, who once again dismissed them as lacking support. Even Devin Nunes, the Republican chairman of the House Intelligence Committee, who originally defended Trump’s claims, has defected. “I don’t think there was an actual tap of Trump Tower,” the congressman said last week at a news conference. None of these statements seem to have affected President Trump, however, who continues to stand by his accusations.
But regardless of whether these claims turn out to be completely false, which is all but certain now, they do raise a question that shouldn’t be casually dismissed: Could President Obama’s administration have surveiled his political opponents under its interpretation of the law? Could President Trump’s administration now do the same?
The answer, unfortunately, is yes. And that should make Republicans and Democrats nervous enough to work together to reform our surveillance laws.
Many have dismissed President Trump’s accusations as the unsubstantiated ramblings of a Twitter addict with little understanding of how our intelligence laws work. These may be fair criticisms—today the president cannot simply order the intelligence agencies to wiretap his domestic political opponents. But many of our surveillance authorities have been interpreted so broadly that they put vast amounts of Americans’ data easily within the president’s reach. Without significant reform, exploiting this immense pool of data may one day prove irresistible. Thus, whether President Trump’s accusations are true or not, the potential for White House officials to abuse our spying laws for political purposes is real.
It is important to remember that surveilling political opponents in the name of security is something of an American pastime. In the 1960s, the FBI targeted political activists, including Martin Luther King Jr., claiming they posed “national security” threats. Cesar Chavez, the prominent labor and civil-rights activist, was similarly tracked for years because of his supposed communist ties.
In response to many of these types of abuses, Congress created the Church Committee to investigate surveillance practices. The widespread crimes and abuse they uncovered led to the passage of the Foreign Intelligence Surveillance Act (FISA) in 1978. But recent disclosures demonstrate that the law did not go far enough. Moreover, passage of the Patriot Act in 2001 and other laws have undercut the protections in FISA, further opening the door to biased, unjustified, or politically motivated spying. There are jarringly few protections against these abuses.
The result: if the president wanted to surveil his critics, he could exploit at least three national security authorities.
Section 702 of FISA
Section 702 of FISA was passed at the request of the Bush administration and extended at the request of the Obama administration with bipartisan support. Now the Trump administration is reportedly pushing for reauthorization of this law when it is set to expire in 2017, with the nominee for the director of national intelligence calling it the “crown jewels” of the intelligence community. FBI Director Comey once again defended the controversial program.
While Section 702 was passed to protect against international terrorism, its tentacles reach much farther. Under the law, the government collects emails and phone calls—without a warrant—of nearly 100,000 foreign “targets.” These include their conversations with people in the United States. These targets can include journalists, human-rights workers, and other individuals who have no connection to terrorism or criminal activity, and whose only offense may be discussing information related to “foreign affairs”—a nebulous term.
Over 250 million internet communications alone are collected under Section 702 annually. While the government refuses to disclose how many Americans have been swept up in this dragnet, analysis of leaked documents suggests that at least half those communications contain information about a U.S. citizen or resident. If that’s accurate, the Trump administration will collect over 125 million internet communications that contain information about someone in the United States. Given that much of the data collected under Section 702 is stored for five years or longer, it means the government likely has access to hundreds of millions of stored emails and phone calls.
Once collected, the government asserts that they can mine this information to scrutinize the activities of Americans—opening the door to political abuse. For example, if the intelligence agencies under President Obama had wanted to search through Section 702 data for information about Senate Majority Leader Mitch McConnell (R-Ky.), on the argument that McConnell might possess information about “foreign affairs,” no technological barrier or explicit provision in Section 702 would have stopped them. Under current procedures, no court would have needed to approve this and Senator McConnell would not need to be notified that he had been the subject of such a search.
Under the government’s current interpretation of the law, this information could then be used as the basis for a criminal prosecution, criminal investigation, civil action, or additional surveillance.
Executive Order (EO) 12333
Under Executive Order 12333, the government engages in the bulk collection of communications and data—with no approval from a court or any other independent judicial body. This surveillance primarily takes place abroad. While the government is not supposed to target Americans under EO 12333, this spying likely results in the collection of information of millions of Americans. We know, for example, that the government reportedly relied on EO 12333 to steal data transmitted between certain Yahoo and Google data centers; to capture the content of all phone calls to, from, and within the Bahamas and other countries; and to collect millions of text messages from individuals around the world.
Under EO 12333, the government can target foreigners for “foreign intelligence” purposes, which, similar to Section 702, is a category so broad that it easily encompasses individuals who have no nexus to a national-security threat. As a result of recent NSA procedures, agencies across the federal government now have the right to request access to the raw information collected under EO 12333, which can contain the information of both Americans and foreigners.
While NSA officials have said there are procedures that limit the ability of the NSA to search through electronic surveillance captured under EO 12333 for information about Americans, those procedures are largely secret and can be modified purely at the discretion of the president. Moreover, the government has taken the position that information collected under the executive order can be used to prosecute Americans for certain ordinary domestic crimes—even though it was collected without a warrant.
In practice, this means that if the president decided to unilaterally change EO 12333 procedures to allow him to search for information for purposes unrelated to national security, he would have broad latitude to do so under the government’s current legal interpretations. In addition, it means that if the government stumbles across information related to these individuals in the trove of data they collect, they may assert the right to use it as the basis to prosecute or further investigate these individuals, without ever notifying them. This creates a bizarre incentive for any ill-intentioned president: the more information collected under EO 12333 in the name of security, the more information that can be mined for other purposes.
“Traditional” FISA
Although FISA was passed with the admirable goal of halting many of the surveillance abuses of the 1960s, this statutory scheme is not nearly as protective as a warrant. Specifically, unlike an ordinary warrant or wiretapping order, a traditional FISA order does not require the government to believe that its spying will produce evidence of a crime, and the secrecy surrounding the FISA court undermines effective oversight. For these reasons, the ACLU has long cautioned that FISA authorities are prone to abuse.
Under FISA, when the government seeks to conduct electronic surveillance, it must submit an application to the secret intelligence court demonstrating that there is probable cause that its individual target is a “foreign power or an agent of a foreign power,” and it must identify the particular phone line or communications facility used by the target. The terms “foreign power or agent of a foreign power” are broadly defined. They include foreign government officials, foreign political organizations not substantially composed of U.S. citizens or green-card holders, and foreign individuals engaged in terrorism. While this authority is certainly narrower than EO 12333 or Section 702, it too leaves room for abuse.
For example, under traditional FISA, the government would have the authority to surveil virtually any foreign government official—including that official’s entirely legal conversations with individuals in the United States. These communications can be retained or disseminated under procedures that are more lenient than those that apply to federal wiretaps. For instance, in the wiretapping context, the government is supposed to immediately purge communications that are considered irrelevant. FISA, by contrast, permits retention, analysis, and dissemination of Americans’ information for years, regardless of whether there is any evidence of criminal activity.
The Potential for Abuse Is Real, No Matter What the Intel Community Says
The intelligence agencies would argue that these authorities do not permit the government to deliberately “target” Americans—at least not without a warrant—mitigating constitutional concerns. But that explanation only tells half the story. The reality is that these authorities are used to vacuum up large amounts of Americans’ data, do not prevent the government from knowingly capturing the communications that Americans have with tens of thousands of foreign “targets,” and, in some cases, routinely collect purely domestic communications. Moreover, once Americans’ information is collected, there are inadequate safeguards to ensure that such data is not inappropriately used.
The fact that our intelligence-gathering laws leave room for politically motivated surveillance should give us pause. And it’s not enough for President Trump or members of Congress to simply express outrage that the private communications of political leaders could have been surveilled. With the expiration of Section 702 looming, they have the opportunity to push for a complete overhaul of our surveillance authorities, and ensure that they are brought fully in line with the requirements of our Constitution.
In other words, President Trump should match his action to his tweets, and demand that Section 702 and other authorities be reformed.
Neema Singh Guliani is a legislative counsel at the ACLU focusing on surveillance, privacy, and national-security issues. Prior to the ACLU, she worked at the Department of Homeland Security and as an investigative counsel with the House Oversight and Government Reform Committee.
https://www.theamericanconservative.com/articles/could-the-president-spy-on-his-political-opponents/
Story 2: Time Running Out For Federal $25 Billion Funding Appropriation $25 Billion of for Trump’s Wall — Videos
Pelosi takes hard line on paying for Trump’s border wall
House Democratic Leader Nancy Pelosi of California, meets with reporters at her weekly news conference on Capitol Hill in Washington, Thursday, Dec. 6, 2018. (AP Photo/J. Scott Applewhite)
WASHINGTON (AP) — House Democratic leader Nancy Pelosi on Thursday rejected the idea of paying for President Donald Trump’s border wall in exchange for helping hundreds of thousands of young immigrants avoid deportation.
Funding for the wall — a top Trump priority — and legal protections for so-called Dreamers, a key Democratic goal, should not be linked, Pelosi said.
“They’re two different subjects,” she said.
Her comments came as the House and Senate approved a stopgap bill Thursday to keep the government funded through Dec. 21. The measure, approved by voice votes in near-empty chambers, now goes to the White House.
Trump has promised to sign the two-week extension to allow for ceremonies this week honoring former President George H.W. Bush, who died Nov. 30. But he wants the next funding package to include at least $5 billion for his proposed wall, something Democrats have rejected. Trump is set to meet Tuesday at the White House with Pelosi and Senate Democratic leader Chuck Schumer.
Pelosi, who is seeking to become House speaker in January, said the lame-duck Congress should now pass a half-dozen government funding bills that key committees have already agreed on, along with a separate measure funding the Department of Homeland Security, which oversees the border. Funding for the homeland agency should address border security and does not necessarily include a wall, Pelosi said.
Most Democrats consider the wall “immoral, ineffective and expensive,” Pelosi said, noting that Trump promised during the 2016 campaign that Mexico would pay for it, an idea Mexican leaders have repeatedly rejected.
Even if Mexico did pay for the wall, “it’s immoral still,” Pelosi said.
Protecting borders “is a responsibility we honor, but we do so by honoring our values as well,” she added.
Schumer said Thursday that a bipartisan Senate plan for $1.6 billion in border security funding does not include money for the 30-foot-high (9-meter-high) concrete wall Trump has envisioned. The money “can only be used for fencing” and technology that experts say is appropriate and makes sense as a security feature, Schumer said.
If Republicans object to the proposal because of pressure from Trump, Schumer said lawmakers should follow Pelosi’s advice and approve six appropriations bills and a separate measure extending current funding for Homeland Security.
Either option would avert a partial government shutdown, which lawmakers from both parties oppose, he said.
“The one and only way we approach a shutdown is if President Trump refuses both of our proposals and demands $5 billion or more for a border wall,” Schumer said. He called the wall “a nonstarter” for Democrats, who face increasing pressure from outside groups and liberal lawmakers to resist Trump’s continued push for the barrier, which Trump says is needed to stop an “invasion” of Central American migrants and others from crossing into the country illegally.
Schumer called the spat over the wall unnecessary, noting that the administration has not spent more than $1 billion approved for border security in the budget year that ended Sept. 30. “The idea that they haven’t spent last year’s money and they’re demanding such a huge amount this year makes no sense at all,” he said.
Senate Appropriations Committee Chairman Richard Shelby said he prefers to include Homeland Security in an omnibus package containing seven unresolved spending bills for the current budget year.
“I believe the best route is to keep all seven together and pass them,” the Alabama Republican told reporters Thursday. Lawmakers have “made a lot of progress” in recent weeks on the seven spending bills. “I’d like to conclude it,’” he said.
Missouri Sen. Roy Blunt, a member of Republican leadership, said the key question is whether Trump will sign a bill without funding for the wall.
“It doesn’t matter how much appetite there is for a shutdown anywhere else, if he is willing to have a shutdown over this issue,” Blunt said. “He has given every indication that he would.”
___
Associated Press writers Alan Fram and Padmananda Rama contributed to this story.
https://apnews.com/e3fd315c66554c22bfdf97710e0df711
Story 3: President Trump Will Nominate Former U.S. Attorney General William Bar as Permanent Replacement for Former AG Jeff Sessions
WASHINGTON (Reuters) – Former U.S. Attorney General William Barr, who served under former President George H.W. Bush, is the leading candidate for the job as a permanent replacement for Jeff Sessions, a source familiar with the matter said on Thursday.
The Washington Post reported earlier on Thursday that President Donald Trump could choose his nominee for attorney general in coming days, and that Trump had told advisers he plans to nominate Barr.
Sessions departed from the role last month, and Trump named Matthew Whitaker as the government’s top lawyer on an interim basis. With the current session of Congress set to soon end, anyone Trump nominates may have to wait until well into 2019 for confirmation.
Barr has worked in the private sector since serving as attorney general from 1991 to 1993, retiring from Verizon Communications (VZ.N) in 2008.
Reporting by Steve Holland and Lisa Lambert, Editing by David Gregorio and Bill Berkrot
Story 3: President Trump Will Nominate Former U.S. Attorney General William Bar as Permanent Replacement for Former AG Jeff Sessions — Videos
Trump eyeing Bush 41 attorney general to replace Sessions
President Trump To Tap Former Attorney General William Barr To Head Justice Department
William P. Barr
Jump to navigationJump to search
November 26, 1991 – January 20, 1993
May 1990 – November 26, 1991
April 1989 – May 1990
May 23, 1950 (age 68)
New York City, New York, U.S.
George Washington University(JD)
William Pelham Barr (born May 23, 1950) is an American attorney who served as the 77th Attorney General of the United States. He is a Republican and served as Attorney General from 1991 to 1993 during the administration of President George H. W. Bush.
Early life, education, and career
Barr was born in New York City. The son of Columbia University faculty members Mary and Donald Barr, he grew up on the Upper West Side, attended the Corpus Christi School and Horace Mann School. He received his B.A. degree in government in 1971 and his M.A. degree in government and Chinese studies in 1973, both from Columbia University. He received his J.D. degree with highest honors in 1977 from the George Washington University Law School.[1]
Barr with President Ronald Reaganin 1983
From 1973-77, he was employed by the Central Intelligence Agency. Barr was a law clerk to Judge Malcolm Wilkey of the U.S. Court of Appeals for the District of Columbia Circuit from 1977 through 1978. He served on the domestic policy staff at the Reagan White House from 1982 to 1983. He was also in private practice for nine years with the Washington law firm of Shaw, Pittman, Potts & Trowbridge.[2]
Department of Justice
Barr and Dan Quayle watch as President George H. W. Bush signs the Civil Rights Commission Reauthorization Act in the Rose Garden of the White House in 1991
During 1989, at the beginning of his administration, President George H. W. Bush appointed Barr to the U.S. Department of Justice as Assistant Attorney General for the Office of Legal Counsel, an office which functions as the legal advisor for the President and executive agencies. Barr was known as a strong defender of Presidential power and wrote advisory opinions justifying the U.S. invasion of Panama and arrest of Manuel Noriega, and a controversial opinion that the F.B.I. could enter onto foreign soil without the consent of the host government to apprehend fugitives wanted by the United States government for terrorism or drug-trafficking.[3]
During May 1990, Barr was appointed Deputy Attorney General, the official responsible for day-to-day management of the Department. According to media reports, Barr was generally praised for his professional management of the Department.[4]
Acting Attorney General of the United States
During August 1991, when then-Attorney General Richard Thornburgh resigned to campaign for the Senate, Barr was named Acting Attorney General.[5] Three days after Barr accepted that position, 121 Cuban inmates, awaiting deportation to Cuba as extremely violent criminals, seized 9 hostages at the Talladega federal prison. He directed the FBI’s Hostage Rescue Team to assault the prison, which resulted in rescuing all hostages without loss of life.[6]
Nomination and confirmation
It was reported that President Bush was impressed with Barr’s management of the hostage crisis, and weeks later, President Bush nominated him as Attorney General.[7]
Barr’s two-day confirmation hearing was “unusually placid” and he received a good reception from both Republicans and Democrats on the Senate Judiciary Committee.[8] Asked whether he thought a constitutional right to privacy included the right to an abortion, Barr responded that he believed the constitution was not originally intended to create a right to abortion; that Roe v. Wade was thus wrongly decided; and that abortion should be a “legitimate issue for state legislators”.[8] Committee Chairman, Senator Joe Biden, though disagreeing with Barr, responded that it was the “first candid answer” he had heard from a nominee on a question that witnesses would normally evade.[9] Barr was approved unanimously by the Senate Judiciary Committee. Chairman Biden hailed Barr as “a throwback to the days when we actually had attorneys general that would talk to you.”[9]
Attorney General of the United States
Tenure
Analysis
The media described Barr as staunchly conservative.[10] The New York Times described the “central theme” of his tenure to be: “his contention that violent crime can be reduced only by expanding Federal and state prisons to jail habitual violent offenders.”[10] At the same time, reporters consistently described Barr as affable with a dry, self-deprecating wit.[11]
Subsequent career
After his tenure at the Department of Justice, Barr spent more than 14 years as a senior corporate executive. At the end of 2008 he retired from Verizon Communications, having served as Executive Vice President and General Counsel of GTE Corporation from 1994 until that company merged with Bell Atlantic to become Verizon. During his corporate tenure, Barr directed a successful litigation campaign by the local telephone industry to achieve deregulation by scuttling a series of FCC rules, personally arguing several cases in the federal courts of appeals and the Supreme Court.[12] Barr currently serves with several corporate boards.[citation needed]
In his adopted home state of Virginia, Barr was appointed during 1994 by then-Governor George Allen to co-chair a commission to reform the criminal justice system and abolish parole in the state.[13] He served on the Board of Visitors of the College of William & Mary in Williamsburg from 1997 to 2005.[14]
He became an independent director of Time Warner (now WarnerMedia) in July 2009.
In 2009, Barr was of counsel to Kirkland & Ellis and joined the firm in 2017.[15]
On December 6, 2018, it was reported that President Donald Trump was considering Barr to be Attorney General.[16][17]
Policy positions
Immigration
As deputy attorney general, Barr successfully challenged a proposed rule by the Department of Health and Human Services to allow people with HIV/AIDS into the United States.[18] He also advocated the use of Guantanamo Bay to prevent Haitian refugees and HIV infected peoples from claiming asylum in the United States.[19]
Crime and security
Social issues
Barr has stated that he believed the constitution was not originally intended to create a right to abortion; that Roe v. Wade was thus wrongly decided; and that abortion should be a “legitimate issue for state legislators”.[8]
Health care reform
Energy and environment
Executive power
Personal life
Barr is an avid bagpiper, an avocation he began at age 8, and has played competitively in Scotland with a major American pipe band; he was a member for some time of the City of Washington Pipe Band.[20]
Barr is a Roman Catholic. He married Christine Moynihan in June 1973, and they have three grown daughters. He is a resident of Virginia.[citation needed]
References …
https://en.wikipedia.org/wiki/William_P._Barr
Story 4: United States Net Oil Exporter — First Time Since 1949 — Videos
OPEC set to curb oil supply? | DW News
The US Is Making Its Mark On The Global Oil Market, But How Long Will It Last?
Study: US Could Be a Net Energy Exporter
Analysts: OPEC Meeting in Vienna to Result in Less Production
The U.S. Just Became a Net Oil Exporter for the First Time in 75 Years
By Javier BlasAmerica turned into a net oil exporter last week, breaking 75 years of continued dependence on foreign oil and marking a pivotal — even if likely brief — moment toward what U.S. President Donald Trump has branded as “energy independence.”
The shift to net exports is the dramatic result of an unprecedented boom in American oil production, with thousands of wells pumping from the Permian region of Texas and New Mexico to the Bakken in North Dakota to the Marcellus in Pennsylvania.
While the country has been heading in that direction for years, this week’s dramatic shift came as data showed a sharp drop in imports and a jump in exports to a record high. Given the volatility in weekly data, the U.S. will likely remain a small net importer most of the time.
“We are becoming the dominant energy power in the world,” said Michael Lynch, president of Strategic Energy & Economic Research. “But, because the change is gradual over time, I don’t think it’s going to cause a huge revolution, but you do have to think that OPEC is going to have to take that into account when they think about cutting.”
The shale revolution has transformed oil wildcatters into billionaires and the U.S. into the world’s largest petroleum producer, surpassing Russia and Saudi Arabia. The power of OPEC has been diminished, undercutting one of the major geopolitical forces of the last half century. The cartel and its allies are meeting in Vienna this week, trying to make a tough choice to cut output and support prices, risking the loss of more market share to the U.S.
American Oil Renaissance
U.S. net imports of crude oil and refined petroleum products
Sources: 1918-1948 courtesy of Michael Lynch and adapted from American Petroleum Institute’s ‘Petroleum Facts and Figures 1959’; for 1949-2017 U.S. EIA ‘Monthly Energy Review’. 2018 and 2019 are forecast from the EIA.
The U.S. sold overseas last week a net 211,000 barrels a day of crude and refined products such as gasoline and diesel, compared to net imports of about 3 million barrels a day on average so far in 2018, and an annual peak of more than 12 million barrels a day in 2005, according to the U.S. Energy Information Administration.
The EIA said the U.S. has been a net oil importer in weekly data going back to 1991 and monthly data starting in 1973. Oil historians that have compiled even older annual data using statistics from the American Petroleum Institute said the country has been a net oil importer since 1949, when Harry Truman was at the White House.
U.S. crude exports are poised to rise even further, with new pipelines from the Permian in the works and at least nine terminals planned that will be capable of loading supertankers. The only facility currently able to load the largest ships, the Louisiana Offshore Oil Port, is on pace to load more oil in December than it has in any other month.
The massive Permian may be even bigger than previously thought. The Delaware Basin, the less drilled part of the field, holds more than twice the amount of crude as its sister, the Midland Basin, the U.S. Geological Service said Thursday.
While the net balance shows the U.S. is selling more petroleum than buying, American refiners continue to buy millions of barrels each day of overseas crude and fuel. The U.S. imports more than 7 million barrels a day of crude from all over the globe to help feed its refineries, which consume more than 17 million barrels each day. In turn, the U.S. has become the world’s top fuel supplier.
“The U.S. is now a major player in the export market,” said Brian Kessens, who helps manage $16 billion at Tortoise in Leawood, Kansas. “We continue to re-tool our export infrastructure along the Gulf Coast to expand capacity, and you continue to see strong demand globally for crude oil.”
— With assistance by Jessica Summers
https://www.bloomberg.com/news/articles/2018-12-06/u-s-becomes-a-net-oil-exporter-for-the-first-time-in-75-years
The Pronk Pops Show Podcasts Portfolio
Listen To Pronk Pops Podcast or Download Shows 1182-1183
Listen To Pronk Pops Podcast or Download Shows 1174-1181
Listen To Pronk Pops Podcast or Download Shows 1168-1173
Listen To Pronk Pops Podcast or Download Shows 1159-1167
Listen To Pronk Pops Podcast or Download Shows 1151-1158
Listen To Pronk Pops Podcast or Download Shows 1145-1150
Listen To Pronk Pops Podcast or Download Shows 1139-1144
Listen To Pronk Pops Podcast or Download Shows 1131-1138
Listen To Pronk Pops Podcast or Download Shows 1122-1130
Listen To Pronk Pops Podcast or Download Shows 1112-1121
Listen To Pronk Pops Podcast or Download Shows 1101-1111
Listen To Pronk Pops Podcast or Download Shows 1091-1100
Listen To Pronk Pops Podcast or Download Shows 1082-1090
Listen To Pronk Pops Podcast or Download Shows 1073-1081
Listen To Pronk Pops Podcast or Download Shows 1066-1073
Listen To Pronk Pops Podcast or Download Shows 1058-1065
Listen To Pronk Pops Podcast or Download Shows 1048-1057
Listen To Pronk Pops Podcast or Download Shows 1041-1047
Listen To Pronk Pops Podcast or Download Shows 1033-1040
Listen To Pronk Pops Podcast or Download Shows 1023-1032
Listen To Pronk Pops Podcast or Download Shows 1017-1022
Listen To Pronk Pops Podcast or Download Shows 1010-1016
Listen To Pronk Pops Podcast or Download Shows 1001-1009
Listen To Pronk Pops Podcast or Download Shows 993-1000
Listen To Pronk Pops Podcast or Download Shows 984-992
Listen To Pronk Pops Podcast or Download Shows 977-983
Listen To Pronk Pops Podcast or Download Shows 970-976
Listen To Pronk Pops Podcast or Download Shows 963-969
Listen To Pronk Pops Podcast or Download Shows 955-962
Listen To Pronk Pops Podcast or Download Shows 946-954
Listen To Pronk Pops Podcast or Download Shows 938-945
Listen To Pronk Pops Podcast or Download Shows 926-937
Listen To Pronk Pops Podcast or Download Shows 916-925
Listen To Pronk Pops Podcast or Download Shows 906-915
Listen To Pronk Pops Podcast or Download Shows 889-896
Listen To Pronk Pops Podcast or Download Shows 884-888
Listen To Pronk Pops Podcast or Download Shows 878-883
Listen To Pronk Pops Podcast or Download Shows 870-877
Listen To Pronk Pops Podcast or Download Shows 864-869
Listen To Pronk Pops Podcast or Download Shows 857-863
Listen To Pronk Pops Podcast or Download Shows 850-856
Listen To Pronk Pops Podcast or Download Shows 845-849
Listen To Pronk Pops Podcast or Download Shows 840-844
Listen To Pronk Pops Podcast or Download Shows 833-839
Listen To Pronk Pops Podcast or Download Shows 827-832
Listen To Pronk Pops Podcast or Download Shows 821-826
Listen To Pronk Pops Podcast or Download Shows 815-820
Listen To Pronk Pops Podcast or Download Shows 806-814
Listen To Pronk Pops Podcast or Download Shows 800-805
Listen To Pronk Pops Podcast or Download Shows 793-799
Listen To Pronk Pops Podcast or Download Shows 785-792
Listen To Pronk Pops Podcast or Download Shows 777-784
Listen To Pronk Pops Podcast or Download Shows 769-776
Listen To Pronk Pops Podcast or Download Shows 759-768
Listen To Pronk Pops Podcast or Download Shows 751-758
Listen To Pronk Pops Podcast or Download Shows 745-750
Listen To Pronk Pops Podcast or Download Shows 738-744
Listen To Pronk Pops Podcast or Download Shows 732-737
Listen To Pronk Pops Podcast or Download Shows 727-731
Listen To Pronk Pops Podcast or Download Shows 720-726
Listen To Pronk Pops Podcast or Download Shows 713-719
Listen To Pronk Pops Podcast or Download Shows 705-712
Listen To Pronk Pops Podcast or Download Shows 695-704
Listen To Pronk Pops Podcast or Download Shows 685-694
Listen To Pronk Pops Podcast or Download Shows 675-684
Listen To Pronk Pops Podcast or Download Shows 668-674
Listen To Pronk Pops Podcast or Download Shows 660-667
Listen To Pronk Pops Podcast or Download Shows 651-659
Listen To Pronk Pops Podcast or Download Shows 644-650
Listen To Pronk Pops Podcast or Download Shows 637-643
Listen To Pronk Pops Podcast or Download Shows 629-636
Listen To Pronk Pops Podcast or Download Shows 617-628
Listen To Pronk Pops Podcast or Download Shows 608-616
Listen To Pronk Pops Podcast or Download Shows 599-607
Listen To Pronk Pops Podcast or Download Shows 590-598
Listen To Pronk Pops Podcast or Download Shows 585- 589
Listen To Pronk Pops Podcast or Download Shows 575-584
Listen To Pronk Pops Podcast or Download Shows 565-574
Listen To Pronk Pops Podcast or Download Shows 556-564
Listen To Pronk Pops Podcast or Download Shows 546-555
Listen To Pronk Pops Podcast or Download Shows 538-545
Listen To Pronk Pops Podcast or Download Shows 532-537
Listen To Pronk Pops Podcast or Download Shows 526-531
Listen To Pronk Pops Podcast or Download Shows 519-525
Listen To Pronk Pops Podcast or Download Shows 510-518
Listen To Pronk Pops Podcast or Download Shows 500-509
Listen To Pronk Pops Podcast or Download Shows 490-499
Listen To Pronk Pops Podcast or Download Shows 480-489
Listen To Pronk Pops Podcast or Download Shows 473-479
Listen To Pronk Pops Podcast or Download Shows 464-472
Listen To Pronk Pops Podcast or Download Shows 455-463
Listen To Pronk Pops Podcast or Download Shows 447-454
Listen To Pronk Pops Podcast or Download Shows 439-446
Listen To Pronk Pops Podcast or Download Shows 431-438
Listen To Pronk Pops Podcast or Download Shows 422-430
Listen To Pronk Pops Podcast or Download Shows 414-421
Listen To Pronk Pops Podcast or Download Shows 408-413
Listen To Pronk Pops Podcast or Download Shows 400-407
Listen To Pronk Pops Podcast or Download Shows 391-399
Listen To Pronk Pops Podcast or Download Shows 383-390
Listen To Pronk Pops Podcast or Download Shows 376-382
Listen To Pronk Pops Podcast or Download Shows 369-375
Listen To Pronk Pops Podcast or Download Shows 360-368
Listen To Pronk Pops Podcast or Download Shows 354-359
Listen To Pronk Pops Podcast or Download Shows 346-353
Listen To Pronk Pops Podcast or Download Shows 338-345
Listen To Pronk Pops Podcast or Download Shows 328-337
Listen To Pronk Pops Podcast or Download Shows 319-327
Listen To Pronk Pops Podcast or Download Shows 307-318
Listen To Pronk Pops Podcast or Download Shows 296-306
Listen To Pronk Pops Podcast or Download Shows 287-295
Listen To Pronk Pops Podcast or Download Shows 277-286
Listen To Pronk Pops Podcast or Download Shows 264-276
Listen To Pronk Pops Podcast or Download Shows 250-263
Listen To Pronk Pops Podcast or Download Shows 236-249
Listen To Pronk Pops Podcast or Download Shows 222-235
Listen To Pronk Pops Podcast or Download Shows 211-221
Listen To Pronk Pops Podcast or Download Shows 202-210
Listen To Pronk Pops Podcast or Download Shows 194-201
Listen To Pronk Pops Podcast or Download Shows 184-193
Listen To Pronk Pops Podcast or Download Shows 174-183
Listen To Pronk Pops Podcast or Download Shows 165-173
Listen To Pronk Pops Podcast or Download Shows 158-164
Listen To Pronk Pops Podcast or Download Shows 151-157
Listen To Pronk Pops Podcast or Download Shows 143-150
Listen To Pronk Pops Podcast or Download Shows 135-142
Listen To Pronk Pops Podcast or Download Shows 131-134
Listen To Pronk Pops Podcast or Download Shows 124-130
Listen To Pronk Pops Podcast or Download Shows 121-123
Listen To Pronk Pops Podcast or Download Shows 118-120
Listen To Pronk Pops Podcast or Download Shows 113 -117
Listen To Pronk Pops Podcast or Download Show 112
Listen To Pronk Pops Podcast or Download Shows 108-111
Listen To Pronk Pops Podcast or Download Shows 106-108
Listen To Pronk Pops Podcast or Download Shows 104-105
Listen To Pronk Pops Podcast or Download Shows 101-103
Listen To Pronk Pops Podcast or Download Shows 98-100
Listen To Pronk Pops Podcast or Download Shows 94-97
Listen To Pronk Pops Podcast or Download Show 93
Listen To Pronk Pops Podcast or Download Show 92
Listen To Pronk Pops Podcast or Download Show 91
Listen To Pronk Pops Podcast or Download Shows 88-90
Listen To Pronk Pops Podcast or Download Shows 84-87
Listen To Pronk Pops Podcast or Download Shows 79-83
Listen To Pronk Pops Podcast or Download Shows 74-78
Listen To Pronk Pops Podcast or Download Shows 71-73
Listen To Pronk Pops Podcast or Download Shows 68-70
Listen To Pronk Pops Podcast or Download Shows 65-67
Listen To Pronk Pops Podcast or Download Shows 62-64
Listen To Pronk Pops Podcast or Download Shows 58-61
Listen To Pronk Pops Podcast or Download Shows 55-57
Listen To Pronk Pops Podcast or Download Shows 52-54
Listen To Pronk Pops Podcast or Download Shows 49-51
Listen To Pronk Pops Podcast or Download Shows 45-48
Listen To Pronk Pops Podcast or Download Shows 41-44
Listen To Pronk Pops Podcast or Download Shows 38-40
Listen To Pronk Pops Podcast or Download Shows 34-37
Listen To Pronk Pops Podcast or Download Shows 30-33
Listen To Pronk Pops Podcast or Download Shows 27-29
Listen To Pronk Pops Podcast or Download Shows 17-26
Listen To Pronk Pops Podcast or Download Shows 16-22
Listen To Pronk Pops Podcast or Download Shows 10-15
Listen To Pronk Pops Podcast or Download Shows 1-9
 
Read Full Post | Make a Comment ( None so far )